Cylance confirms data breach linked to ‘third-party’ platform
by nlqip

Cybersecurity company Cylance confirmed the legitimacy of data being sold on a hacking forum, stating that it is old data stolen from a “third-party platform.”
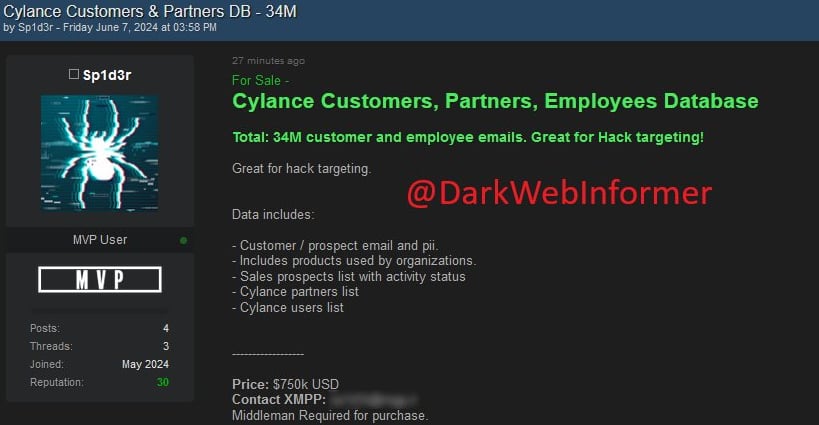
A threat actor known as Sp1d3r is selling this stolen data for $750,000, as first spotted by Dark Web Informer.
The data allegedly includes a substantial amount of information, such as 34,000,000 customer and employee emails and personally identifiable information belonging to Cylance customers, partners, and employees.
However, researchers have told BleepingComputer that the leaked samples appear to be old marketing data used by Cylance.
BlackBerry Cylance told BleepingComputer that they’re aware of and investigating the threat actor’s claims but that no “BlackBerry data and systems related to [..] customers, products, and operations have been compromised.”
“Based on our initial reviews of the data in question, no current Cylance customers are impacted, and no sensitive information is involved,” the company added.
“The data in question was accessed from a third-party platform unrelated to BlackBerry and appears to be from 2015-2018, predating BlackBerry’s acquisition of the Cylance product portfolio.”
Links to Snowflake attacks
While the company has yet to reply to a follow-up request for more details regarding the name of the third-party platform that was breached to steal what it claims to be old data, the same threat actor is also selling 3TB of data from automotive aftermarket parts provider Advance Auto Parts, stolen after breaching the company’s Snowflake account.
BleepingComputer confirmed that Cylance is a Snowflake customer, with the web management console located at https://cylance.snowflakecomputing.com/.
Recent breaches at Santander, Ticketmaster, and QuoteWizard/Lendingtree have also been linked to Snowflake attacks. Ticketmaster’s parent company, Live Nation, also confirmed that a data breach had affected the ticketing firm after its Snowflake account was compromised on May 20.
In a joint advisory with CrowdStrike and Mandiant, Snowflake said that attackers had used stolen customer credentials to target accounts without multi-factor authentication protection.
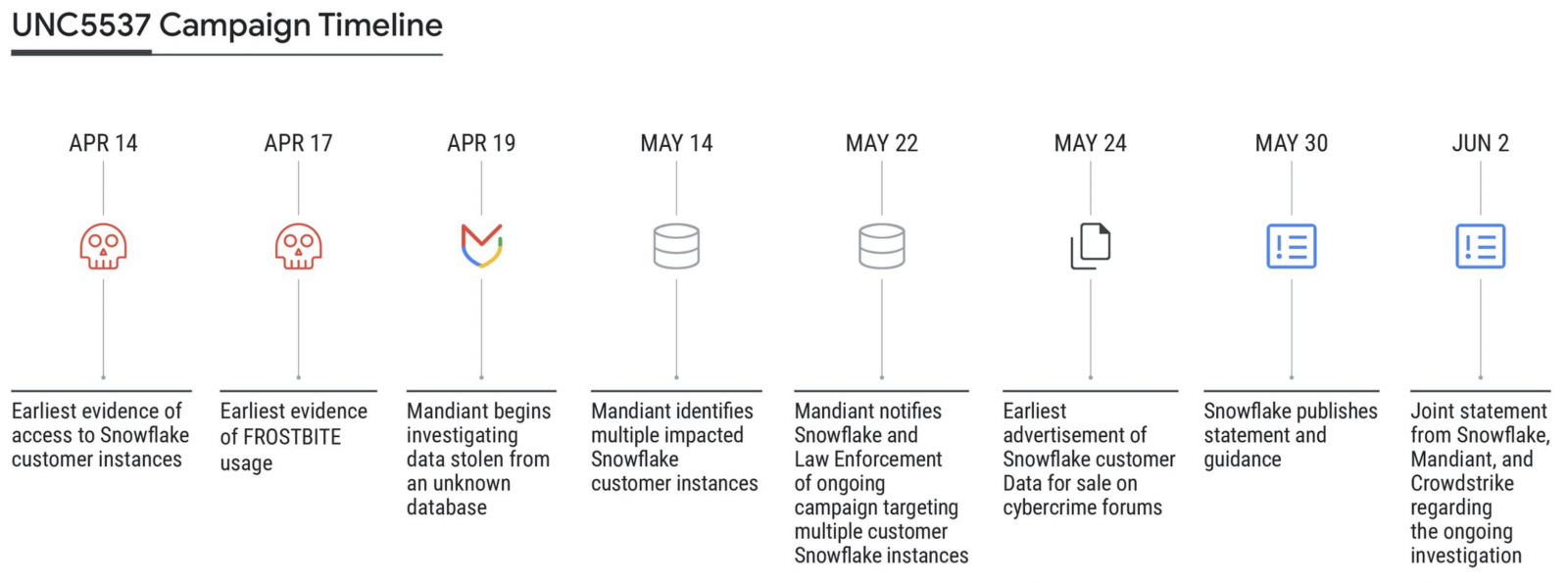
Today, Mandiant published a report linking the Snowflake attacks to a financially motivated threat actor it tracks as UNC5537. The actor gained access to Snowflake customer accounts using customer credentials stolen in infostealer malware infections from as far back as 2020.
Mandiant has been tracking the UNC5537 since May 2024. The financially motivated threat actor has targeted hundreds of organizations worldwide, extorting victims for financial gain.
While Mandiant has not shared much information about UNC5537, BleepingComputer has learned they are part of a larger community of threat actors who frequent the same websites, Telegram, and Discord servers, where they commonly collaborate on attacks.
“The impacted accounts were not configured with multi-factor authentication enabled, meaning successful authentication only required a valid username and password,” Mandiant said.
“Credentials identified in infostealer malware output were still valid, in some cases years after they were stolen, and had not been rotated or updated. The impacted Snowflake customer instances did not have network allow lists in place to only allow access from trusted locations.”
Mandiant says it has identified hundreds of customer Snowflake credentials exposed in Vidar, RisePro, Redline, Racoon Stealer, Lumm, and Metastealer infostealer malware attacks since at least 2020.
To date, Snowflake and Mandiant have notified around 165 organizations potentially exposed to these ongoing attacks.
Source link
lol
Cybersecurity company Cylance confirmed the legitimacy of data being sold on a hacking forum, stating that it is old data stolen from a “third-party platform.” A threat actor known as Sp1d3r is selling this stolen data for $750,000, as first spotted by Dark Web Informer. The data allegedly includes a substantial amount of information, such…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
