Hacker posts fake story about Ukrainians trying to kill Slovak President
by nlqip
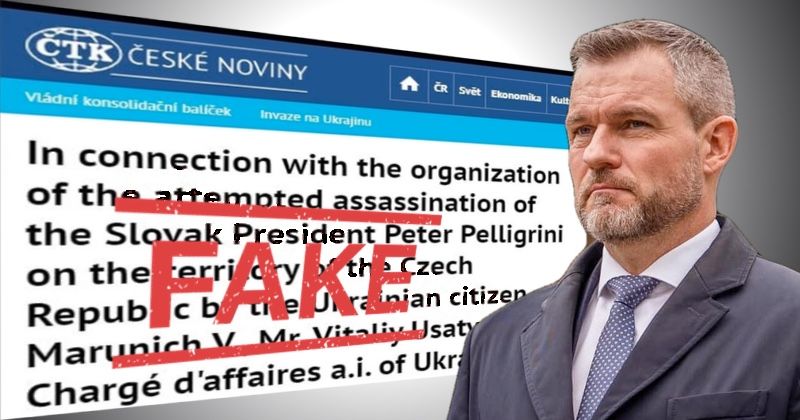
Czech news agency ČTK announced on Tuesday that a hacker had managed to break into its systems and published fake news reports of a plot to murder the president of a neighbouring country.
One of the false stories published by the hacker in Czech and English claimed that Czechia’s security information service (known as BIS) had prevented an assassination attempt against Slovakia’s new president “Peter Pelligrini”
According to the false report planted by the hacker, the plot against the Slovak president’s life was orchestrated by, amongst others, Ukrainian Chargé d’Affaires Vitaliy Usatyy.
A follow-up fake news story published by the hacker on ČTK’s website and mobile app claimed that Czech Foreign Minister Jan Lipavský had commented on the alleged murder plot.
The hacker’s haste in publishing false news led to careless mistakes that tipped off readers to its lack of factual basis.
For instance, the Slovak president’s surname was referred to as “Pelligrini” instead of the correct Pellegrini.
The finger of suspicion is likely to point towards the attack being a deliberate act of disinformation by pro-Kremlin hackers intended to discredit Ukraine as it continues to fight against Russian invaders.
Last year, security researchers described how a hacking group called “Ghostwriter” affiliated with the Belarus government had gained access to media organisations’ content management systems to post false stories.
The ČTK news agency confirmed in a statement on its site that the assassination plot news reports were fake, removed the bogus stories from its website, and blocked the hacker’s access to its content management system.
ČTK said that it was working closely with Czech authorities to investigate the hack, and would not be providing any additional information at this time.
All businesses need to put layers of protection in place to prevent malicious hackers from gaining access to their IT systems. It is essential to tightly control access to internal infrastructure, like media organizations’ content management services, and authenticate users are truly who they say they are.
Security breaches repeatedly show that simply asking users to choose strong, unique passwords and to look out for phishing attacks may not be enough. Additional defenses such as two-factor authentication can help make the breaching of systems much more of a challenge.
Source link
lol
Czech news agency ČTK announced on Tuesday that a hacker had managed to break into its systems and published fake news reports of a plot to murder the president of a neighbouring country. One of the false stories published by the hacker in Czech and English claimed that Czechia’s security information service (known as BIS)…
Recent Posts
- The 10 Hottest Semiconductor Startups Of 2024
- Cybersecurity Snapshot: Prompt Injection and Data Disclosure Top OWASP’s List of Cyber Risks for GenAI LLM Apps
- Healthcare Ransomware Attacks: How to Prevent and Respond Effectively | BlackFog
- Black Friday Versus The Bots
- Over 2,000 Palo Alto firewalls hacked using recently patched bugs
