Author: nlqip
ESET Research ESET researchers discuss how they uncovered a zero-day Telegram for Android exploit that allowed attackers to send malicious files posing as videos 17 Sep 2024 • , 1 min. read Telegram, with nearly a billion monthly users, is a juicy target for cybercriminals, especially if they can exploit a zero-day vulnerability to spread…
Read MoreConfluent Launches OEM Program To Help ISV And MSP Partners Build Data Streaming Into Their Offerings
by nlqip
Confluent also discloses investments in two regional systems integration partners who are developing leading-edge data integration and migration expertise and practices. Data streaming tech developer Confluent has launched an OEM channel program to recruit managed service providers, cloud service providers and independent software vendors to build the Confluent platform within their software and service offerings.…
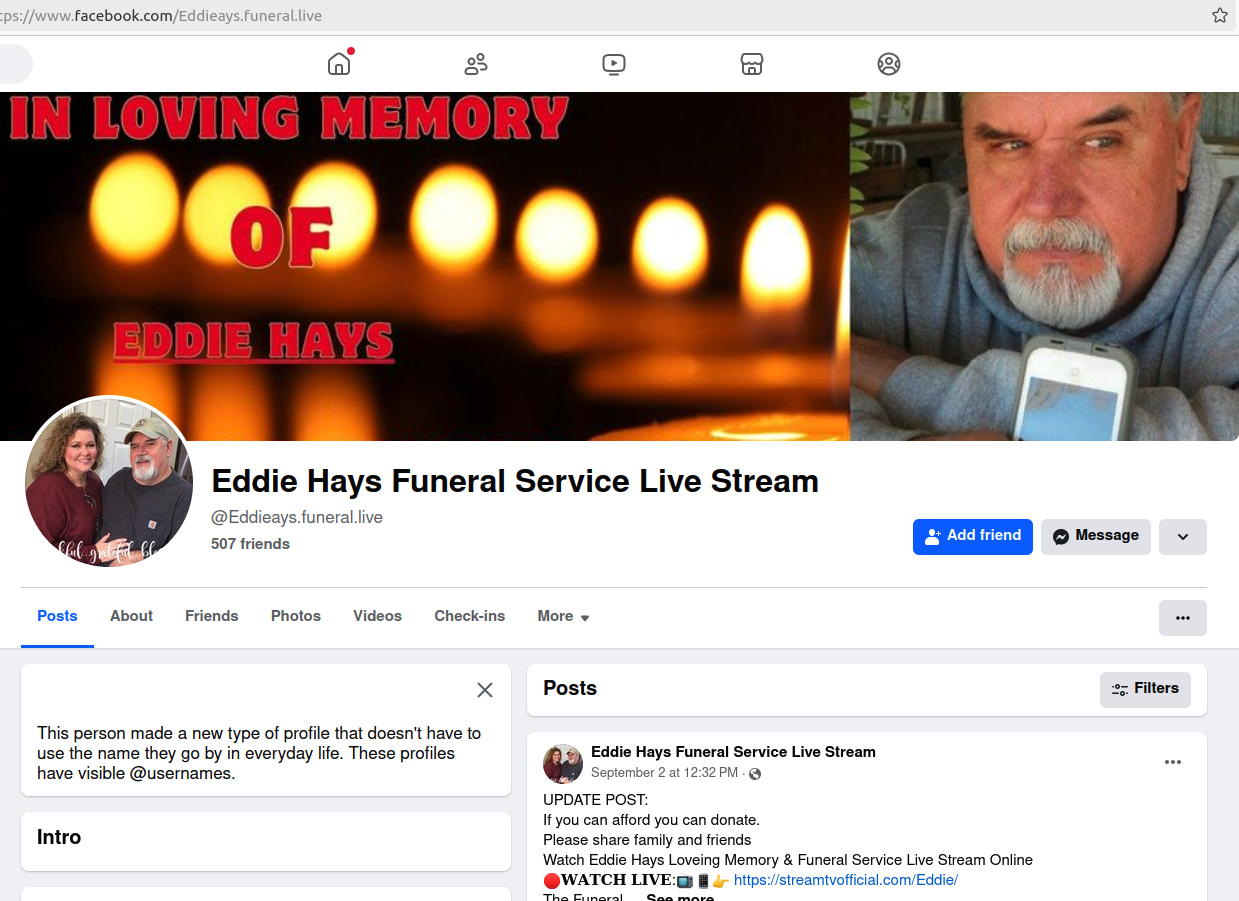
Read MoreScammers are flooding Facebook with groups that purport to offer video streaming of funeral services for the recently deceased. Friends and family who follow the links for the streaming services are then asked to cough up their credit card information. Recently, these scammers have branched out into offering fake streaming services for nearly any kind…
Read MoreA New Edge For HPE: Why The Nvidia AI-Ready ProLiant DL145 Gen11 Server Is A ‘Big Breakthrough’
by nlqip
Hewlett Packard Enterprise is pushing the edge computing price performance envelope with a 2U Nvidia AI Ready ProLiant DL145 Gen11 server priced starting at just $2,065 for a configure to order chassis. A ‘Big Breakthrough’ At The Edge Hewlett Packard Enterprise’s new 2U Nvidia AI ready ProLiant DL145 is aimed at once and for all…
Read More“We’re going to do ourselves a disservice … as an industry if we push people too fast into AI and we don’t give real solutions,” Insight SVP Stephen Moss tells CRN. Artificial intelligence as a service. Managed AI. AI assurance. Solution providers are at work sorting through new practices and new ways to not only…
Read More6 Big Intel Changes, Wins Outlined By CEO: AWS Chip Deal, Independent Foundry, Factory Delays
by nlqip
In a Monday letter to employees, Intel CEO Pat Gelsinger outlined changes that will help the beleaguered chipmaker save billions of dollars and bounce back financially while highlighting a new multibillion-dollar chip deal with Amazon Web Services. Intel CEO Pat Gelsinger said the company plans to turn its contract chip manufacturing business into an independent…
Read MoreThe evolution of software always catches us by surprise. I remember betting against the IBM computer Deep Blue during its chess match against the grandmaster Garry Kasparov in 1997, only to be stunned when the machine claimed victory. Fast forward to today, would we have imagined just three years ago that a chatbot could write…
Read MoreSep 18, 2024Ravie LakshmananCyber Espionage / Malware A North Korea-linked cyber-espionage group has been observed leveraging job-themed phishing lures to target prospective victims in energy and aerospace verticals and infect them with a previously undocumented backdoor dubbed MISTPEN. The activity cluster is being tracked by Google-owned Mandiant under the moniker UNC2970, which it said overlaps…
Read MoreTenable Research Uncovers Thousands of Vulnerable Cyber Assets Amongst Southeast Asia’s Financial Sector
by nlqip
New research conducted by Tenable®, Inc., the exposure management company, has uncovered more than 26,500 potential internet-facing assets among Southeast Asia’s top banking, financial services and insurance (BFSI) companies by market capitalisation across Indonesia, Malaysia, the Philippines, Singapore, Thailand and Vietnam. On July 15, 2024, Tenable examined the external attack surface of over 90 BFSI…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/introducing-levelblues-24-7-managed-threat-detection-and-response-service-for-government” on this server. Reference #18.edd7ce17.1726655008.76eeaee https://errors.edgesuite.net/18.edd7ce17.1726655008.76eeaee Source link lol
Read MoreRecent Posts
- Tor needs 200 new WebTunnel bridges to fight censorship
- What Is a SOC Report, and Why Does Your Business Need One?
- Affordable and Effective: Best EDR Solutions for Small Business Affordable and Effective: Best EDR Solutions for Small Business
- Top Features to Look for in Endpoint Detection and Response Software Top Features to Look for in Endpoint Detection and Response Software
- What Does EDR Stand For in Threat Management? What Does EDR Stand For in Threat Management?