ONNX phishing service targets Microsoft 365 accounts at financial firms
by nlqip

A new phishing-as-a-service (PhaaS) platform called ONNX Store is targeting Microsoft 365 accounts for employees at financial firms using QR codes in PDF attachments.
The platform can target both Microsoft 365 and Office 365 email accounts and operates via Telegram bots and features two-factor authentication (2FA) bypass mechanisms.
Researchers at EclecticIQ who discovered the activity believe that ONNX is a rebranded version of the Caffeine phishing kit managed by the Arabic-speaking threat actor MRxC0DER.
Mandiant discovered caffeine in October 2022, when the platform targeted Russian and Chinese platforms instead of Western services.
Source: EclecticIQ
ONNX attacks
EclecticIQ observed ONNX attacks in February 2024, distributing phishing emails with PDF attachments containing malicious QR codes that targeted employees at banks, credit union service providers, and private funding firms.
The emails impersonate human resources (HR) departments, using salary updates as lures to open the PDFs, which are themed after Adobe or Microsoft.

Source: EclecticIQ
Scanning the QR code on a mobile device bypasses phishing protections on the targeted organizations, taking victims to phishing pages that mimic the legitimate Microsoft 365 login interface.
Source: EclecticIQ
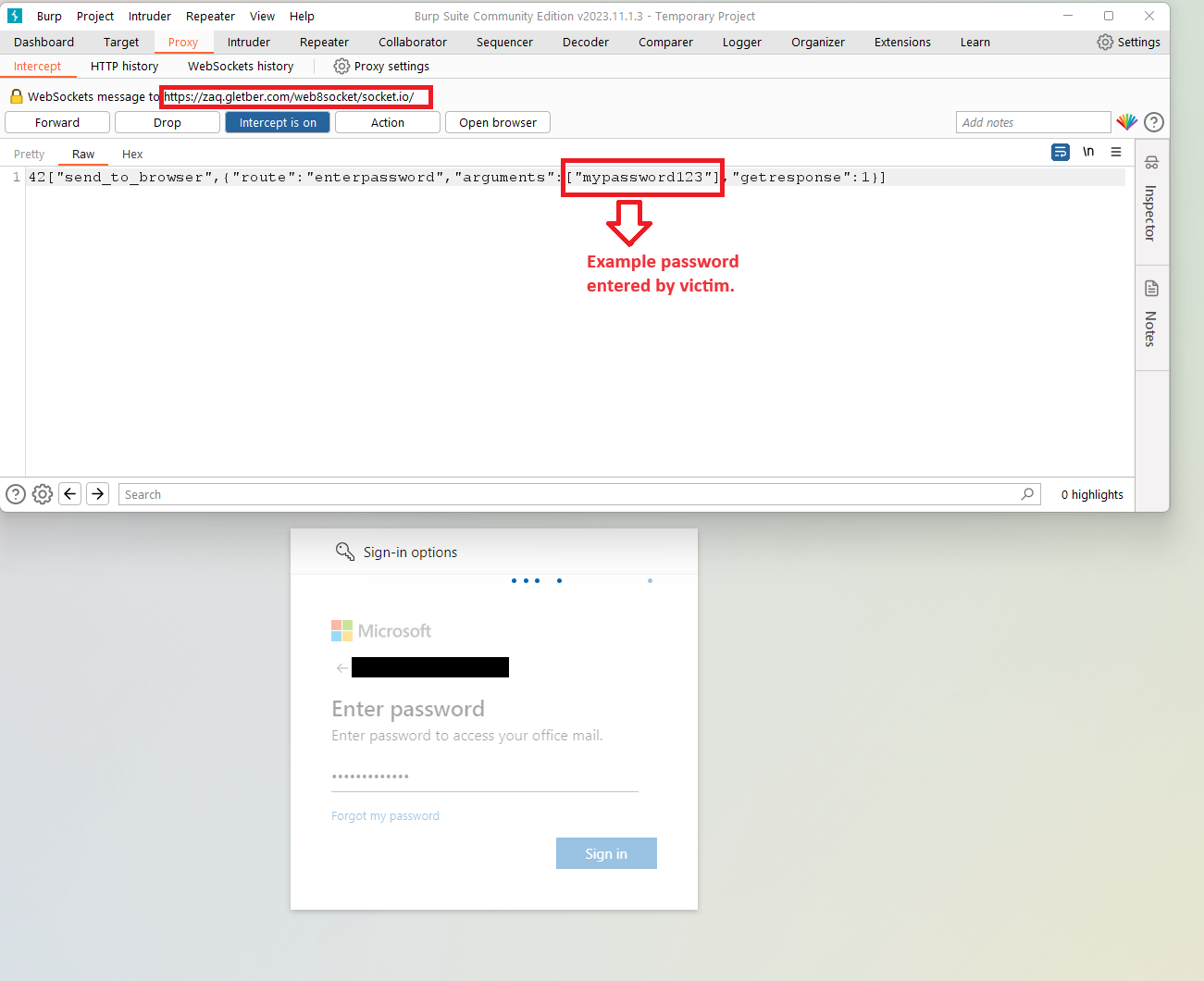
The victim is prompted to enter their login credentials and 2FA token on the fake login page, and the phishing site captures these details in real-time.
The stolen credentials and 2FA token are immediately relayed to the attackers via WebSockets, allowing them to hijack the target’s account before the authentication and MFA-validated token expires.
Source: EclecticIQ
From there, the attackers can access the compromised email account to exfiltrate sensitive information such as emails and documents or sell the credentials on the dark web for malware and ransomware attacks.
Robust phishing platform
From the perspective of the cybercriminals using the service, ONNX is a compelling and cost-effective platform.
The center of operations is on Telegram, where bots enable clients to manage their phishing operations through an intuitive interface. Moreover, there are dedicated support channels to assist users with any issues.
The Microsoft Office 365 phishing templates are customizable, and webmail services are available for sending phishing emails to targets.
The ONNX phishing kit also uses encrypted JavaScript code that decrypts itself during page load, adding a layer of obfuscation to evade detection by anti-phishing tools and scanners.
Additionally, ONNX uses Cloudflare services to prevent its domains from being taken down, including an anti-bot CAPTCHA and IP proxying.
There is also a bulletproof hosting service to ensure that the operations aren’t interrupted by reports and takedowns, as well as remote desktop protocol (RDP) services for managing the campaigns securely.

Source: EclecticIQ
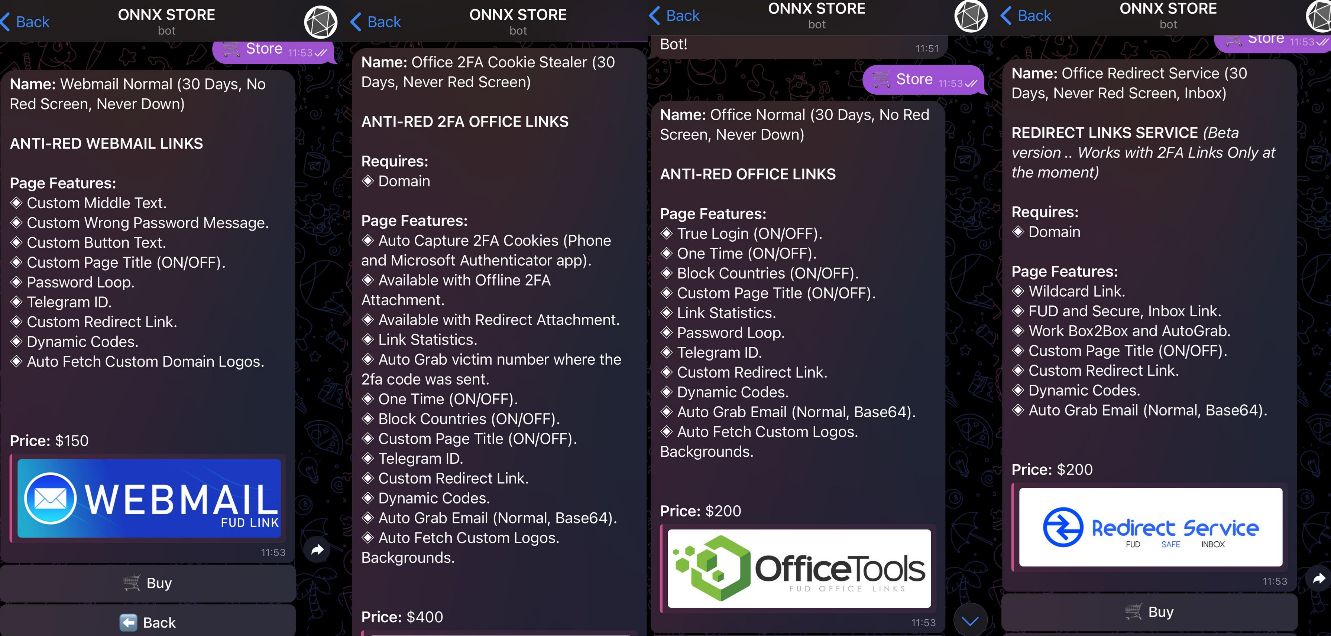
ONNX offers four subscription tiers summarized as follows:
- Webmail Normal ($150/month): Offers customizable text elements, a password loop, Telegram ID integration, custom redirect links, and auto-fetch custom domain logos.
- Office Normal ($200/month): Includes true login, one-time passwords, country blocking, custom page titles, password loops, Telegram integration, and custom logos.
- Office Redirect ($200/month): Provides wildcard links, fully undetectable inbox links, custom page titles, dynamic codes, and auto-grab email functionality for 2FA redirects.
- Office 2FA Cookie Stealer ($400/month): Captures 2FA cookies, supports offline 2FA, and includes custom page titles, Telegram integration, dynamic codes, and link statistics.
Source: EclecticIQ
All in all, ONNX Store is a dangerous threat for Microsoft 365 account holders, especially for companies engaged in the broader financial services sectors.
To protect against its sophisticated phishing attacks, admins are recommended to block PDF and HTML attachments from unverified sources, block access to HTTPS websites with untrusted or expired certificates, and set up FIDO2 hardware security keys for high-risk, privileged accounts.
EclecticIQ has also shared YARA rules in its report to help detect malicious PDF files that contain QR codes leading to phishing URLs.
Source link
lol
A new phishing-as-a-service (PhaaS) platform called ONNX Store is targeting Microsoft 365 accounts for employees at financial firms using QR codes in PDF attachments. The platform can target both Microsoft 365 and Office 365 email accounts and operates via Telegram bots and features two-factor authentication (2FA) bypass mechanisms. Researchers at EclecticIQ who discovered the activity believe that…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
