Notorious FIN7 hackers sell EDR killer to other threat actors
by nlqip

The notorious FIN7 hacking group has been spotted selling its custom “AvNeutralizer” tool, used to evade detection by killing enterprise endpoint protection software on corporate networks.
FIN7 is believed to be a Russian hacking group that has been active since 2013, initially focusing on financial fraud by hacking organizations and stealing debit and credit cards.
They later moved into the ransomware space and were linked with the DarkSide and BlackMatter ransomware-as-a-operation platforms. The same threat actors are also likely tied to the BlackCat ransomware operation, which recently conducted an exit scam after stealing a UnitedHealth ransom payment.
FIN7 is known for sophisticated phishing and engineering attacks to gain initial access to corporate networks, including impersonating BestBuy to send malicious USB keys and developing custom malware and tools.
To add to the exploits, they created a fake security company named Bastion Secure to hire pentesters and developers for ransomware attacks without the applicants knowing how their work was being used.
FIN7 hackers are also tracked under other names, including Sangria Tempest, Carbon Spider, and the Carbanak Group.
FIN7 selling tools to other hackers
In a new report by SentinelOne, researchers say that one of the custom tools created by FIN7 is “AvNeutralizer” (aka AuKill), a tool used to kill security software that was first spotted in attacks by the BlackBasta ransomware operation in 2022.
As BlackBasta was the only ransomware operation using the tool at the time, the researchers believed that there was a connection between the two groups.
However, SentinelOne’s historic telemetry has shown that the tool was used in attacks by five other ransomware operations, showing a wide distribution of the tool.
“Since early 2023, our telemetry data reveals numerous intrusions involving various versions of AvNeutralizer,” explains a report by SentinelOne researcher Antonio Cocomazzi.
“About 10 of these are attributed to human-operated ransomware intrusions that deployed well-known RaaS payloads including AvosLocker, MedusaLocker, BlackCat, Trigona and LockBit.”
Further research revealed that threat actors operating under the aliases “goodsoft”, “lefroggy”, “killerAV” and “Stupor” had been selling an “AV Killer” on Russian-speaking hacking forums since 2022 for prices ranging from $4,000 to $15,000.
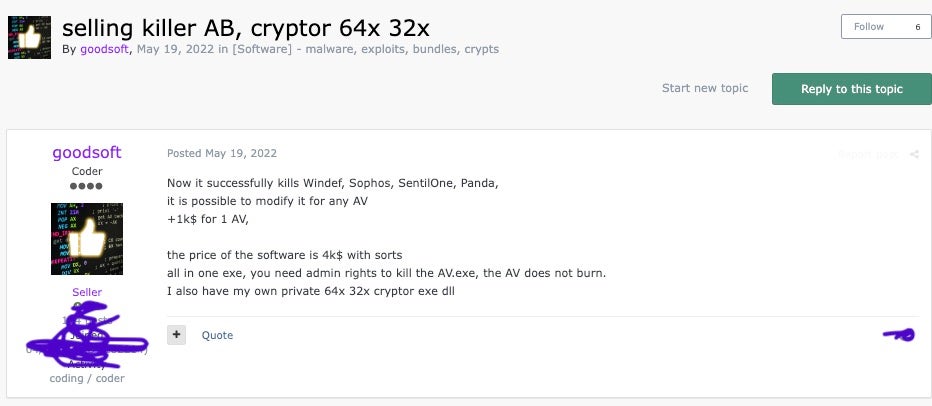
Source: SentinelOne
A 2023 report from Sophos detailed how AvNeutralizer/AuKill abused the legitimate SysInternals Process Explorer driver to terminate antivirus processes running on a device.
The threat actors claimed that this tool could be used to kill any antivirus/EDR software, including Windows Defender and products from Sophos, SentinelOne, Panda, Elastic, and Symantec.
SentinelOne now found that FIN7 have updated AVNeutralizer to utilize the Windows ProcLaunchMon.sys driver to hang processes, making them no longer function correctly.
“AvNeutralizer uses a combination of drivers and operations to create a failure in some specific implementations of protected processes, ultimately leading to a denial of service condition,” explains SentinelOne.
“It employs the TTD monitor driver ProcLaunchMon.sys, available on default system installations in the system drivers directory, in conjunction with updated versions of the process explorer driver with version 17.02 (17d9200843fe0eb224644a61f0d1982fac54d844), which has been hardened for cross process operations abuse and is currently not blocked by the Microsoft’s WDAC list.”
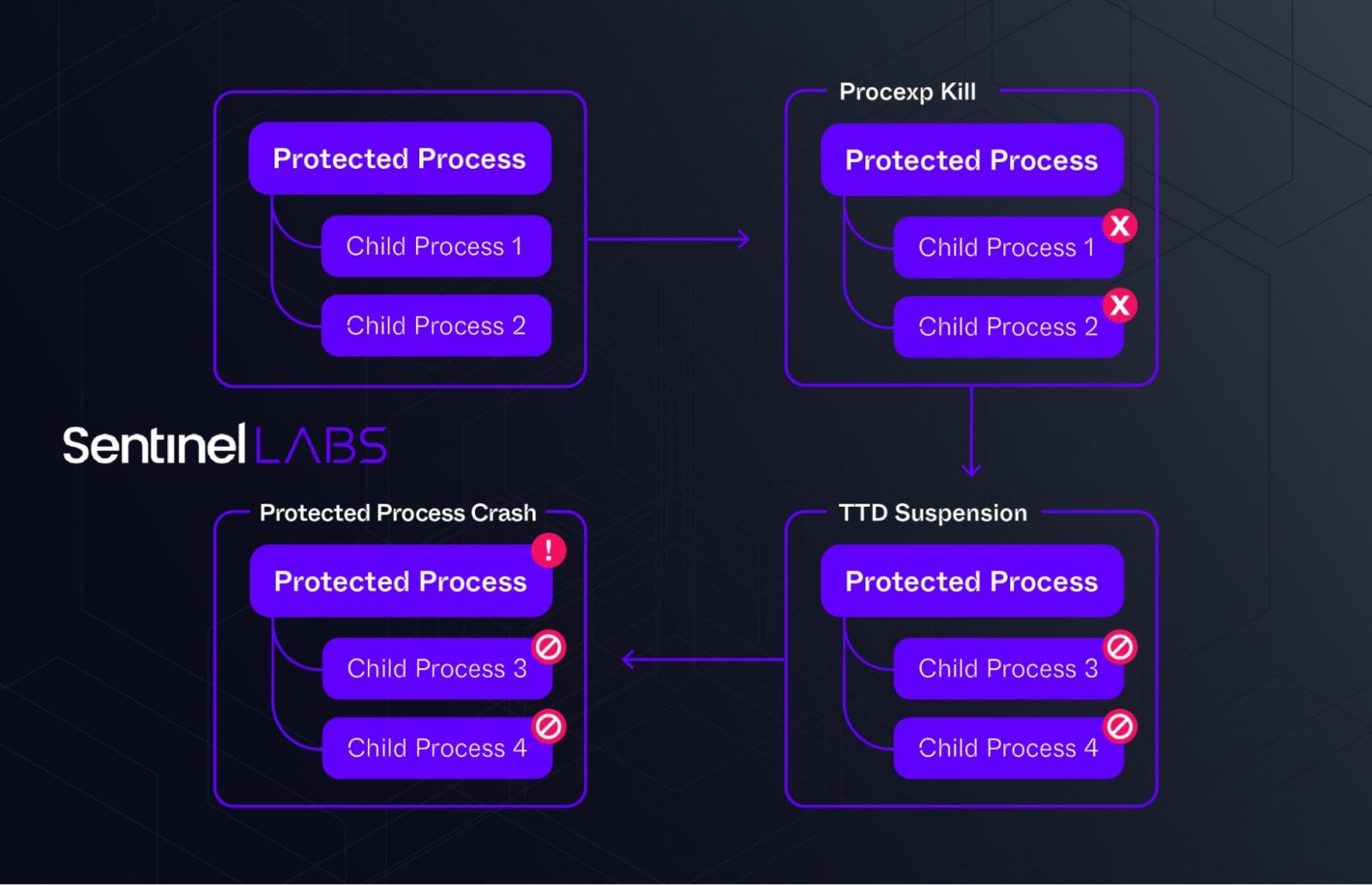
Source: SentinelOne
SentinelOne found additional custom tooling and malware used by FIN7, which is not known to be sold to other threat actors:
Powertrash (a PowerShell backdoor), Diceloader (a light-weight C2-contolled backdoor), Core Impact (a penetration testing toolkit), and a SSH-based backdoor.
The researchers warn that FIN7’s continued evolution and innovation in tooling and techniques, as well as the selling of its software, make it a significant threat to enterprises worldwide.
“FIN7’s continuous innovation, particularly in its sophisticated techniques for evading security measures, showcases its technical expertise,” concludes SentinelOne researcher Antonio Cocomazzi.
“The group’s use of multiple pseudonyms and collaboration with other cybercriminal entities makes attribution more challenging and demonstrates its advanced operational strategies.”

Source link
lol
The notorious FIN7 hacking group has been spotted selling its custom “AvNeutralizer” tool, used to evade detection by killing enterprise endpoint protection software on corporate networks. FIN7 is believed to be a Russian hacking group that has been active since 2013, initially focusing on financial fraud by hacking organizations and stealing debit and credit cards.…
Recent Posts
- Microsoft rolls out Recall to Windows Insiders with Copilot+ PCs
- Five Companies That Came To Win This Week
- The 10 Hottest Semiconductor Startups Of 2024
- Cybersecurity Snapshot: Prompt Injection and Data Disclosure Top OWASP’s List of Cyber Risks for GenAI LLM Apps
- Healthcare Ransomware Attacks: How to Prevent and Respond Effectively | BlackFog
