StackExchange abused to spread malicious PyPi packages as answers
by nlqip

Threat actors uploaded malicious Python packages to the PyPI repository and promoted them through the StackExchange online question and answer platform.
The packages are named ‘spl-types,’ ‘raydium,’ ‘sol-structs,’ ‘sol-instruct,’ and ‘raydium-sdk’ and download scripts that steal sensitive data from the browser, messaging apps (Telegram, Signal, Session), and cryptocurrency wallet details (Exodus, Electrum, Monero).
The info-stealing malware can also exfiltrate files with specific keywords as well as take screenshots, and sends all the data to a Telegram channel.
Researchers at application security testing company Checkmarx say that while the packages were uploaded to PyPI on June 25 but received the malcicious component in an update on July 3.
The packages are no longer on PyPI they have already been downloaded 2082 times.
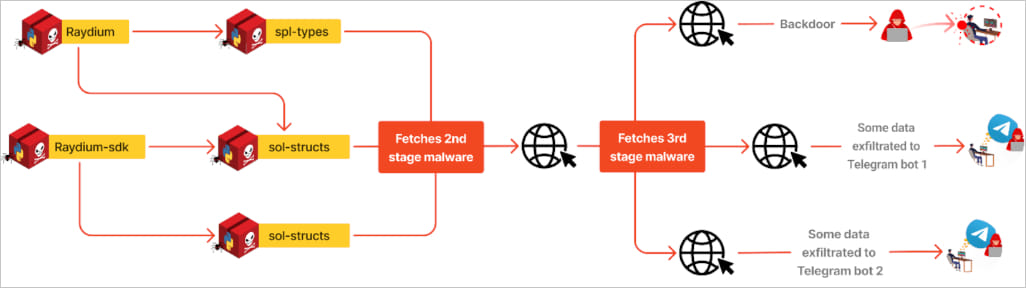
Source: Checkmarx
Abusing StackExchange
According to Checkmarx’s investigation, the attackers specifically targeted users involved in the Raydium and Solana blockchain projects.
The fact that Raydium does not have a Python library created an exploitation opportunity for the attackers, who used the name for their package without having to resort to typosquatting or other deception techniques.
To promote the packages to the right targets, the attackers created accounts on StackExchange and left comments under popular threads containing links to the malicious packages.
The chosen topics were related to the package names, and the answers given were of high quality, so victims could be tempted download the dangerous packages.
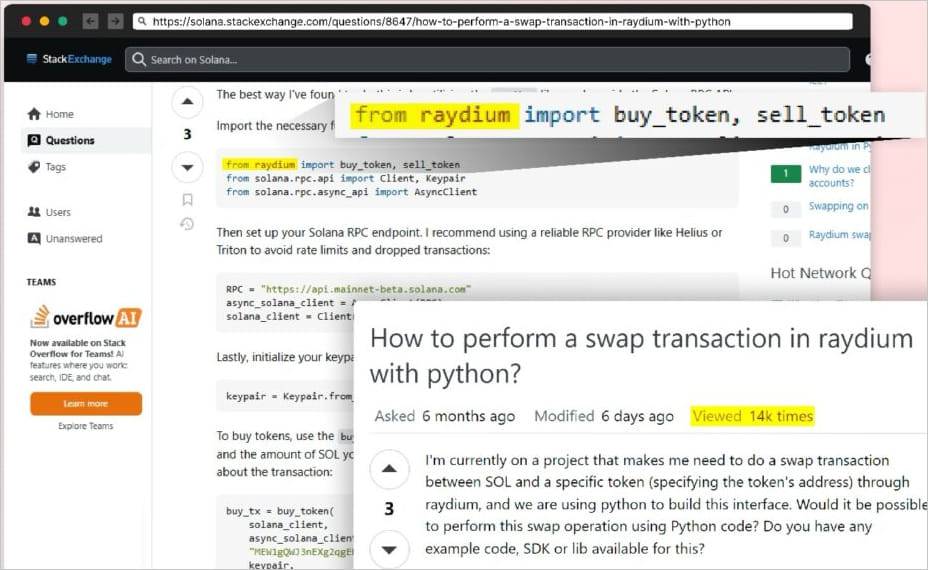
Source: Checkmarx
With over two thousand potential infections, estimating the impact of this campaign is difficult, but Checkmarx researchers presented a couple of victim examples in their report.
One case concerns an IT employee who had his Solana cryptocurrency wallet drained as a result of the infection.
In the second example, the malware captured a screenshot of the victim’s private key, which can be used to bypass MFA protections and hijack accounts even without the password.
Notably, that screenshot shows that Windows Virus and Threat Protection scans failed to catch the threat running on the victim’s device.
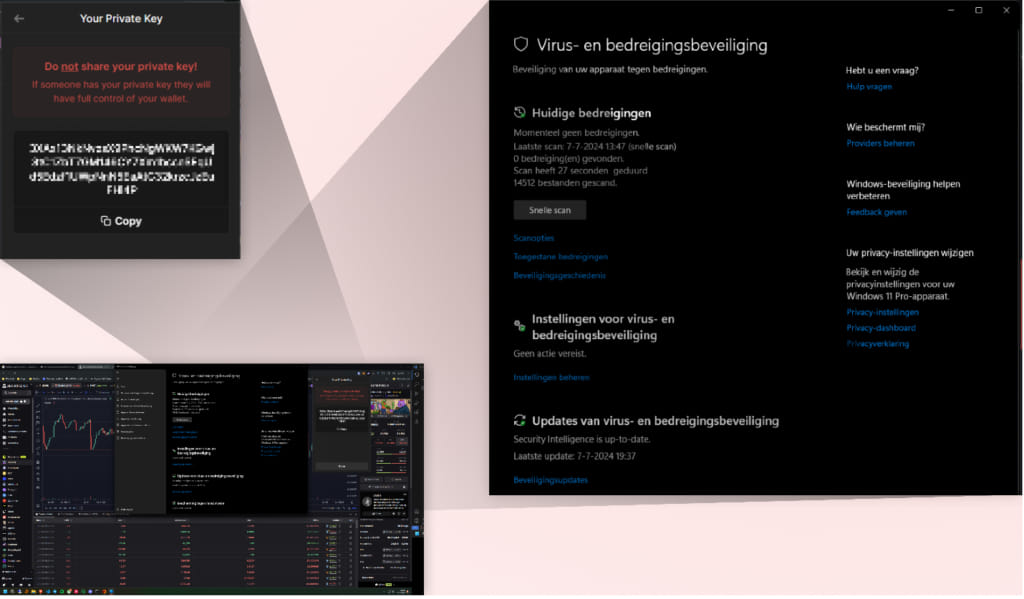
Source: Checkmarx
This tactic has been used in the past. A similar case was reported by Sonatype in May 2024 and involved promoting malicious Python packages on PyPI via StackOverflow answers.
Most software developers are helpful individuals, ready to whip up a script, or point to one that can make things easier. However, using a script from a legitimate platform is not enough as the author should also be trustworthy.
Even so, inspecting the code before using it is the best way to make sure that it has not been modified at a later time for malicious purposes, as it happened in the campaign described by Checkmarx.
Source link
lol
Threat actors uploaded malicious Python packages to the PyPI repository and promoted them through the StackExchange online question and answer platform. The packages are named ‘spl-types,’ ‘raydium,’ ‘sol-structs,’ ‘sol-instruct,’ and ‘raydium-sdk’ and download scripts that steal sensitive data from the browser, messaging apps (Telegram, Signal, Session), and cryptocurrency wallet details (Exodus, Electrum, Monero). The info-stealing malware can also exfiltrate files…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
