Google Chrome adds app-bound encryption to block infostealer malware
by nlqip

Google Chrome now comes with better cookie protection on Windows systems, with the addition of app-bound encryption, which improves defenses against information-stealing malware attacks.
As Chrome software engineer Will Harris explained in a blog post published today, Chrome currently uses the most robust techniques provided by each operating system to safeguard sensitive data such as cookies and passwords: Keychain services on macOS, kwallet or gnome-libsecret on Linux, and the Data Protection API (DPAPI) on Windows.
However, while DPAPI can protect data at rest from cold boot attacks or unauthorized users gaining access to Windows systems, it does not protect against malicious tools or scripts designed to execute code as the logged-in user, which is something that infostealer malware exploits.
“In Chrome 127 we are introducing a new protection on Windows that improves on the DPAPI by providing Application-Bound (App-Bound) Encryption primitives,” said Chrome Software Engineer Will Harris.
“Rather than allowing any app running as the logged in user to access this data, Chrome can now encrypt data tied to app identity, similar to how the Keychain operates on macOS.”
App-Bound Encryption uses a privileged service to confirm an app’s identity when it requests encryption. The service encodes the app’s identity into the encrypted data and ensures that only the intended app can decrypt it, causing other apps to fail when attempting to decrypt the data.
Since the service operates with system privileges, attackers would need to gain system privileges or inject code into an app like Chrome, which is not a typical or legitimate action and makes it easier for antivirus software to detect when malware is used to steal data.
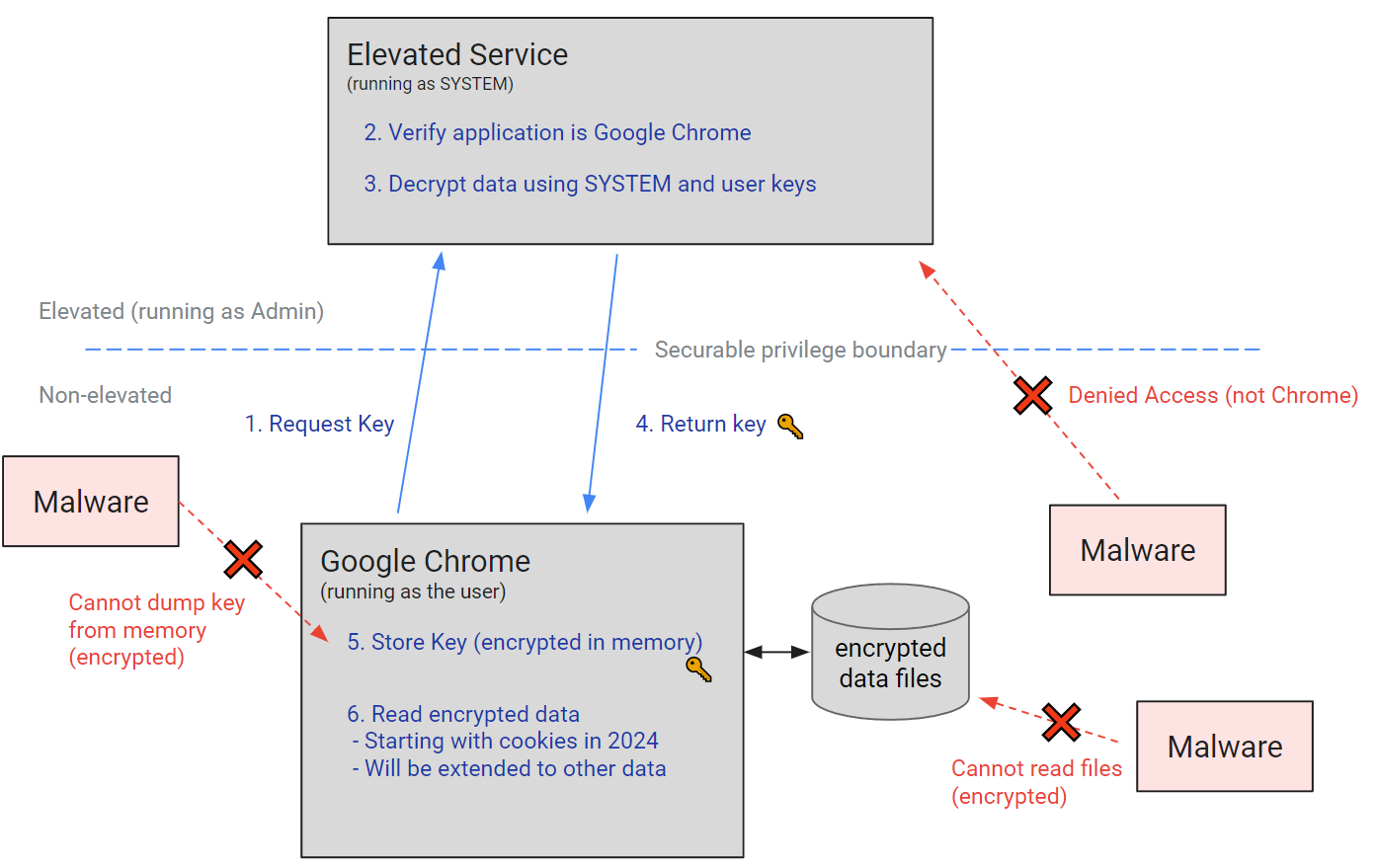
This improved protection capability will be expanded to passwords, payment data, and other persistent authentication tokens to better defend users’ sensitive data from infostealer malware attacks.
It also adds to other recent initiatives and features announced by Google to protect user data, such as Chrome’s download protection using Safe Browsing, Device Bound Session Credentials, and account-based threat detection to flag the use of stolen cookies.
“App-Bound Encryption increases the cost of data theft to attackers and also makes their actions far noisier on the system. It helps defenders draw a clear line in the sand for what is acceptable behavior for other apps on the system,” Harris added.
“As the malware landscape continually evolves we are keen to continue engaging with others in the security community on improving detections and strengthening operating system protections, such as stronger app isolation primitives, for any bypasses.”
Last week, Google also rolled out new Chrome warnings when downloading password-protected archives and implemented improved alerts with more information about potentially malicious downloaded files.

Source link
lol
Google Chrome now comes with better cookie protection on Windows systems, with the addition of app-bound encryption, which improves defenses against information-stealing malware attacks. As Chrome software engineer Will Harris explained in a blog post published today, Chrome currently uses the most robust techniques provided by each operating system to safeguard sensitive data such as…
Recent Posts
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
- Microsoft rolls out Recall to Windows Insiders with Copilot+ PCs
- Five Companies That Came To Win This Week
- The 10 Hottest Semiconductor Startups Of 2024
- Cybersecurity Snapshot: Prompt Injection and Data Disclosure Top OWASP’s List of Cyber Risks for GenAI LLM Apps
