Detecting Living Off The Land attacks with Wazuh
by nlqip

Cyber attackers constantly improve their tactics to evade detection and achieve malicious objectives, making it important for organizations to develop better detection and response strategies. The Living Off The Land (LOTL) technique is an example of a stealthy attack vector cyber attackers use to avoid detection.
It is an infiltration technique that allows adversaries to attack targeted systems without raising suspicion for extended periods.
LOTL attacks are often called fileless attacks because threat actors use existing tools on the victim’s endpoint, unlike traditional malware attacks that require customized programs. Instead, they use tools like binaries, scripts, libraries, or drivers already present in the endpoint.
These attacks are becoming more challenging due to the absence of unique, recognizable signatures and their ability to camouflage as typical system utilities.
Why threat actors leverage LOTL techniques
Threat actors leverage LOTL techniques for the following reasons:
- The absence of files or signatures in LOTL attacks makes detection challenging, thereby increasing the difficulty of future prevention and enabling attackers to reuse tactics.
- Threat actors effectively utilize LOTL techniques across various environments, eliminating the need to create and deploy specialized attack tools.
- Threat actors leverage built-in system tools in LOTL attacks to blend in with normal network and system activities, making it difficult for security analysts to differentiate between legitimate and malicious behaviors.
Understanding the rationale behind LOTL techniques is important for implementing adequate cyber defense strategies against these increasingly prevalent forms of cyber threat.
How LOTL attacks work
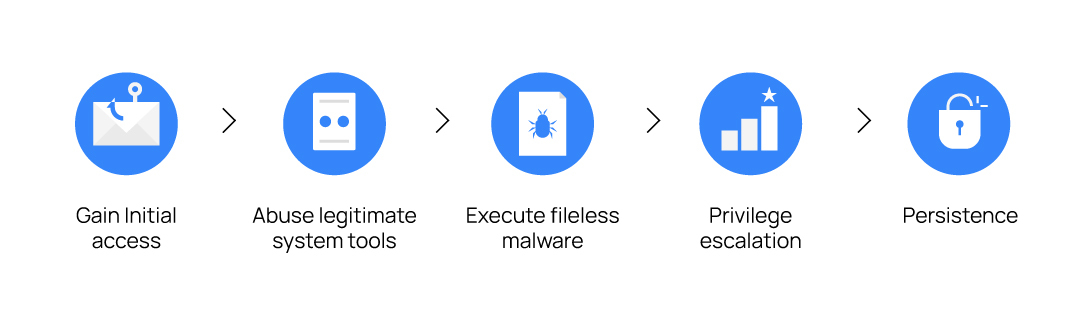
Here’s how LOTL attacks typically operate:
- Gain initial access: Attackers gain initial access through brute force attacks, vulnerability exploitation, or social engineering. For example, they might trick victims into visiting a compromised website, where they exploit browser vulnerabilities.
- Abuse legitimate system tools: Attackers abuse legitimate system tools and misconfigured system settings for malicious purposes. Common tools include command line utilities (cron, wget, curl, WMIC, net.exe, PowerShell), scripting languages (Bash, JavaScript), and administrative tools (SSH, PsExec).
- Execute fileless malware: Attackers execute fileless malicious code and modify system programs in memory without creating new files on the disk. They may also exploit some browser-based vulnerabilities to execute malicious processes.
- Privilege escalation: Attackers discreetly conduct malicious activities within the compromised network to gain remote access, perform lateral movement, escalate privileges, and exfiltrate sensitive data. For example, they might abuse legitimate administrative tools or misconfigured system settings to gain elevated privileges.
- Persistence: Attackers maintain persistence by creating scheduled tasks, modifying registry keys, and leveraging legitimate autostart mechanisms for future attacks.
Strengthen your cyber defense against LOTL attacks with Wazuh
Organizations require comprehensive cyber security monitoring capabilities to detect anomalous behavior and suspicious use of system utilities within their IT environment.
You can enhance your cyber defense and response by leveraging security solutions such as Extended Detection and Response (XDR) and Security Information and Event Management (SIEM).
Wazuh is a free, open source security platform that offers unified XDR and SIEM capabilities across workloads in cloud and on premises environments.
Wazuh performs log data analysis, file integrity monitoring, threat detection, real-time alerting, and automated incident response to detect and respond to LOTL attacks.
Detecting initial access attempts
Effective detection strategies for identifying attackers’ attempts to gain initial access include continuous monitoring for vulnerability exploitation and brute-force login attempts. Such strategies generate real-time alerts for unusual activities, detect changes to user accounts, and analyze network connections for suspicious patterns.
Wazuh employs its log data collection capability to collect logs from monitored endpoints, applications, and network devices, which are then analyzed in real-time. The Wazuh server uses customizable decoders and rules to extract and map relevant information from the collected logs to appropriate fields. It also processes this information and records them as alerts within the /var/ossec/logs/alerts/ directory.
The blog post on detecting the exploration of XZ Utils vulnerability with Wazuh shows how users can identify potential exploitation of the CVE-2024-3094 vulnerability within their monitored endpoints. You can configure Wazuh agents to identify and forward logs about suspicious sshd descendant processes to the Wazuh server for processing.
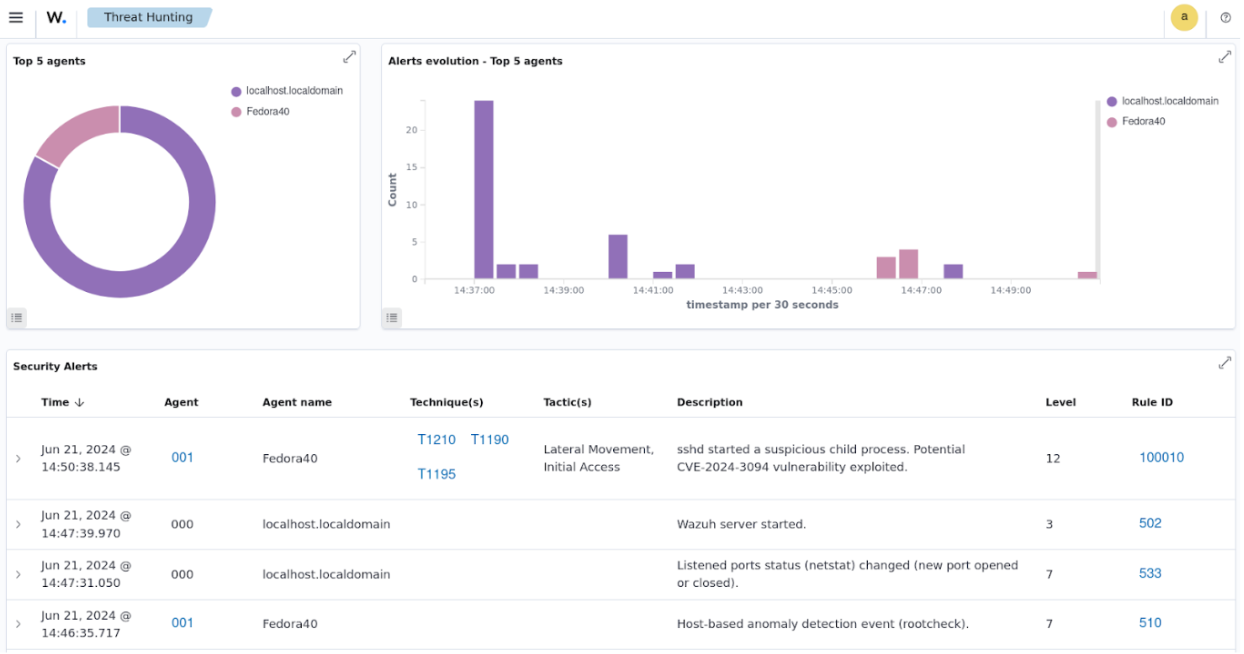
Organizations can detect and address suspicious activities in their IT environment by leveraging security solutions like Wazuh, which includes real-time log data collection and analysis capabilities.
Detecting abuse of system tools
Monitoring the unauthorized use of legitimate tools like PowerShell, Crontab, Schtasks, and SSH allows organizations to detect deviations from normal system activities and respond to malicious actions. Early detection of these malicious activities prevents attackers from abusing these tools to conduct lateral movement or perform other illegitimate actions.
Wazuh has out-of-the-box rulesets to detect and alert administrators about instances of malware that abuse native system utilities to accomplish the attacker’s malicious objectives. Furthermore, you can add custom rules and decoders that detect other specific activities.
For instance, you can use Wazuh to monitor commonly abused Windows utilities such as nltest, bcedit, vssadmin, attrib, or the schtasks. The Wazuh agent collects and forwards logs from the Windows event channel to the Wazuh server for analysis.
These logs are filtered for process creation events to detect when native utilities are executed.
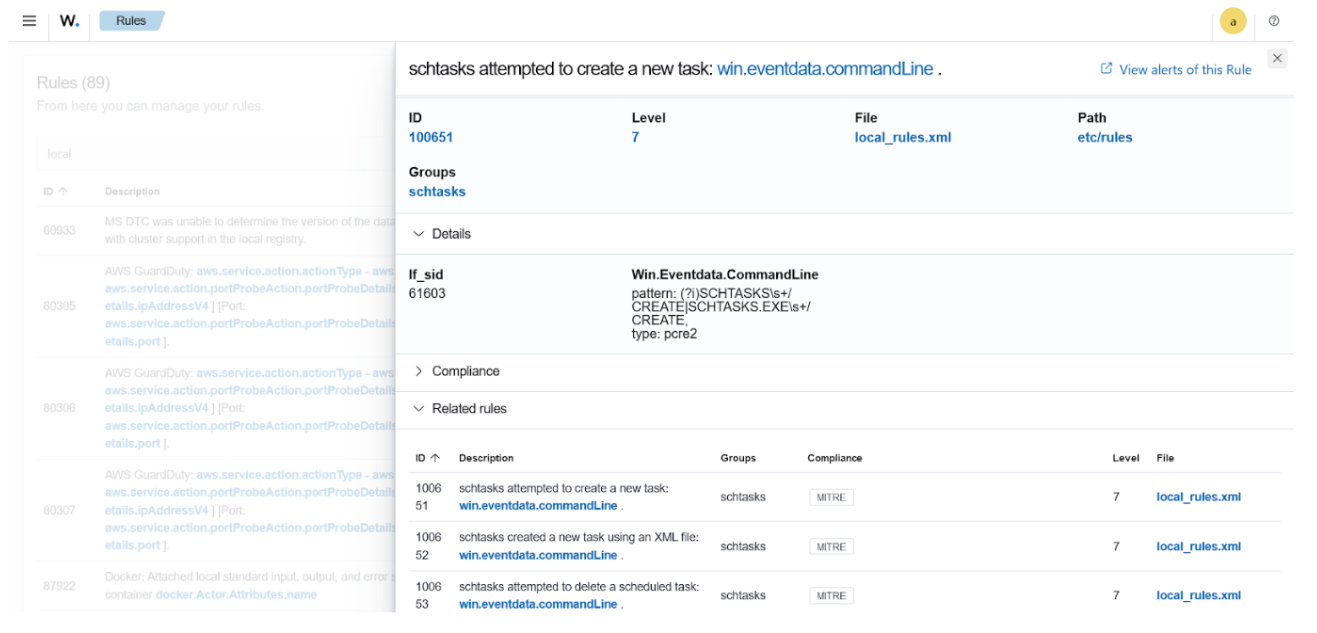
A LOTL attack associated with the MITRE ATT&CK technique T1053.005 involves the abuse of the Task Scheduler (schtasks) utility by executing specific commands to schedule malicious tasks:
> schtasks /create /tn test-task /tr "C:WindowsSystem32calc.exe" /sc onlogon /ru System /f
> schtasks.exe /CREATE /XML C:WindowsTEMPredacted.xml /TN task-task /F
> schtasks.exe /CREATE /XML C:redactedredacted.xml /TN task-task /F
> SCHTASKS /Delete /TN * /F
By creating the following custom rules, Wazuh detects the above activities in real-time and triggers alerts accordingly.
Detecting unauthorized configuration changes
Attackers often manipulate and modify system configuration settings to maintain persistence or conceal their presence. To defend against this stage of LOTL attack, organizations should regularly conduct endpoint scans to identify misconfigurations that do not comply with security best practices and standards.
This security measure is essential for prompt detection of unauthorized changes and response to LOTL attacks before they cause significant harm.
Wazuh assesses system configuration settings using its Security Configuration Assessment (SCA) capability to identify misconfigurations and vulnerabilities on monitored endpoints.
Users can also monitor critical configuration files and directories for unauthorized and unintended changes using the Wazuh File Integrity Monitoring (FIM) capability.
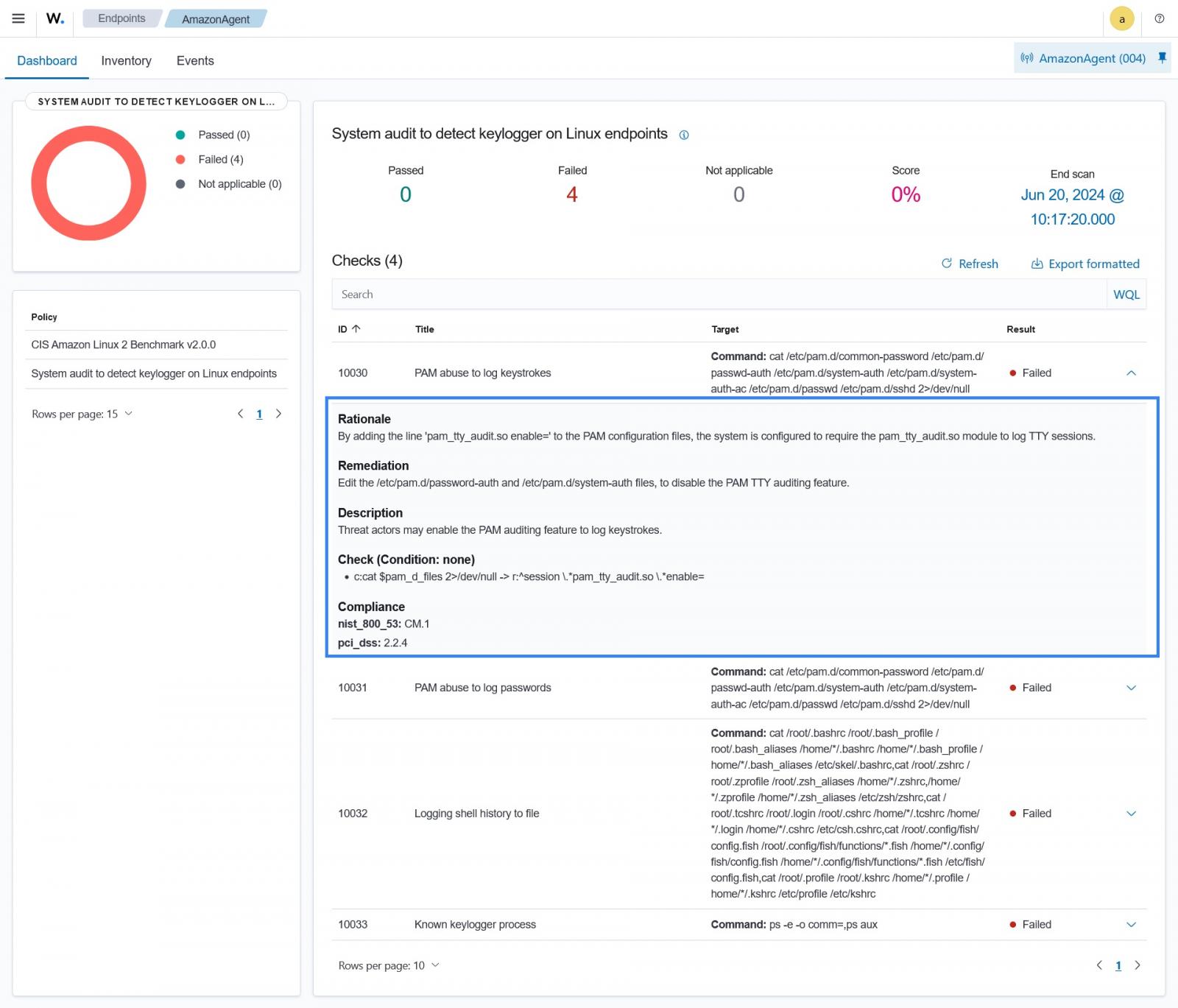
For example, you can use the Wazuh SCA capability to perform system audits to detect keyloggers on Linux endpoints that leverage LOTL techniques. This is achieved by setting up a custom SCA policy on the Wazuh server to initiate routine scans on all monitored Linux endpoints.
The SCA policy checks the configuration settings to identify instances where adversaries may have manipulated legitimate programs to log the victim’s keyboard activities in terminal sessions (TTY).
The image below demonstrates Wazuh detecting instances where adversaries abuse trusted processes such as PAM on a Linux endpoint to capture keystrokes and credentials from the victim. Highlighting the rationale behind the attack and how users can remediate it when detected.
Detecting unusual resource usage
Organizations can enhance their defense against LOTL attacks by monitoring abnormal resource usage patterns on their endpoints. Unusual resource consumption, such as excessive CPU usage, memory utilization, or network activity, often indicates malicious activities associated with LOTL techniques.
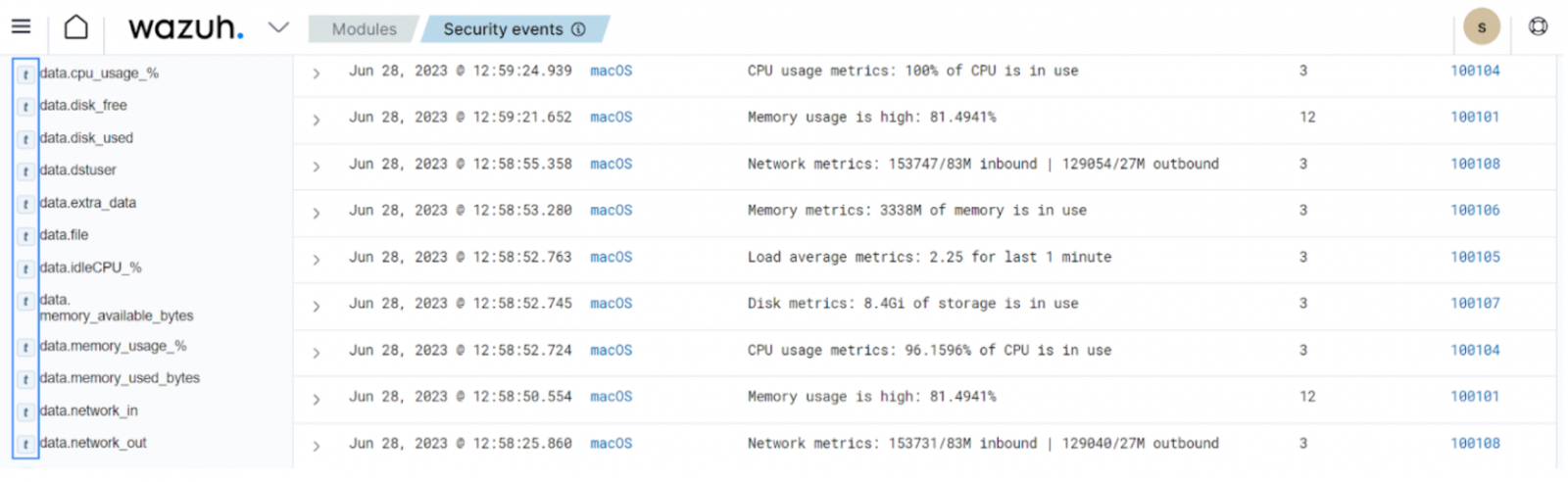
By tracking command line executions and performance metrics, organizations can detect these subtle indicators of compromise.
Wazuh offers a command monitoring capability that tracks the commands executed on monitored endpoints. With this capability, users can configure Wazuh to capture and log details about the output of specific commands executed, providing visibility into unusual resource usage by system processes.
The Wazuh agent executes these commands periodically on the configured endpoint based on set frequency, monitoring their execution and forwarding the output to the Wazuh server for analysis.
The blog post on monitoring macOS resource usage demonstrates how the Wazuh agent uses the command monitoring capability to gather system information. This information includes the endpoint CPU usage, CPU load, memory usage, disk usage, and other performance metrics.
This data provides insights into the utilization of system resources, enabling users to detect ongoing LOTL attacks.
Detecting known vulnerabilities
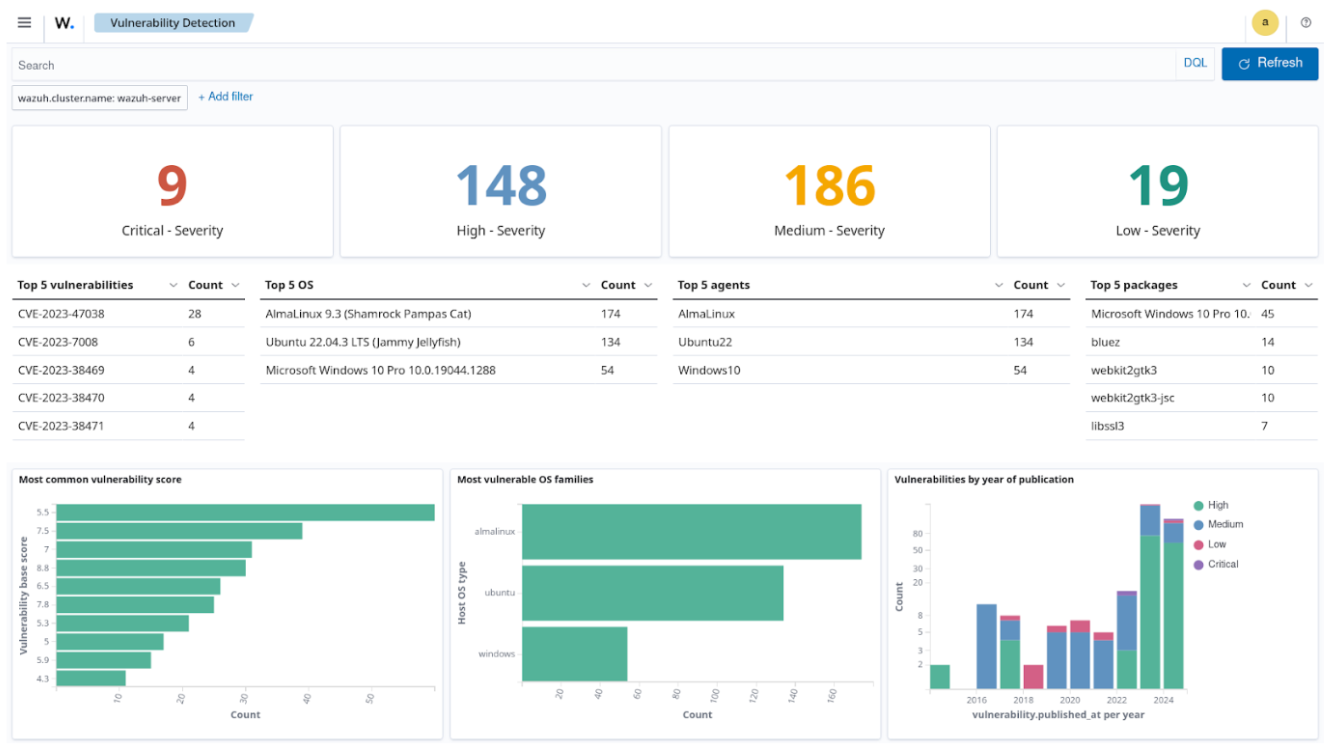
Regular vulnerability scans allow organizations to identify and patch security weaknesses. This is important as attackers often exploit known vulnerabilities to establish long-term presence and evade detection.
Wazuh leverages its vulnerability detection capability to provide comprehensive visibility into known vulnerabilities that adversaries may exploit to establish persistence. This is done by comparing installed software versions against known vulnerabilities sourced from various databases.
These databases include the National Vulnerability Database (NVD), Canonical, Red Hat, Debian, Arch Linux, and others.
Conclusion
Living Off The Land (LOTL) attacks are stealthy cyberattacks where threat actors leverage built-in system tools rather than external malware to achieve their goals.
Organizations must employ a multilayered approach with diverse detection capabilities to increase the likelihood of detecting and responding to such attacks.
Wazuh offers various detection mechanisms to increase the chances of detecting LOTL attacks and mitigate the potential impact. It also allows you to integrate third-party solutions to suit your use case and meet the peculiarities of your environment.
Learn more about Wazuh by checking out our documentation and joining our community of professionals.
Sponsored and written by Wazuh.
Source link
lol
Cyber attackers constantly improve their tactics to evade detection and achieve malicious objectives, making it important for organizations to develop better detection and response strategies. The Living Off The Land (LOTL) technique is an example of a stealthy attack vector cyber attackers use to avoid detection. It is an infiltration technique that allows adversaries to…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
