Fraud ring pushes 600+ fake web shops via Facebook ads
by nlqip

A malicious fraud campaign dubbed “ERIAKOS” promotes more than 600 fake web shops through Facebook advertisements to steal visitors’ personal and financial information.
The sites promote products from well-known brands and include significant discounts to draw in visitors but are only accessible via mobile devices to evade detection by security scanners.
Recorded Future discovered the ERIAKOS operation and believes it likely originates from China, based on the domain registrar, card networks, and payment service providers used.
Although most of the sites the researchers mapped are now offline, as they’re short-lived, the campaign is still active and constantly generating new advertisement waves for people to visit freshly created sites.
The fraud campaign
Recorded Future named the campaign after its content delivery network, hosted at eriakos[.]com, which is common across all identified fake web stores. The researchers discovered the fraud campaign on April 17, 2024, but it’s unknown when it first became active.
Each fraudulent site features roughly a hundred ads on Facebook targeting mobile users, which include fake user testimonials in comments to boost engagement.
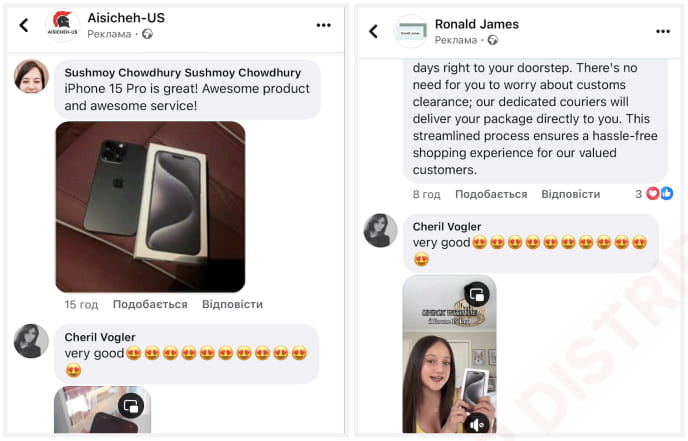
Source: Recorded Future
The ads promote massive discounts on popular products, such as Nike sneakers, North Face clothing, and Amazon iPhones, but with unrealistic time-limited offers to attract potential buyers.
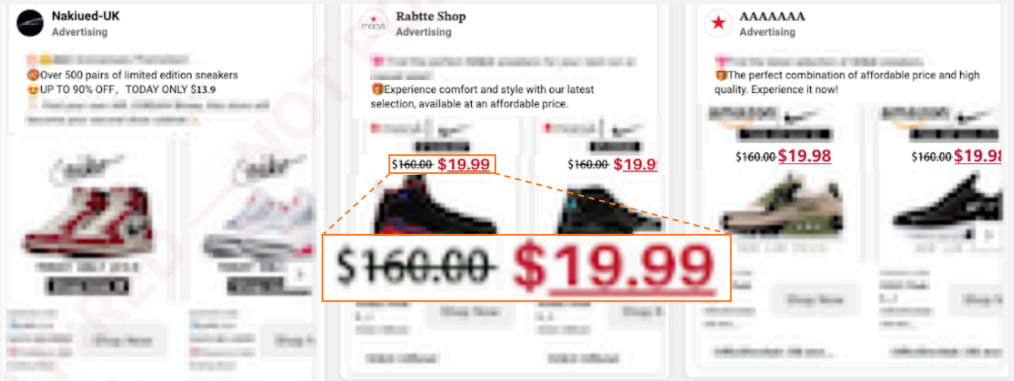
Source: Recorded Future
Recorded Future says Facebook occasionally detected the ads and blocked them, demonstrating that the ad platform’s anti-fraud algorithms were effective in some cases.
“Facebook Ads occasionally blocked the scam advertisements and ultimately blocked the account responsible for the ad campaign, indicating that the service’s fraud-detection algorithms are at least partially effective,” explains Record Future’s report.
“However, the short life of the actual scam domains suggests the ad campaigns were likely also designed to be short-lived, indicating their operators’ intention to attract and defraud their victims quickly.”
“This tactic is more likely to be effective when scam advertising campaigns are operated at scale, as was the case for this campaign.”
To evade detection by researchers and anti-fraud firms, the landing pages are only accessible via mobile platforms or when they were referred from Facebook. If the URL to a fake web shop is inputted manually on the desktop or is missing the referrer header, the page returns a 404 error, as shown below.
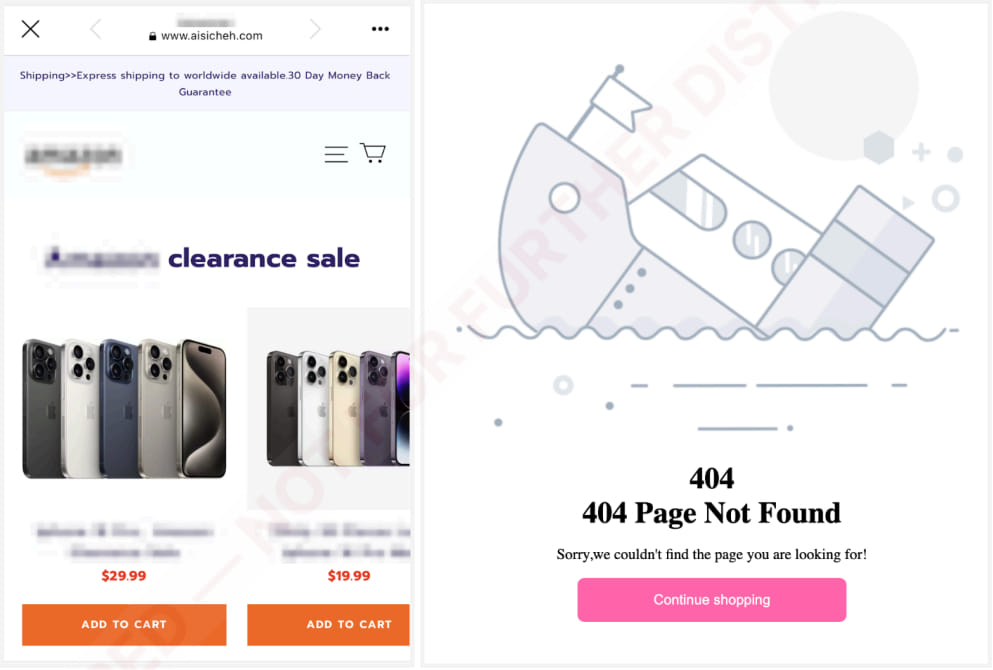
Source: Recorded Future
This screening prevents immediate detection and takedowns, increasing Facebook users’ exposure to the risk.
Also, the constant refresh of short-lived domains used for the fraudulent online stores creates another challenge, as the malicious network is constantly shifting from old sites to new sites at a rapid pace.
Common indicators for the fraud campaign are the website’s use of oss[.]eriakos[.]com as a CDN, domains registered with Alibaba Cloud Computing, and the use of the IP addresses 47.251.50[.]19 and 47.251.129[.]84.
BleepingComputer found malware uploaded to VirusTotal [1, 2] communicating with these IP addresses. However, whether these malware are from the same threat actors or other cybercriminals using shared infrastructure is unknown.
While many of the fraud ring’s websites are no longer in operation, Recorded Future shared samples of advertisements with BleepingComputer from as recent as two days ago, demonstrating that the campaign is still active.
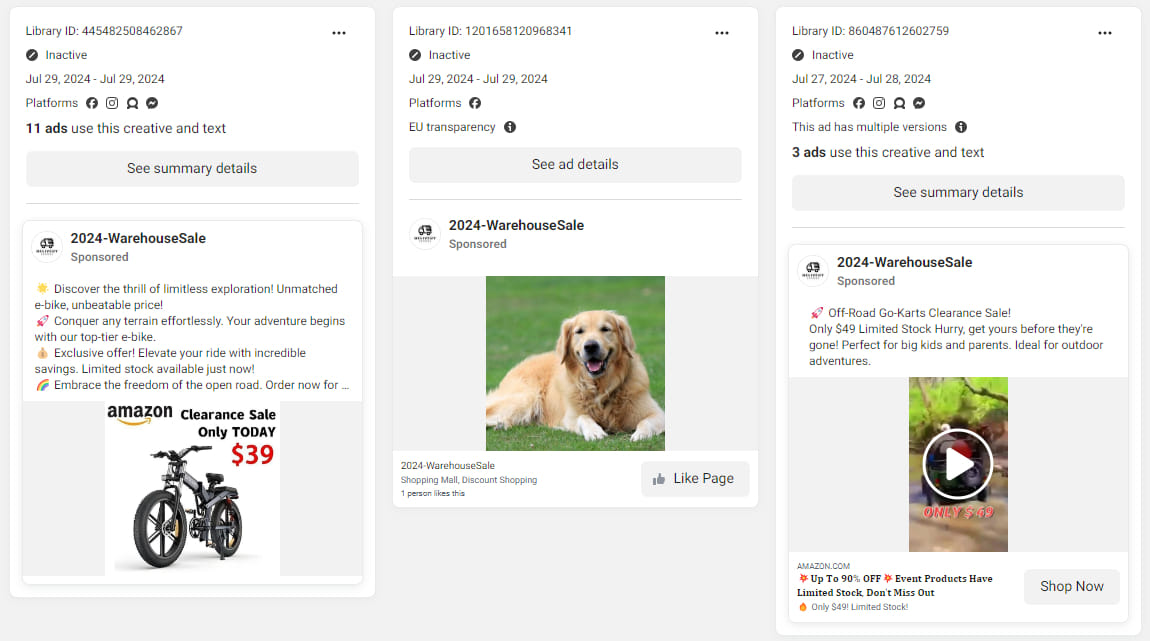
Source: BleepingComputer
In May 2024, researchers from SRLabs discovered another online fraud network, “BogusBazaar,” which is also believed to be operated out of China.
Recorded Future told BleepingComputer that they notified Meta about the fraudulent advertisements before they published their report.
BleepingComputer also asked Meta about the campaign and will update the story if we hear back.
Shop safely
Fraud campaigns like this can hurt consumers in multiple ways, including causing long-term fraudulent purchases on credit cards.
When consumers purchase the products on the fake sites, their cards are charged, allowing the threat actors to steal their money. However, the threat actors now also have your credit card information, which is commonly sold on dark web marketplaces for other threat actors to use for fraud.
Therefore, it is essential to shop safely online and research before purchasing from unknown sites.
Furthermore, ads on large platforms like Facebook may carry a false sense of legitimacy, causing users to make rushed decisions to purchase what appears to be an amazing deal.
However, users must remember that despite all the protection mechanisms on social media sites, scammers still find windows of opportunity to promote fake sites.
Before proceeding to a purchase and entering your sensitive information on the order page, run a background check on the electronic shop, read user reviews, check for the existence of terms of conditions, and ensure the domain you’re on uses HTTPS.
Performing these checks on mobile may be more difficult, which likely explains why the crooks target mobile users, so it is important to research any website you provide credit card details.
If there are any suspicious signs or a lack of search results about the site, it is likely a fake web shop created to steal your credit cards and personal information and should be avoided.

Source link
lol
Image: Midjourney A malicious fraud campaign dubbed “ERIAKOS” promotes more than 600 fake web shops through Facebook advertisements to steal visitors’ personal and financial information. The sites promote products from well-known brands and include significant discounts to draw in visitors but are only accessible via mobile devices to evade detection by security scanners. Recorded Future…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
