Author: nlqip
Access Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/tackling-the-unique-cybersecurity-challenges-of-online-learning-platforms” on this server. Reference #18.ddd7ce17.1726501433.90741bc5 https://errors.edgesuite.net/18.ddd7ce17.1726501433.90741bc5 Source link lol
Read MoreIvanti has released a security update addressing an OS command injection vulnerability (CVE-2024-8190) affecting Ivanti Cloud Services Appliance (CSA) 4.6 (all versions before patch 519). A cyber threat actor could exploit this vulnerability to take control of an affected system. At this time, Ivanti has confirmed limited exploitation and urges its customers using the affected…
Read MoreCISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-43461 Microsoft Windows MSHTML Platform Spoofing Vulnerability CVE-2024-6670 Progress WhatsUp Gold SQL Injection Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD)…
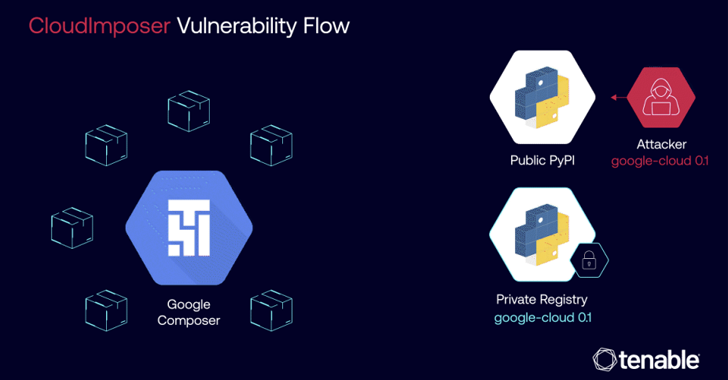
Read More‘CloudImposer could have allowed attackers to conduct a massive supply chain attack by compromising the Google Cloud Platform’s Cloud Composer service for orchestrating software pipelines,’ says Tenable security researcher Liv Matan. Google has patched a critical security flaw inside its Google Cloud Platform Composer tool that could have enabled hackers to achieve remote execution on…
Read MoreOpenText–eDirectory Possible Insertion of Sensitive Information into Log File Vulnerability in eDirectory has been discovered in OpenText™ eDirectory 9.2.4.0000. 2024-09-12 6.5 CVE-2021-22533 security@opentext.com n/a–n/a ONLYOFFICE Docs before 8.0.1 allows XSS because a macro is an immediately-invoked function expression (IIFE), and therefore a sandbox escape is possible by directly calling the constructor of the Function object.…
Read MoreD-Link has fixed critical vulnerabilities in three popular wireless router models that allow remote attackers to execute arbitrary code or access the devices using hardcoded credentials. The impacted models are popular in the consumer networking market, especially among users looking for high-end WiFi 6 routers (DIR-X) and mesh networking systems (COVR). The bulletin lists five…
Read More“This deal is a big accelerant for the NWN platform which is consistent with the approach we have taken over the last five years that has allowed us to quadruple the company from less than $300 million to more than $1 billion,” said NWN Senior Vice President of Corporate Development Matt Curran. NWN Carousel has…
Read MoreUnisys, Fusion Connect, Impact Networking, Tenable, Confluent and Thales are among the vendors to list open positions for channel-related roles. This month, Unisys, Fusion Connect and Impact Networking are among the solution providers to list open positions while Tenable, Confluent and Thales are among the vendors to list open positions for channel-related roles. CRN has…
Read MoreSep 16, 2024Ravie LakshmananFinancial Security / Malware Cybersecurity researchers are continuing to warn about North Korean threat actors’ attempts to target prospective victims on LinkedIn to deliver malware called RustDoor. The latest advisory comes from Jamf Threat Labs, which said it spotted an attack attempt in which a user was contacted on the professional social…
Read MoreSep 16, 2024Ravie LakshmananCloud Security / Vulnerability A now-patched critical security flaw impacting Google Cloud Platform (GCP) Composer could have been exploited to achieve remote code execution on cloud servers by means of a supply chain attack technique called dependency confusion. The vulnerability has been codenamed CloudImposer by Tenable Research. “The vulnerability could have allowed…
Read MoreRecent Posts
- Tor needs 200 new WebTunnel bridges to fight censorship
- What Is a SOC Report, and Why Does Your Business Need One?
- Affordable and Effective: Best EDR Solutions for Small Business Affordable and Effective: Best EDR Solutions for Small Business
- Top Features to Look for in Endpoint Detection and Response Software Top Features to Look for in Endpoint Detection and Response Software
- What Does EDR Stand For in Threat Management? What Does EDR Stand For in Threat Management?