Lockbit’s seized site comes alive to tease new police announcements
by nlqip

The NCA, FBI, and Europol have revived a seized LockBit ransomware data leak site to hint at new information being revealed by law enforcement this Tuesday.
On February 19, a law enforcement operation called Operation Cronos took down LockBit’s infrastructure, including 34 servers hosting the data leak website and its mirrors, data stolen from the victims, cryptocurrency addresses, 1,000 decryption keys, and the affiliate panel.
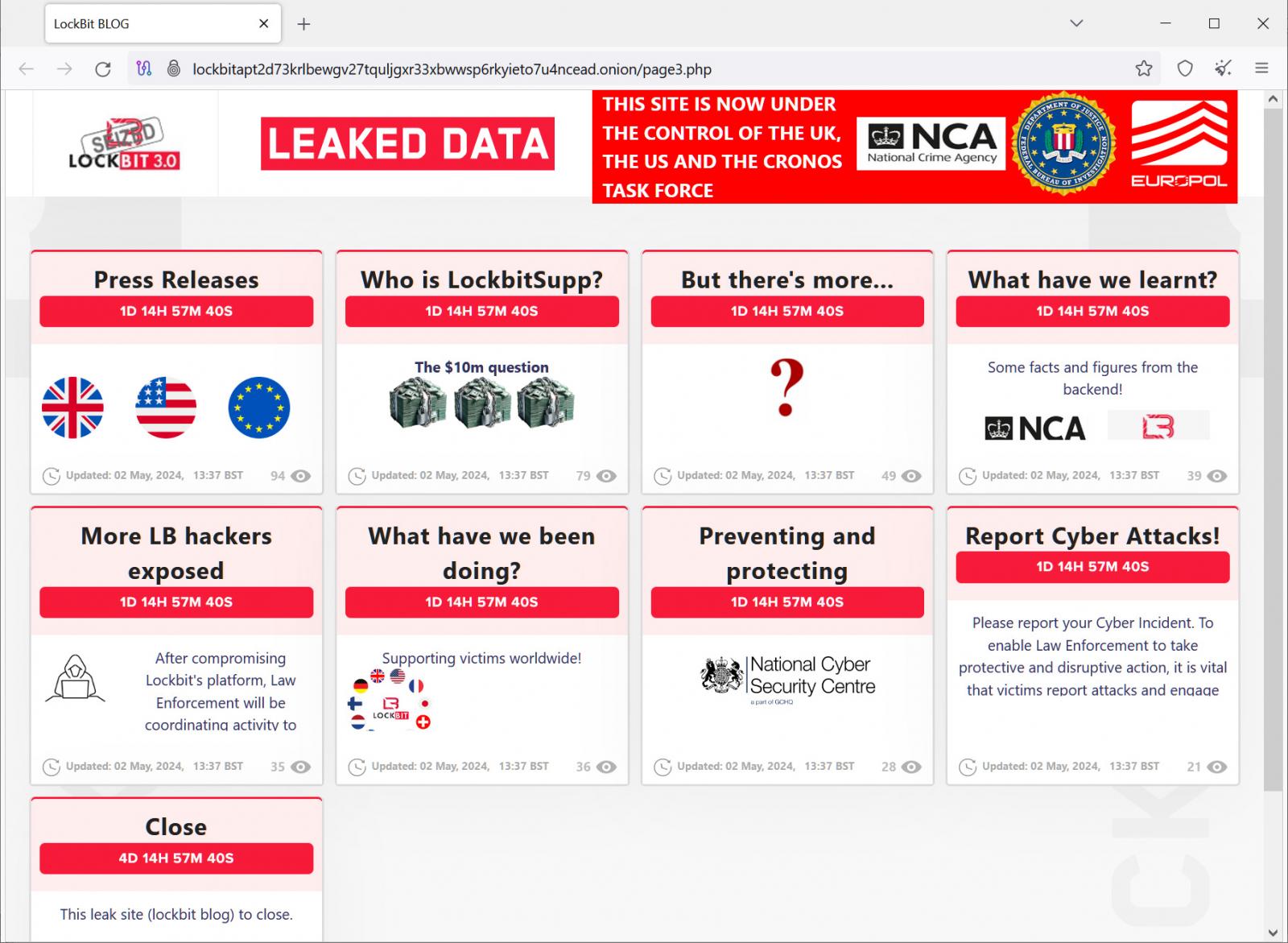
As part of this disruption, the police converted one of the data leak sites into a press release site, where the UK’s National Crime Agency (NCA), the FBI, and Europol shared information about what they learned during the operation, a list of affiliates, and how LockBit lies to victims by not always deleting stolen data after a ransom is paid.
One of the announcements had the title “Who is LockBitSupp?” hinting that law enforcement would reveal information about who was running the ransomware operation.
However, after days of waiting, the blog post simply stated, “We know who he is. We know where he lives. We know how much he is worth. LockBitSupp has engaged with Law Enforcement :).”
Law enforcement eventually shut down the website a few days later, with many seeing the “LockBitSupp” post as a blunder by law enforcement for hyping the announcement and revealing nothing and a win for LockBitSupp, who continued to remain anonymous.
On Sunday, international law enforcement revived LockBit’s data leak/press release site, this time with seven new blog posts that are all going live at the same time, on Tuesday at 14:00:00 UTC (2 PM EST).
Source: BleepingComputer
These blog posts tease titles like “What have we learnt?,” “More LB hackers exposed,” “What have we been doing?,” and what many hope to be the coup de grâce on the diminished ransomware operation, another blog post titled “Who is LockBitSupp?”.
For now, we will have to wait to see if law enforcement will actually reveal anything substantial about LockBit’s operator or if this is once again going to be a letdown.
Since the law enforcement operation, LockBit has been struggling to return to prior activity levels, with affiliates having become wary that the operation is now compromised and being watched too closely by law enforcement.
However, that does not mean the ransomware gang is finished, as disruptive attacks continue and the operation is still a risk to the enterprise worldwide.
Source link
lol
The NCA, FBI, and Europol have revived a seized LockBit ransomware data leak site to hint at new information being revealed by law enforcement this Tuesday. On February 19, a law enforcement operation called Operation Cronos took down LockBit’s infrastructure, including 34 servers hosting the data leak website and its mirrors, data stolen from the victims, cryptocurrency…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
