Over 50,000 Tinyproxy servers vulnerable to critical RCE flaw
by nlqip

Nearly 52,000 internet-exposed Tinyproxy instances are vulnerable to CVE-2023-49606, a recently disclosed critical remote code execution (RCE) flaw.
Tinyproxy is an open-source HTTP and HTTPS proxy server designed to be fast, small, and lightweight. It is specifically tailored for UNIX-like operating systems and is commonly used by small businesses, public WiFi providers, and home users.
At the start of the month, Cisco Talos disclosed CVE-2023-49606, a critical (CVSS v3: 9.8) use-after-free flaw the researchers discovered in December 2023, impacting versions 1.11.1 (latest) and 1.10.0, after claiming to not receiving a response from the developers.
Cisco’s report shared detailed information about the vulnerability, including proof-of-concept exploits that crashed the server and could potentially lead to remote code execution.
Talos researchers explained in the report that the flaw occurs in the ‘remove_connection_headers()’ function, where specific HTTP headers (Connection and Proxy-Connection) are not correctly managed, leading to memory being freed and then incorrectly accessed again.
This can be easily exploited with a simple malformed HTTP request (e.g., Connection: Connection) without requiring authentication.
Cisco warned at the time that despite its efforts to alert Tinyproxy’s developers of the critical flaw, it received no response, and no patch was available for users to download.
On Saturday, Censys reported seeing 90,000 internet-exposed Tinyproxy services online, of which about 57% were vulnerable to CVE-2023-49606.
Specifically, Censys found 18,372 instances running the vulnerable version 1.11.1 and another 1,390 running on 1.10.0.
Most of these instances are located in the United States (11,946), followed by South Korea (3,732), China (675), France (300), and Germany (150).
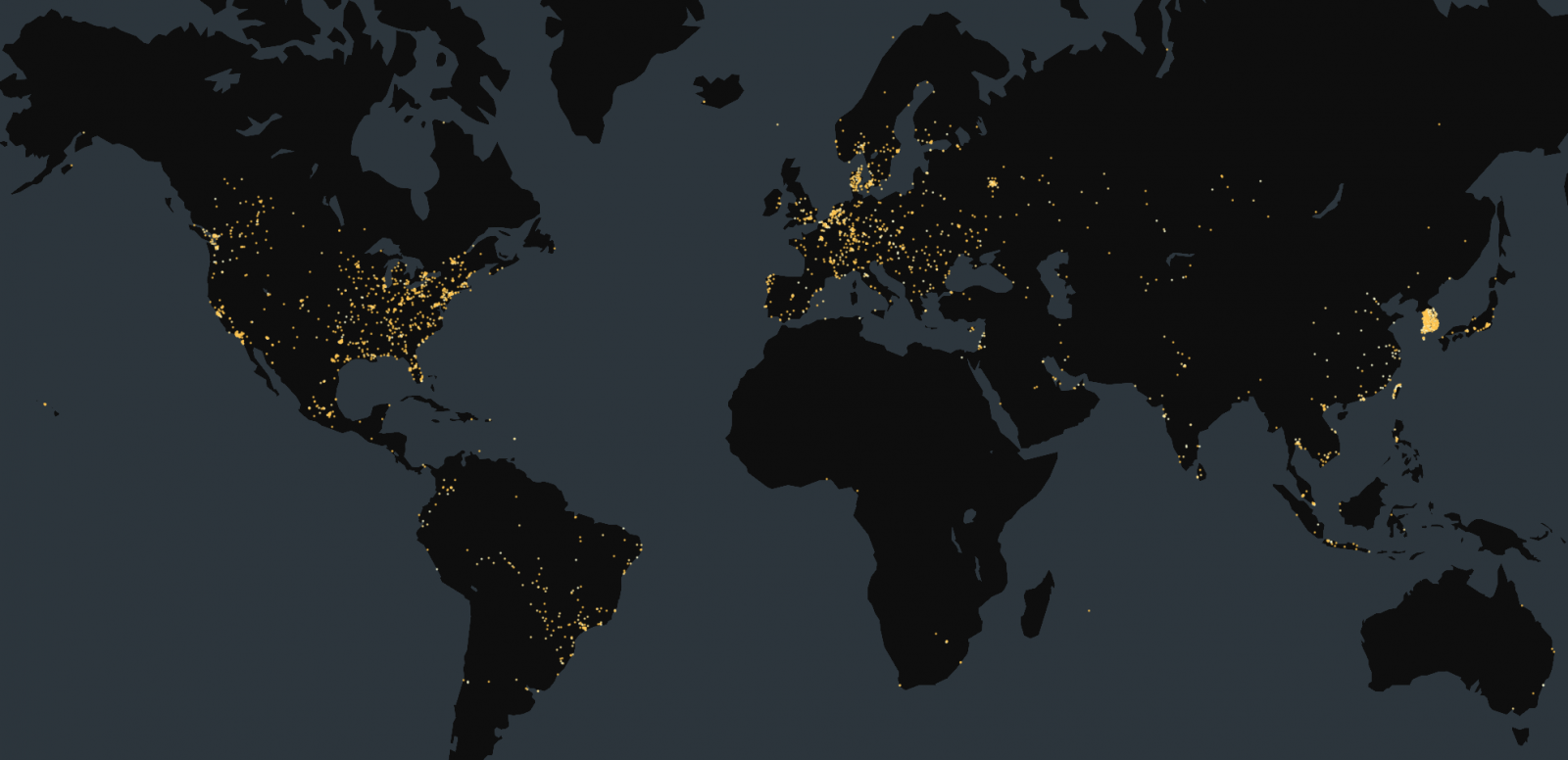
Source: Censys
Flaw fixed
On Sunday, five days after Cisco disclosed the bug, the maintainers of Tinyproxy released a fix for CVE-2023-49606, which adjusts memory management as needed to prevent exploitation.
However, the Tinyproxy maintainer disputed that Cisco properly disclosed the bug, stating they never received the report via the project’s requested disclosure channels.
“A security researcher from TALOS intelligence found a use-after-free vulnerability in tinyproxy in december 2023, claiming to have contacted upstream and waited 6 months for publication,” noted the developers on GitHub
“Whatever he did to contact upstream, it wasn’t effective and not what was described on either the tinyproxy homepage nor in README.md.”
“He certainly didn’t try hard to find a responsive contact, and probably pulled a random email address out of git log and sent a mail there. The vulnerability was made public on may 01 2024, and it took a full 5 days until i was notified on IRC by a distro package maintainer.”
The commit (12a8484) containing the security fix is in the upcoming version 1.11.2, but people in urgent need can pull the change from the master branch or manually apply the highlighted fix.
“This is a quite nasty bug, and could potentially lead to RCE – though i haven’t seen a working exploit yet,” continued the Tinyproxy maintainers.
“What it certainly allows is a DOS attack on the server if tinyproxy is either using musl libc 1.2+ – whose hardened memory allocator automatically detects UAF, or built with an address sanitizer.”
The developers also noted that the updated code only triggers after passing authentication and access list checks, meaning the vulnerability might not affect all setups, especially those within controlled environments like corporate networks or those using basic authentication with secure passwords.
Source link
lol
Nearly 52,000 internet-exposed Tinyproxy instances are vulnerable to CVE-2023-49606, a recently disclosed critical remote code execution (RCE) flaw. Tinyproxy is an open-source HTTP and HTTPS proxy server designed to be fast, small, and lightweight. It is specifically tailored for UNIX-like operating systems and is commonly used by small businesses, public WiFi providers, and home users. At the…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
