Latest Intel CPUs impacted by new Indirector side-channel attack
by nlqip

Modern Intel processors, including chips from the Raptor Lake and the Alder Lake generations are susceptible to a new type of a high-precision Branch Target Injection (BTI) attack dubbed ‘Indirector,’ which could be used to steal sensitive information from the CPU.
Indirector exploits flaws in Indirect Branch Predictor (IBP) and Branch Target Buffer (BTB), two hardware components found in modern Intel CPUs, to manipulate speculative execution for data extraction.
Three researchers at the University of California, San Diego discovered and presented the Indirector attack, with full details to be presented at the upcoming USENIX Security Symposium in August 2024.
Indirector attacks
The Indirect Branch Predictor is designed to predict the target addresses of indirect branches using historical execution information, while the Branch Target Buffer predicts the target addresses of direct branches using a set-associative cache structure.
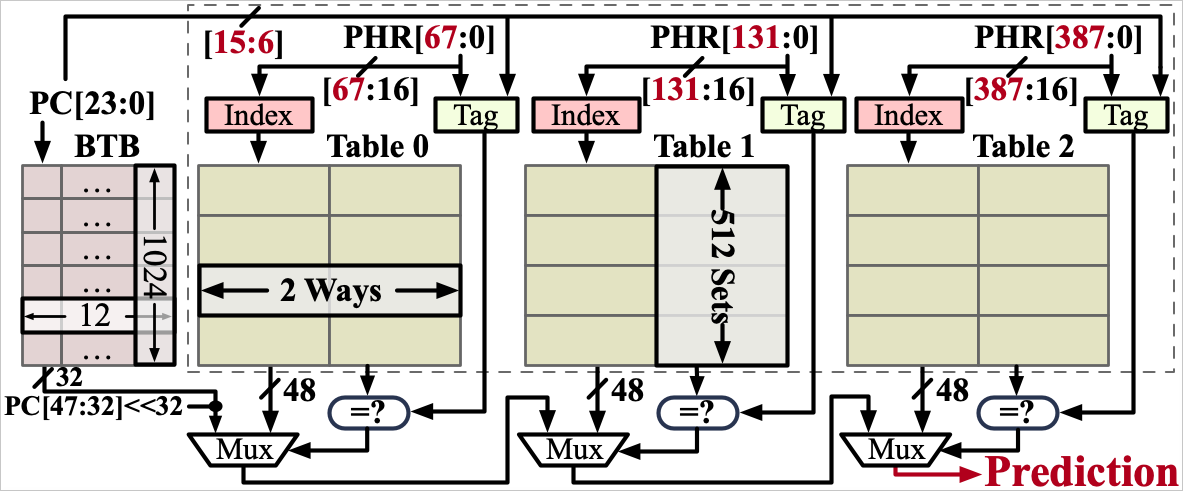
Source: indirector.cpusec.org
The researchers found that the two systems have flaws in indexing, tagging, and entry-sharing mechanisms and are generally built upon a predictable structure that allows for targeted, high-precision manipulation.
Based on the above, Indirector performs attacks mainly using three mechanisms:
- iBranch Locator: Custom tool that uses eviction-based techniques to identify the indices and tags of victim branches and accurately determine the IBP entries for specific branches.
- IBP/BTB injections: Perform targeted injections into the prediction structures to perform speculative code execution.
- ASLR bypass: Break Address Space Layout Randomization (ASLR) by determining the exact locations of indirect branches and their targets, making the prediction and manipulation of the control flow of protected processes easier.
Along with the speculative execution achieved by the targeted injections, the attacker can use cache side-channel techniques, such as measuring access times, to infer the accessed data.
Mitigating Indirector attacks
Indirector works against Raptor Lake and Alder Lake Intel CPUs, the 12th and 13th generation of the chipmaker’s ‘Core’ processors.
Intel was informed about the attack in February 2024 and has informed impacted hardware and software vendors.
The researchers propose two primary mitigations against the Indirector attack: more aggressive use of the Indirect Branch Predictor Barrier (IBPB) and bolstering the Branch Prediction Unit (BPU) design by incorporating more complex tags, encryption, and randomization.
However, there are significant performance trade-offs to consider, especially when using IBPB, so implementing the proposed mitigation requires delicate balancing work.
On Linux, IBPB is activated by default during transitions to SECCOMP mode or tasks with restricted indirect branches in the kernel, but its use is limited due to causing a 50% performance hit.
More details about Indirector, the attack methodologies, potential data leak mechanisms, and the suggested mitigations can be found in this technical paper.
The researchers have also published proof-of-concept code and tools for their branch injection attacks on GitHub.
Source link
lol
Modern Intel processors, including chips from the Raptor Lake and the Alder Lake generations are susceptible to a new type of a high-precision Branch Target Injection (BTI) attack dubbed ‘Indirector,’ which could be used to steal sensitive information from the CPU. Indirector exploits flaws in Indirect Branch Predictor (IBP) and Branch Target Buffer (BTB), two…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
