Volatile Data Acquisition on Linux Systems Using fmem
by nlqip

The content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article.
Memory forensics is a critical aspect of digital forensics, allowing investigators to analyze the volatile memory of a system to uncover evidence of malicious activity, detect hidden malware, and reconstruct system events. In this blog, we’ll explore the world of memory forensics using two powerful tools: Fmem and LiME. We’ll delve into the basics of memory forensics, explore the features and capabilities of Fmem and LiME, and provide a step-by-step guide on how to use these tools to analyze a memory dump.
What is Memory Forensics?
Memory forensics involves the analysis of a system’s volatile memory to extract valuable information about system state, running processes, and network connections. This type of analysis is crucial in incident response, malware analysis, and digital forensics investigations. By analysing memory, investigators can:
1. Detect Hidden Malware and Rootkits:
Memory forensics enables investigators to uncover hidden malware and rootkits that may be actively running in a system’s memory. Unlike traditional antivirus software that primarily scans the file system, memory forensics tools can identify malicious code and processes that attempt to evade detection by residing solely in memory.
2. Identify Malicious Processes and Network Connections:
By analyzing the contents of a system’s memory, forensic analysts can identify suspicious processes and network connections. This includes processes that may be performing malicious activities such as data exfiltration, privilege escalation, or network reconnaissance. Identifying these malicious entities is crucial for understanding the scope and impact of a security incident.
3. Reconstruct System Events and Timelines:
Memory forensics allows investigators to reconstruct the sequence of events that occurred on a system leading up to and during a security incident. By analyzing memory artifacts such as process creation timestamps, network connection logs, and registry modifications stored in memory, investigators can create a detailed timeline of activities, which aids in understanding the tactics and techniques employed by attackers.
4. Extract Sensitive Data:
Volatile data, such as passwords, encryption keys, and other sensitive information, may be present in a system’s memory during normal operation. Memory forensics tools can extract this data from memory dumps, providing valuable evidence for digital investigations. This information can be crucial for understanding how attackers gained access to sensitive resources and for mitigating potential security risks.
Using fmem for Memory Capture:
fmem is a kernel module that creates a virtual device, /dev/fmem, which allows direct access to the physical memory of a system. This module is particularly useful for acquiring memory dumps of a compromised system, even if the system is protected by Secure Boot or has disabled the ability to read physical memory directly.
Follow these steps to capture memory using fmem: Download the fmem source code from the official repository or package manager. The same can be found here.
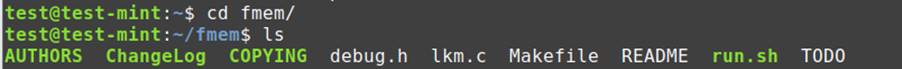
Once cloned into the repository, change directory to fmem using cd command. You can use ls command to list the contents of the directory.
Compile and install fmem on the target Linux system:
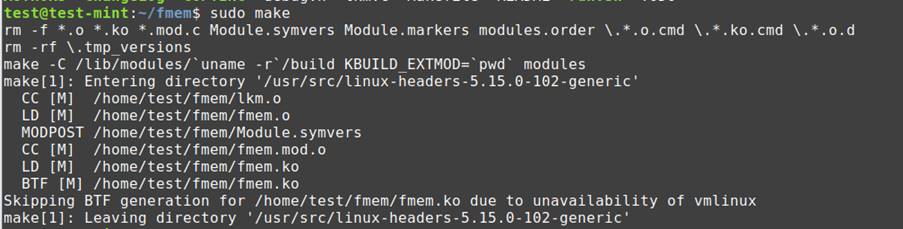
Once you are in fmem directory, use command “sudo make” to build all the necessary libraries associated with fmem from the source code.
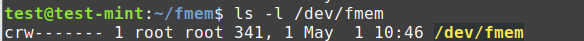
Check if the /dev/fmem device has been created using the following command: ls -l /dev/fmem
You should see something like this:
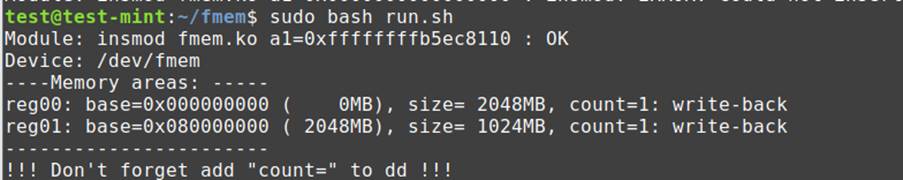
Now, to install fmem, we have to run the bash script in fmem directory. To use the same you can use sudo bash run.sh or sudo ./run.sh
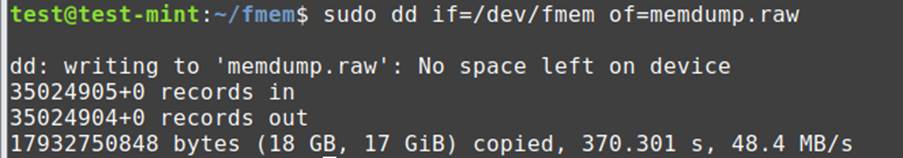
Now to acquire the memory dump, you can use a tool like dd. Use the following command: sudo dd if=/dev/fmem of=memdump.raw
Once executed, it may take some time to complete the acquisition of memory depending on RAM size. After the completion it shall show you a dialog box like this. You can also use other commands specifying buffersize, dd if=/dev/fmem of=/home/”username”/memdump.dd bs=1MB
Once you have acquired the memory dump, you can analyze it using LiME or other memory forensics tools. In our next blog, we’ll explore how to analyze the memory dump using LiME.
Source link
lol
The content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. Memory forensics is a critical aspect of digital forensics, allowing investigators to analyze the volatile memory of a system to uncover evidence of…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA