Author: nlqip
North Korean threat actors have leveraged a fake Windows video conferencing application impersonating FreeConference.com to backdoor developer systems as part of an ongoing financially-driven campaign dubbed Contagious Interview. The new attack wave, spotted by Singaporean company Group-IB in mid-August 2024, is yet another indication that the activity is also leveraging native installers for Windows and…
Read MoreCisco’s site for selling company-themed merchandise is currently offline and under maintenance due to hackers compromising it with JavaScript code that steals sensitive customer details provided at checkout. Cisco’s site for selling company-themed merchandise is currently offline and under maintenance due to a compromise with JavaScript code that steals sensitive details provided at checkout. It…
Read MoreGoogle has released the September 2024 Android security updates to fix 34 vulnerabilities, including CVE-2024-32896, an actively exploited elevation of privilege flaw that was previously fixed on Pixel devices. The high-severity vulnerability is related to a logic error in the code, which allows an attacker to bypass certain protections on Android and elevate their privileges…
Read More‘We have a lot of prospects interested in SuperOps, and my focus will be on reaching out to them, engaging in meaningful conversations and understanding their needs,’ says Brandi Crown, SuperOps’ new U.S. head of sales. ‘We aim to help MSPs not only manage their operations more effectively but also to capitalize on tools and…
Read MoreSep 04, 2024Ravie LakshmananVulnerability / Mobile Security Google has released its monthly security updates for the Android operating system to address a known security flaw that it said has come under active exploitation in the wild. The high-severity vulnerability, tracked as CVE-2024-32896 (CVSS score: 7.8), relates to a case of privilege escalation in the Android…
Read MoreAI SPERA, a leading Cyber Threat Intelligence (CTI) company, has achieved PCI DSS v4.0 certification for its flagship search engine solution, Criminal IP. This accomplishment builds on last year’s attainment of PCI DSS v3.2.1 (Payment Card Industry Data Security Standard) certification and represents a significant milestone in the company’s ongoing efforts to strengthen security, further…
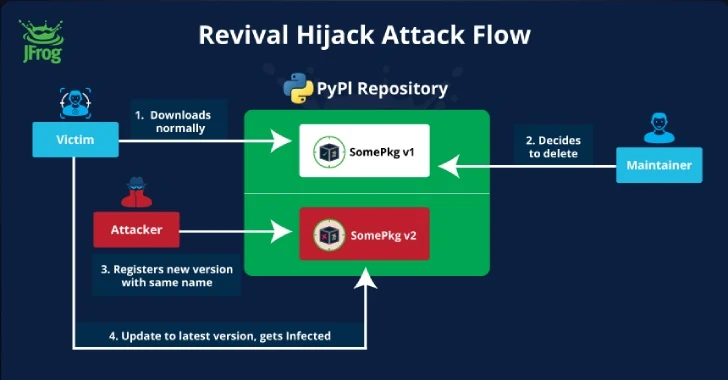
Read MoreThreat actors are utilizing an attack called “Revival Hijack,” where they register new PyPi projects using the names of previously deleted packages to conduct supply chain attacks. The technique “could be used to hijack 22K existing PyPI packages and subsequently lead to hundreds of thousands of malicious package downloads,” the researchers say. Hijacking popular projects…
Read More‘Our partnership with IBM reinforces our commitment to innovation and our conviction in the tremendous benefit of QRadar customers adopting Cortex XSIAM for a robust, data-driven security platform that offers transformative efficiency and effectiveness in defending against evolving cyberthreats,’ says Palo Alto Networks CEO Nikesh Arora. Cybersecurity superstar Palo Alto Networks completed its $500 million…
Read More“The problem is that while this is being discussed, attackers can already use this method to gain code execution on many PyPI users as we’ve demonstrated.” Advice for CISOs, app leaders Infosec leaders should warn their staff that a new version of a package can potentially include malicious code, he said, even if the last…
Read MoreSep 04, 2024Ravie Lakshmanan A new supply chain attack technique targeting the Python Package Index (PyPI) registry has been exploited in the wild in an attempt to infiltrate downstream organizations. It has been codenamed Revival Hijack by software supply chain security firm JFrog, which said the attack method could be used to hijack 22,000 existing…
Read MoreRecent Posts
- New Rockstar 2FA phishing service targets Microsoft 365 accounts
- Russia arrests cybercriminal Wazawaka for ties with ransomware gangs
- Bologna FC confirms data breach after RansomHub ransomware attack
- New Windows Server 2012 zero-day gets free, unofficial patches
- Cybersecurity Snapshot: AI Security Roundup: Best Practices, Research and Insights