Author: nlqip
The report added that the FudModule rootkit has historically been shared between Citrine Sleet and Diamond Sleet (formerly Zinc), another North Korean threat actor known to target media, defense, and information technology (IT) industries globally. RCE to deliver FudModule The report explained that victims were directed to a Citrine Sleet-controlled exploit domain voyagorclub[.]space. While the…
Read MoreSQL Injection Attack on Airport Security Interesting vulnerability: …a special lane at airport security called Known Crewmember (KCM). KCM is a TSA program that allows pilots and flight attendants to bypass security screening, even when flying on domestic personal trips. The KCM process is fairly simple: the employee uses the dedicated lane and presents their…
Read MoreSep 02, 2024The Hacker NewsVulnerability Management / Webinar The world of cybersecurity is in a constant state of flux. New vulnerabilities emerge daily, and attackers are becoming more sophisticated. In this high-stakes game, security leaders need every advantage they can get. That’s where Artificial Intelligence (AI) comes in. AI isn’t just a buzzword; it’s a…
Read MoreA former IT engineer is facing federal charges in the United States after his former employer found it had been locked out of its computer systems and received a demand for $750,000. At approximately 4pm EST on November 25, 2023, staff at an industrial company headquartered in Somerset County, New Jersey, began to receive password…
Read MoreUsing Anti Data Exfiltration (ADX) to Stop Ransomware and Other Threats to Data Dr. EDWARD AMOROSO, FOUNDER & CEO, TAG This series of blogs developed by TAG Infosphere highlights a powerful new cybersecurity solution known as Anti Data Exfiltration (ADX) which provides on-device data security and threat protection. Commercial vendor BlackFog pioneered ADX which is…
Read MoreSep 02, 2024The Hacker NewsCybercrime / CISO Insights The FBI and CISA Issue Joint Advisory on New Threats and How to Stop Ransomware Note: on August 29, the FBI and CISA issued a joint advisory as part of their ongoing #StopRansomware effort to help organizations protect against ransomware. The latest advisory, AA24-242A, describes a new…
Read MoreThere’s a cultural barrier to investing proactively in cybersecurity, Johnson admits. “We are a reactionary society, but cybersecurity is finally being seen for what it is: an investment. An ounce of prevention is worth a pound of cure.” 8. Test, test, and test again “A lot of people are approaching backups from a backup point…
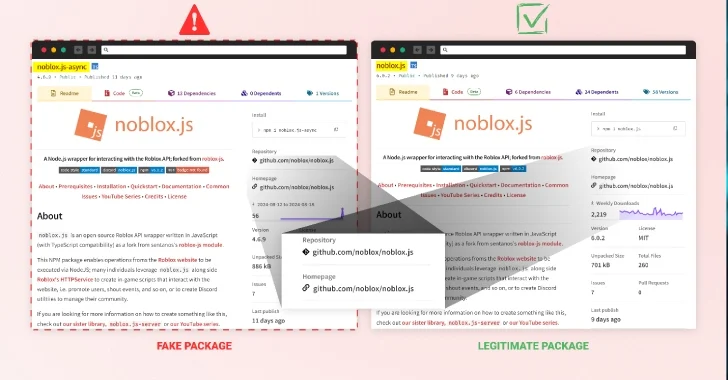
Read MoreSep 02, 2024Ravie LakshmananSoftware Security / Malware Roblox developers are the target of a persistent campaign that seeks to compromise systems through bogus npm packages, once again underscoring how threat actors continue to exploit the trust in the open-source ecosystem to deliver malware. “By mimicking the popular ‘noblox.js’ library, attackers have published dozens of packages…
Read MoreImage: Midjourney A new ransomware-as-a-service (RaaS) operation named Cicada3301 has already listed 19 victims on its extortion portal, as it quickly attacked companies worldwide. The new cybercrime operation is named after the mysterious 2012-2014 online/real-world game that involved elaborate cryptographic puzzles and used the same logo for promotion on cybercrime forums. However, it is unlikely…
Read MoreThe popular Docker-OSX project has been removed from Docker Hub after Apple filed a DMCA (Digital Millennium Copyright Act) takedown request, alleging that it violated its copyright. Docker-OSX is an open-source project created by security researcher Sick.Codes that allows for the virtualization of macOS on non-Apple hardware. It can be hosted on any system that…
Read MoreRecent Posts
- New Rockstar 2FA phishing service targets Microsoft 365 accounts
- Russia arrests cybercriminal Wazawaka for ties with ransomware gangs
- Bologna FC confirms data breach after RansomHub ransomware attack
- New Windows Server 2012 zero-day gets free, unofficial patches
- Cybersecurity Snapshot: AI Security Roundup: Best Practices, Research and Insights