Over 3,000 GitHub accounts used by malware distribution service
by nlqip

Threat actors known as ‘Stargazer Goblin’ have created a malware Distribution-as-a-Service (DaaS) from over 3,000 fake accounts on GitHub that push information-stealing malware.
The malware delivery service is called Stargazers Ghost Network and it utilizes GitHub repositories along with compromised WordPress sites to distribute password-protected archives that contain malware. In most cases, the malware are infostealers, such as RedLine, Lumma Stealer, Rhadamanthys, RisePro, and Atlantida Stealer.
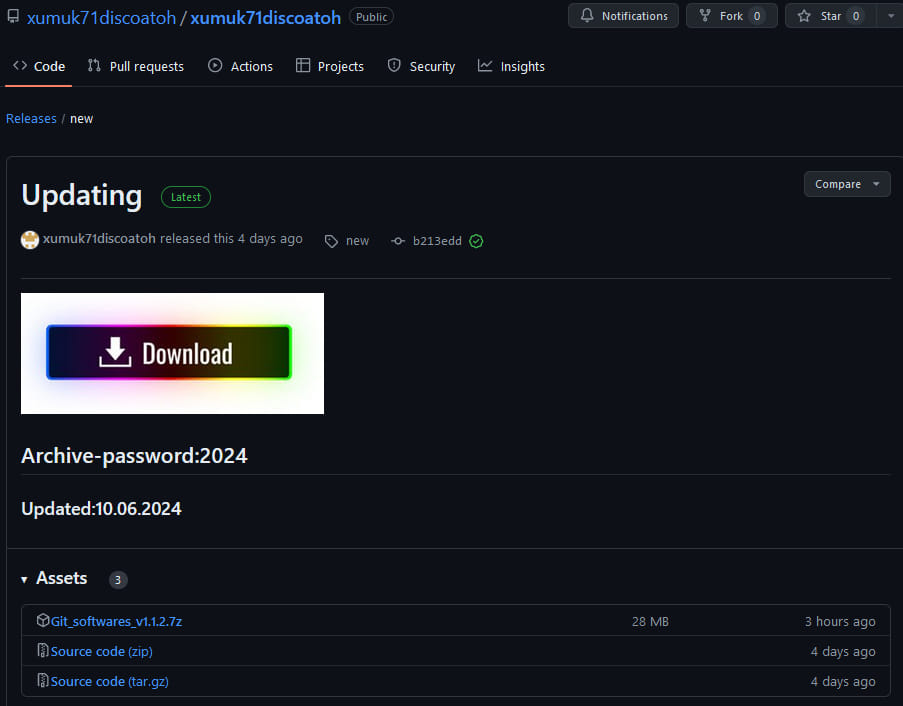
Source: Check Point
Due to GitHub being a well-known, trusted service, people treat it with less suspicion and may be more likely to click on links they find in the service’s repositories.
Check Point Research discovered the operation, which says it is the first time that such an organized and large-scale scheme has been documented running on GitHub.
“The campaigns performed by the Stargazers Ghost Network and malware distributed via this service are extremely successful,” explains the report by Check Point Research.
“In a short period of time, thousands of victims installed software from what appears to be a legitimate repository without suspecting any malicious intent. The heavily victim-oriented phishing templates allow threat actors to infect victims with specific profiles and online accounts, making the infections even more valuable.”
GitHub ‘ghosts’ spreading malware
The creator of the DaaS operation, Stargazer Goblin, has been actively promoting the malware distribution service on the dark web since June 2023. However, Check Point says there’s evidence it has been active since August 2022.
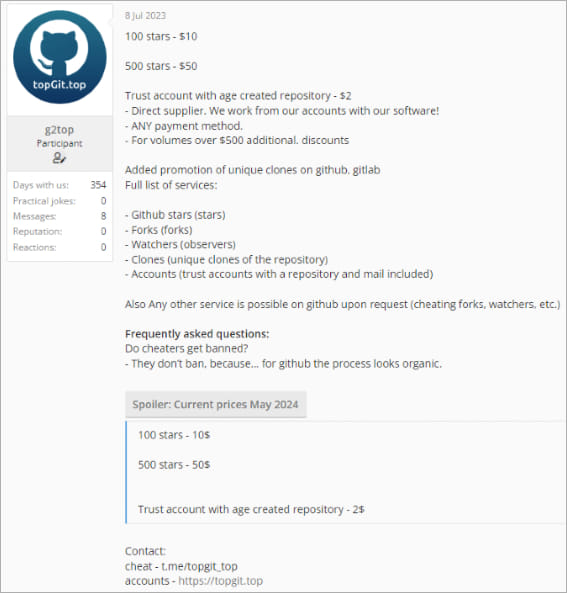
Source: Check Point
Stargazer Goblin established a system where they create hundreds of repositories using three thousand fake ‘ghost’ accounts. These accounts star, fork, and subscribe to malicious repositories to increase their apparent legitimacy and make them more likely to appear on GitHub’s trending section.
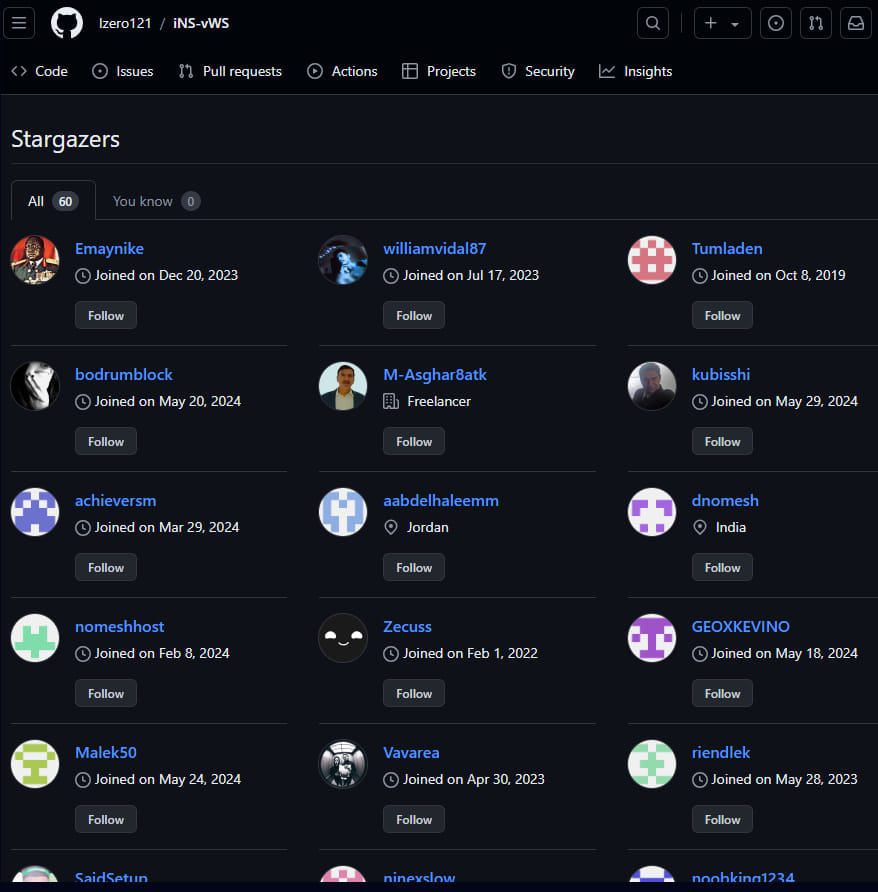
Source: Check Point
The repositories use project names and tags that target specific interests like cryptocurrency, gaming, and social media.
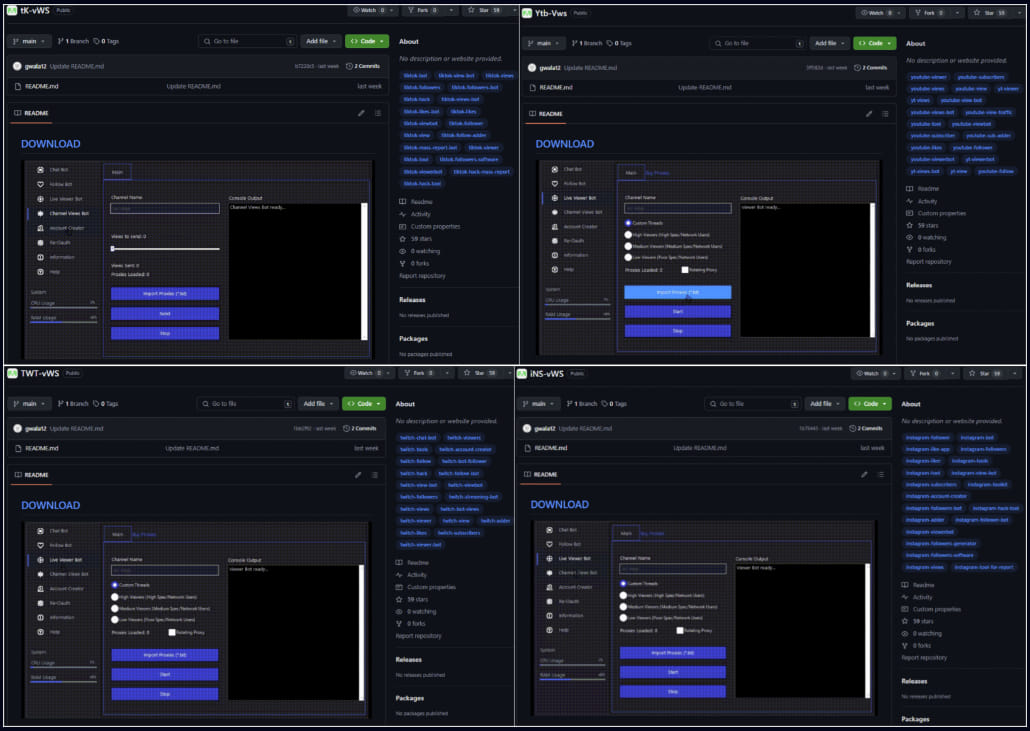
Source: Check Point
The ‘ghost’ accounts are assigned distinct roles. One group serves the phishing template, another provides the phishing image, and a third serves the malware, which gives the scheme a certain level of operational resilience.
“The third account, which serves the malware, is more likely to be detected. When this happens, GitHub bans the entire account, repository, and associated releases,” explains researcher Antonis Terefos.
“In response to such actions, Stargazer Goblin updates the first account’s phishing repository with a new link to a new active malicious release. This allows the network to continue operating with minimum losses when a malware-serving account is banned.”
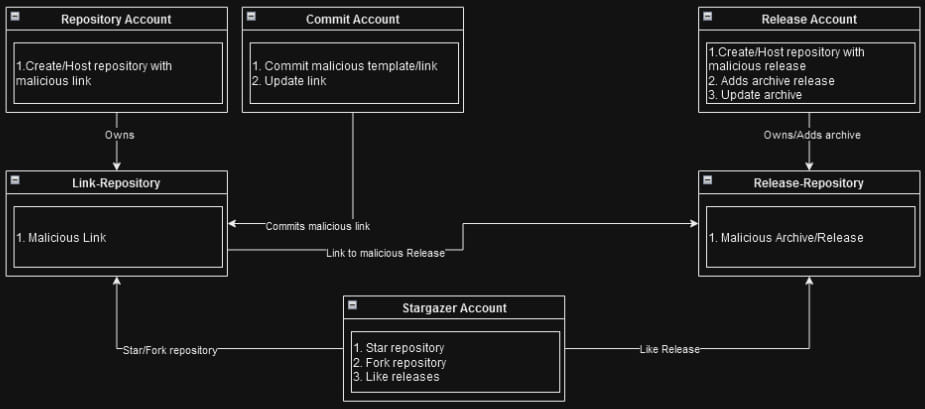
Source: Check Point
Check Point has observed a case of a YouTube video with a software tutorial linking to the same operative as in one of the ‘Stargazers Ghost Network’ GitHub repositories.
The researchers note that it could be one of the potentially multiple examples of channels used to funnel traffic to phishing repositories or malware distribution sites.
In terms of the size of the operation and its profit generation, Check Point estimates that the threat actor has made over $100,000 since the service’s launch.
As for what malware is distributed through the Stargazers Ghost Network’s operation, Check Point says it includes RedLine, Lumma Stealer, Rhadamanthys, RisePro, and Atlantida Stealer, among others.
In one example attack chain presented in Check Point’s report, the GitHub repository redirects visitors to a compromised WordPress site, from where they download a ZIP archive containing an HTA file with VBScript.
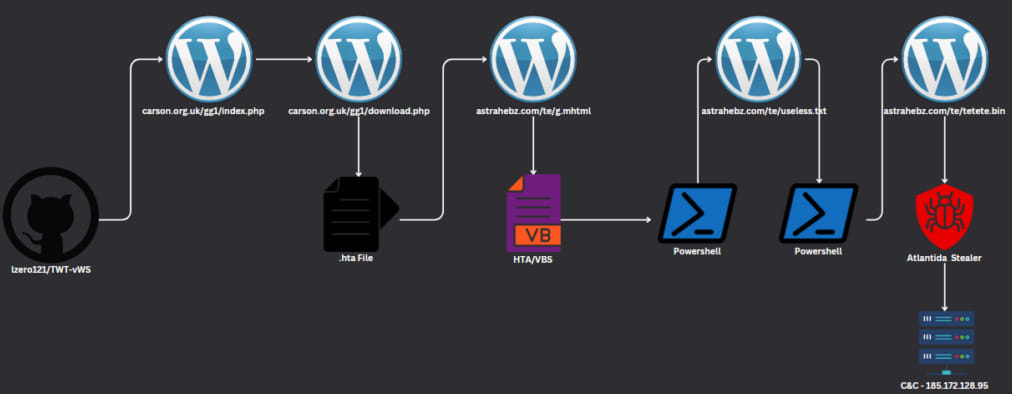
Source: Check Point
The VBScript triggers the execution of two successive PowerShell scripts that ultimately lead to the deployment of the Atlantida Stealer.
Although GitHub has taken action against many of the malicious and essentially fake repositories, taking down over 1,500 since May 2024, Check Point says that over 200 are currently active and continue to distribute malware.
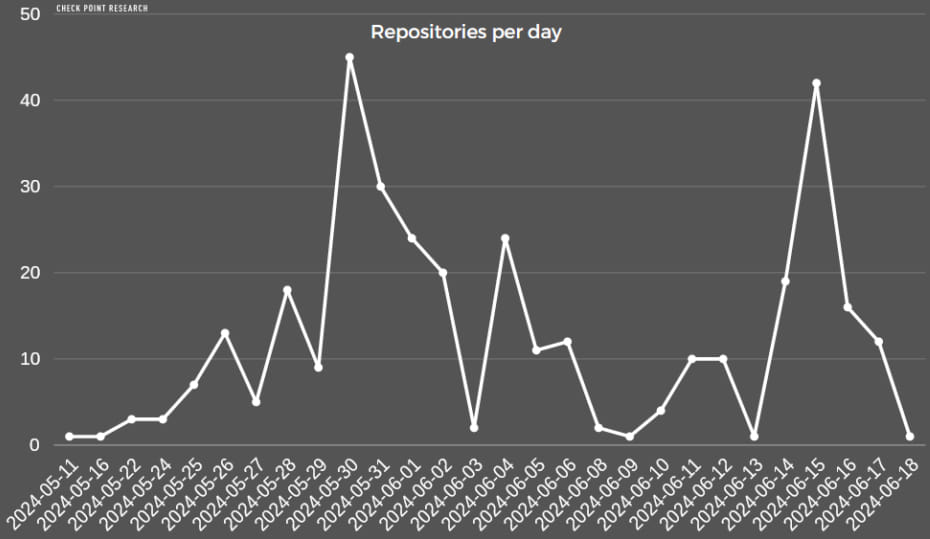
Source: Check Point
Users arriving on GitHub repositories through malvertising, Google Search results, YouTube videos, Telegram, or social media are advised to be very cautious with file downloads and the URLs they click.
This is especially true of password-protected archives, which cannot be scanned by antivirus software. For these types of files, it is suggested you extract them on a VM and scan the extracted contents with antivirus software to check for malware.
If a virtual machine is not available, you can also use VirusTotal, which will prompt for the password of a protected archive so it can scan its contents. However, VirusTotal can only scan a protected archive if it contains a single file.

Source link
lol
Threat actors known as ‘Stargazer Goblin’ have created a malware Distribution-as-a-Service (DaaS) from over 3,000 fake accounts on GitHub that push information-stealing malware. The malware delivery service is called Stargazers Ghost Network and it utilizes GitHub repositories along with compromised WordPress sites to distribute password-protected archives that contain malware. In most cases, the malware are infostealers, such…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
