New Ghost Tap attack abuses NFC mobile payments to steal money
by nlqip

Cybercriminals have devised a novel method to cash out from stolen credit card details linked to mobile payment systems such as Apple Pay and Google Pay, dubbed ‘Ghost Tap,’ which relays NFC card data to money mules worldwide.
The tactic builds upon the methods previously deployed by mobile malware like NGate, documented by ESET in August, which involved relaying Near Field Communication (NFC) signals from payment cards.
Ghost Tap is more obfuscated and more challenging to detect, does not require the card or the victim’s device, doesn’t need continual victim interchange, and involves money mules on multiple remote locations interacting with Point of Sale (PoS) terminals.
Mobile security firm Threat Fabric discovered Ghost Tap, which warns about the increasing adoption and potential of the new tactic, telling BleepingComputer it has recently seen a spike in using this tactic in the wild.

Source: Threat Fabric
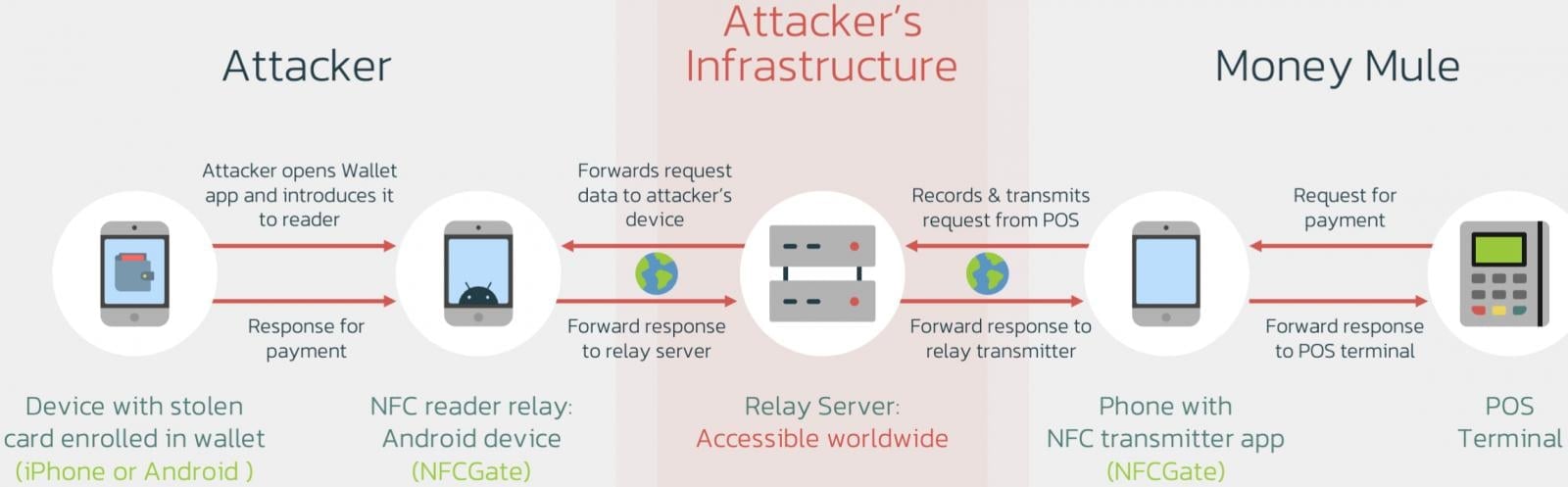
Ghost Tap overview and comparison to NGate
The first step in the attack is to steal the data of payment cards and intercept the one-time passwords (OTP) needed for virtual wallet enrollment on Apple Pay and Google Pay.
Stealing the payment card data can be accomplished through banking malware that displays overlays that mimic digital payment apps or through phishing pages and keylogging. OTPs can be stolen through social engineering or by malware that monitors text messages.
In the previous NGate-based attacks, the victim needed to be tricked into scanning their card using their device’s NFC system using specialized malware that guided them through this process.
The NFCGate tool is still used to relay payment card information. However, a relay server is placed in between now, sending the details to an extensive network of money mules while obfuscating their actual locations.
The mules then perform retail purchases at scale and multiple locations using their device’s NFC chip, making it hard to map the fraud network or trace the primary attacker.
In the NGate attacks, the threat actors were limited to small contactless payments and ATM withdrawals that risked their anonymity and even led to arrests in some cases.
With the new Ghost Taps operation, the threat actors no longer conduct ATM withdrawals. Instead, they only conduct point-of-sale cash outs and spread them among a wide network of mules worldwide.
This obfuscates the trail to the main operators of the malicious activity, only putting the mules at risk.
Source: Threat Fabric
Protecting against Ghost Tap
Threat Fabric warns that the new tactic is challenging for financial institutions to detect and stop as the transactions appear legitimate and span multiple locations.
While many bank’s anti-fraud mechanisms detect purchases from unusual locations, such as when traveling to another country, the researchers say the numerous small payments may bypass these detections.
“The new tactic for cash-outs poses a challenge for financial organisations: the ability of cybercriminals to scale the fraudulent offline purchases, making multiple small payments in different places, might not trigger the anti-fraud mechanisms and might allow cybercriminals to successfully buy goods that can be further re-sold (like gift cards),” explains ThreatFabric.
Even with all these small transactions appearing to come from a single device (tied to the same Apple Pay/Google Pay account), the total amount lost can be significant if the attack is applied at scale.
To evade tracking, the mules put their devices in “airplane mode,” which still allows the NFC system to function as usual.
The only way to defend against Ghost Tap is for banks to flag transactions made from the same card but at locations that are not physically possible to get to in the timeframe between charges. For example, conducting a fraudulent transaction in New York and then ten minutes later, performing one in Cyprus.
From the consumer’s perspective, monitoring for fraudulent transactions and reporting them to your bank immediately is crucial for blocking the card and minimizing the losses.
Source link
lol
Cybercriminals have devised a novel method to cash out from stolen credit card details linked to mobile payment systems such as Apple Pay and Google Pay, dubbed ‘Ghost Tap,’ which relays NFC card data to money mules worldwide. The tactic builds upon the methods previously deployed by mobile malware like NGate, documented by ESET in…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
