Hackers target critical zero-day vulnerability in PTZ cameras
by nlqip

Hackers are attempting to exploit two zero-day vulnerabilities in PTZOptics pan-tilt-zoom (PTZ) live streaming cameras used in industrial, healthcare, business conferences, government, and courtroom settings.
In April 2024, GreyNoise discovered CVE-2024-8956 and CVE-2024-8957 after its AI-powered threat detection tool, Sift, detected unusual activity on its honeypot network that did not match any known threats.
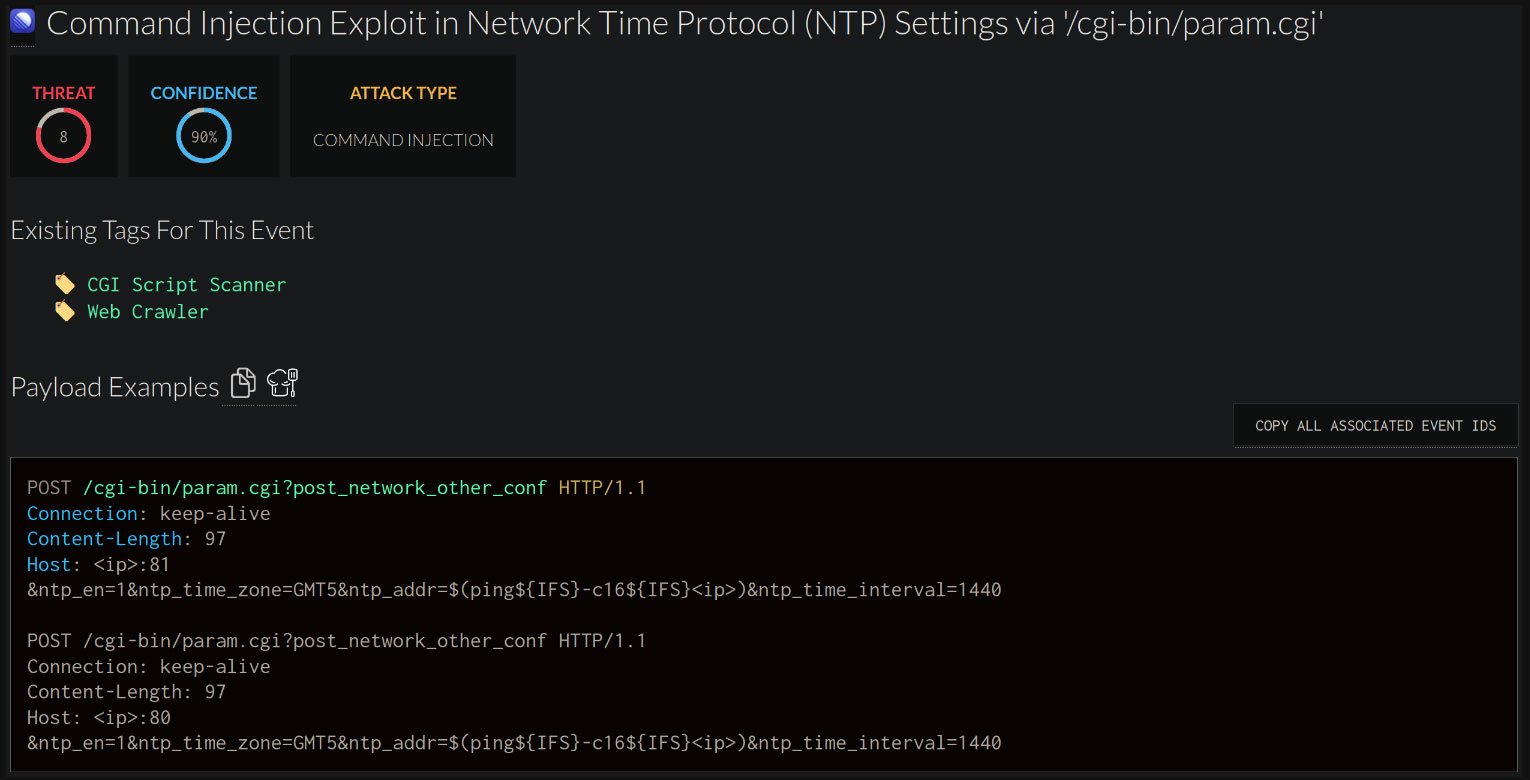
Upon examination of the alert, GreyNoise researchers uncovered an exploit attempt that targeted the camera’s CGI-based API and embedded ‘ntp_client’ aiming to achieve command injection.
A technical deep-dive by GreyNoise researcher Konstantin Lazarev provides more info on the two flaws.
CVE-2024-8956 is a weak authentication problem in the camera’s ‘lighthttpd’ web server, allowing unauthorized users to access the CGI API without an authorization header, which exposes usernames, MD5 password hashes, and network configurations.
CVE-2024-8957 is caused by insufficient input sanitization in the ‘ntp. addr’ field processed by the ‘ntp_client’ binary, allowing attackers to use a specially crafted payload to insert commands for remote code execution.
Greynoise notes that exploitation of these two flaws can lead to complete camera takeover, infection with bots, pivoting to other devices connected on the same network, or disruption of video feeds.
The cybersecurity firm reports that while the source of the initial activity went silent shortly after the honeypot attacks, a separate attempt using wget to download a shell script for reverse shell access was observed in June.
Disclosure and fixing status
Upon discovering CVE-2024-8956 and CVE-2024-8957, GreyNoise worked with VulnCheck for responsible disclosure to impacted vendors.
Source: GreyNoise
Devices impacted by the two flaws are NDI-enabled cameras based on Hisilicon Hi3516A V600 SoC V60, V61, and V63, which run VHD PTZ camera firmware versions older than 6.3.40.
This includes several models from PTZOptics, Multicam Systems SAS cameras, and SMTAV Corporation devices.
PTZOptics released a security update on September 17, but models like the PT20X-NDI-G2 and PT12X-NDI-G2 did not get a firmware update due to having reached end-of-life.
Later, GreyNoise discovered that at least two newer models, PT20X-SE-NDI-G3, and PT30X-SE-NDI-G3, which also didn’t receive a patch, were impacted too.
PTZOptics was notified about the expanded scope through VulnCheck on October 25, but no fixes for these models have been released as of writing.
GreyNoise told BleepingComputer that the flaws likely affect a broad range of camera models.
“We (strongly) believe that a wider range of devices is affected, potentially indicating that the actual culprit lies within the SDK the manufacturer (ValueHD / VHD Corporation) uses,” GreyNoise told BleepingComputer.
That being said, users should check with their device vendor to see if fixes for CVE-2024-8956 and CVE-2024-8957 have been incorporated in the latest available firmware update for their devices.
Source link
lol
Hackers are attempting to exploit two zero-day vulnerabilities in PTZOptics pan-tilt-zoom (PTZ) live streaming cameras used in industrial, healthcare, business conferences, government, and courtroom settings. In April 2024, GreyNoise discovered CVE-2024-8956 and CVE-2024-8957 after its AI-powered threat detection tool, Sift, detected unusual activity on its honeypot network that did not match any known threats. Upon examination of…
