US Post Office phishing sites get as much traffic as the real one
by nlqip

Security researchers analyzing phishing campaigns that target United States Postal Service (USPS) saw that the traffic to the fake domains is typically similar to what the legitimate site records and it is even higher during holidays.
Phishing operations typically target people’s sensitive information (account credentials, card details) or try to trick users into making payments to fraudulent shops or covering fees supposedly required for clearing items that have been placed on hold for various reasons.
USPS phishing
During the 2023 holiday season, Akamai Technologies observed a significant volume of DNS queries going to “combosquatting” domains that impersonate the USPS service.
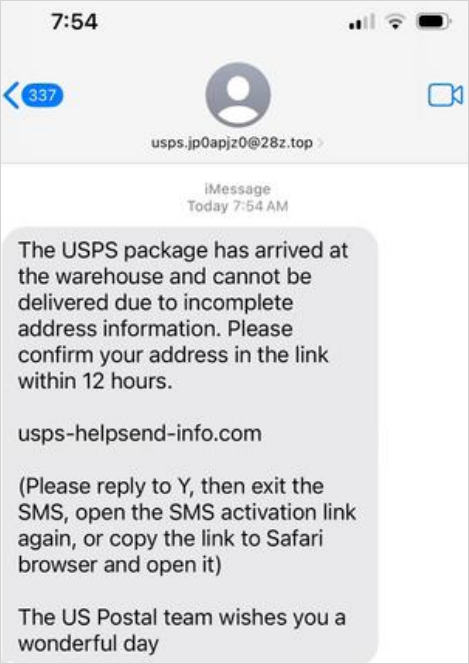
Akamai started investigating USPS-themed phishing in October 2023 after an employee received a suspicious SMS that redirected to a site containing malicious JavaScript code.
Akamai
Next, the analysts compiled a list of all domains using the same JS file from the past five months and kept only those with the USPS string in their name.
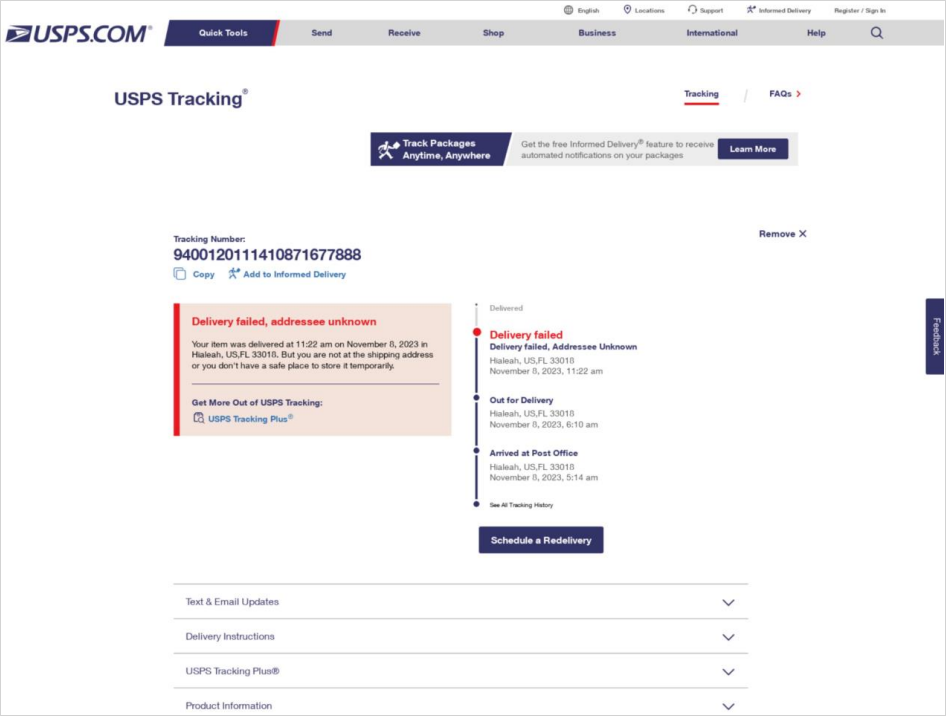
The design of these pages is very convincing and appear as exact replicas of the authentic USPS site with realistic tracking pages for status updates.
Akamai
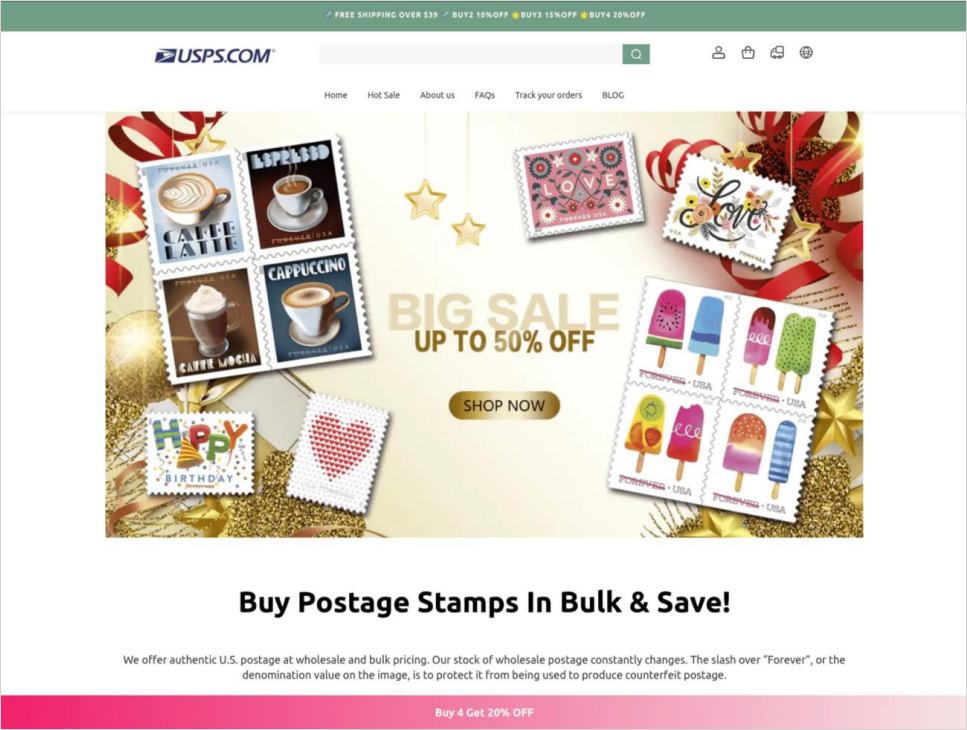
In one case, the phishing actors set up what looks like a dedicated postage items shop, which started getting significant traffic in late November, as consumers sought to buy gifts and collectibles for the holiday season.
Akamai
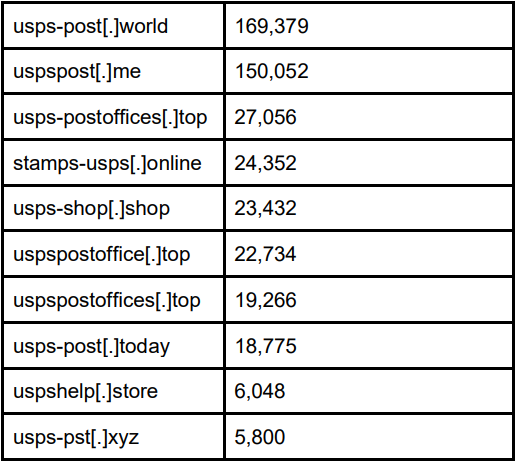
From October 2023 to February 2024, the most popular malicious domains that Akamai discovered received nearly half a million queries, with two surpassing 150k each.
Akamai
The most popular top-level domains (TLDs) associated with phishing USPS-themed domains were:
- .com – 4459 domains and 271,278 queries
- .top – 3,063 domains and 274,257 queries
- .shop – 566 domains and 58,194 queries
- .xyz – 397 domains and 30,870 queries
- .org – 352 domains and 16,391 queries
- .info – 257 domains and 7,597 queries
The total queries generated by all malicious websites uncovered by Akamai’s research during the examined period is over 1,128,146, just short of the 1,181,235 queries recorded for the legitimate USPS site.
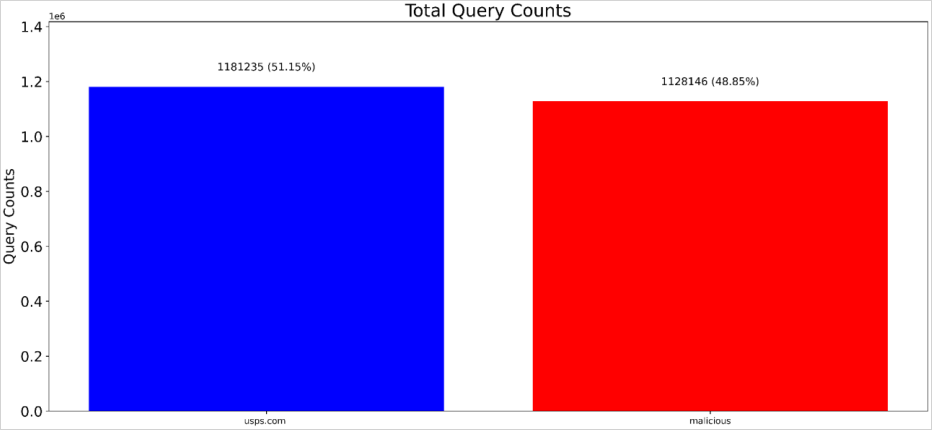
Akamai
However, the stats show that traffic to malicious domains between November to December was higher compared to the legitimate one, indicating increased malicious activity during winter holiday season.
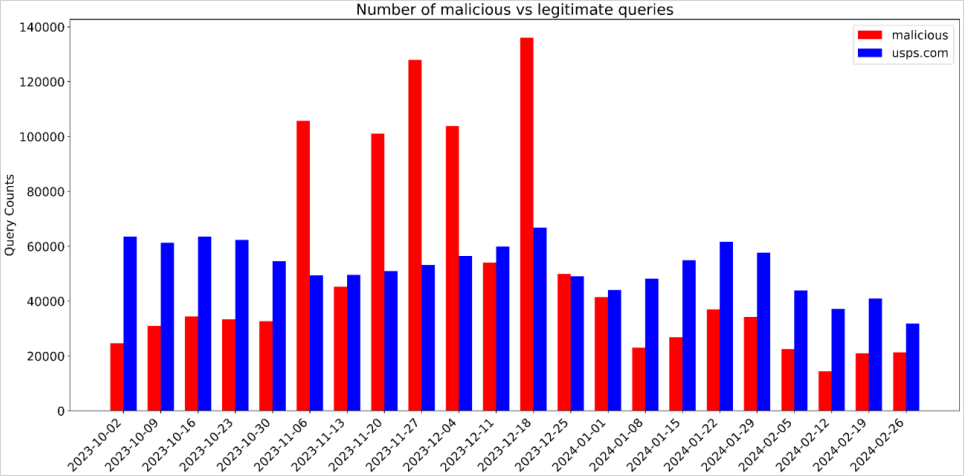
Akamai
Akamai only focused this research on USPS, so the actual scale of these combosquatting campaigns that potentially encompass many more brands is likely larger.
Consumers should exercise caution and be skeptic about any SMS or email messages about package shipments.
To verify the legitimacy of such communications, it’s advisable to use the official website (by manually loading it in the browser) to check the delivery status of a product.
Clicking on the links included in messages for tracking parcels may lead to malicious locations.
Source link
lol
Security researchers analyzing phishing campaigns that target United States Postal Service (USPS) saw that the traffic to the fake domains is typically similar to what the legitimate site records and it is even higher during holidays. Phishing operations typically target people’s sensitive information (account credentials, card details) or try to trick users into making payments…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
