Author: nlqip
‘Amazon’s collaboration with Anthropic does not raise any competition concerns or meet the CMA’s own threshold for review,’ says an Amazon spokesperson regarding the investigation by the U.K. Competition and Markets Authority. A U.K. antitrust watchdog agency said it has “sufficient information” to start an investigation into whether Amazon’s $4 billion investment and partnership with…
Read MoreOver $40 Million Recovered and Arrests Made Within Days After Firm Discovers Business Email Compromise Scam
by nlqip
According to the FBI, billions of dollars have been lost through Business Email Compromise (BEC) attacks in recent years, so you may well think that there is little in the way of good news. However, it has been revealed this week that police managed to recover more than US $40 million snatched in a recent…
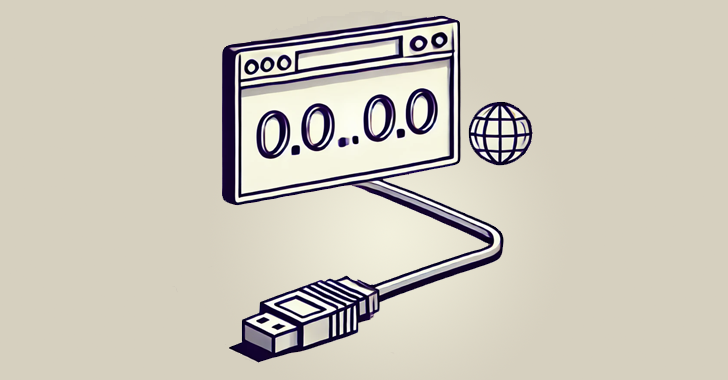
Read MoreAug 08, 2024Ravie LakshmananVulnerability / Browser Security Cybersecurity researchers have discovered a new “0.0.0.0 Day” impacting all major web browsers that malicious websites could take advantage of to breach local networks. The critical vulnerability “exposes a fundamental flaw in how browsers handle network requests, potentially granting malicious actors access to sensitive services running on local…
Read More‘I don’t think we’re ever done when it comes to improving the platform. I think it can continue to get better year over year as we master automation with MSPs’ says Aharon Chernin, Rewst founder and CEO. Automation platform company Rewst has secured $45 million in funding to accelerate the pace of innovation in its…
Read MoreAmerican building security giant ADT confirmed it suffered a data breach after threat actors leaked allegedly stolen customer data on a popular hacking forum. ADT is a public American company that specializes in security and smart home solutions for residential and small business customers. The firm employs 14,300 people, has an annual revenue of $4.98…
Read MoreMoreover, such attacks could disrupt operations by compromising critical infrastructure, leading to downtime and financial losses. Industries with stringent compliance requirements, such as financial services, healthcare, and the public sector, are particularly vulnerable. A successful downgrade attack in these sectors could result in regulatory penalties and significant damage to an organization’s reputation and customer trust.”…
Read MoreAug 08, 2024The Hacker NewsCyber Threat Management The last few years have seen more than a few new categories of security solutions arise in hopes of stemming a never-ending tidal wave of risks. One of these categories is Automated Security Validation (ASV), which provides the attacker’s perspective of exposures and equips security teams to continuously…
Read MoreThe DPC also plans to refer the matter to the European Data Protection Board. Kaur noted that X, already with a history of GDPR non-compliance, now faces heightened pressure to improve data protection practices, enhance transparency, and restore user trust, particularly in Europe. The DPC’s actions also underscore a broader trend of stringent data protection…
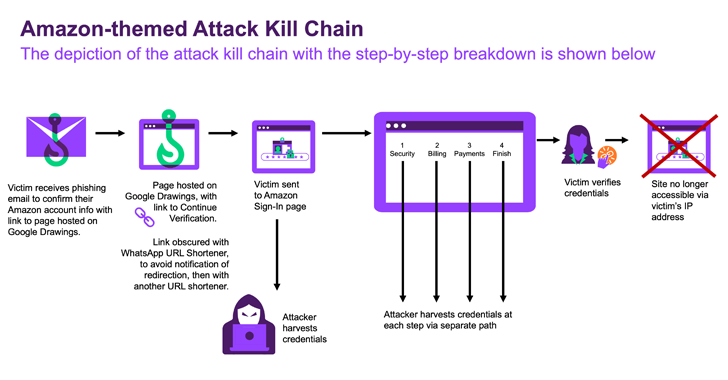
Read MoreAug 08, 2024Ravie LakshmananNetwork Security / Cloud Security Cybersecurity researchers have discovered a novel phishing campaign that leverages Google Drawings and shortened links generated via WhatsApp to evade detection and trick users into clicking on bogus links designed to steal sensitive information. “The attackers chose a group of the best-known websites in computing to craft…
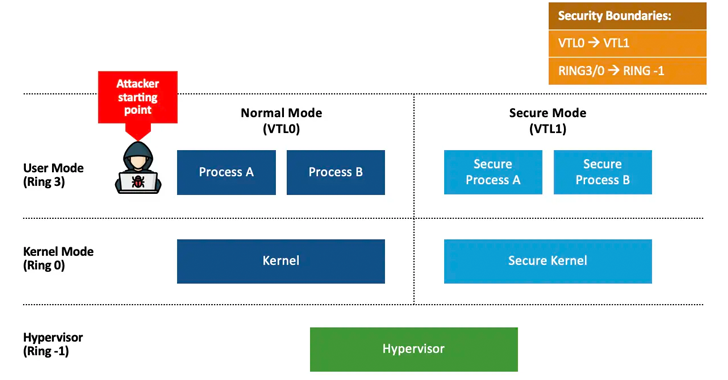
Read MoreAug 08, 2024Ravie LakshmananWindows Security / Vulnerability Microsoft said it is developing security updates to address two loopholes that it said could be abused to stage downgrade attacks against the Windows update architecture and replace current versions of the Windows files with older versions. The vulnerabilities are listed below – CVE-2024-38202 (CVSS score: 7.3) –…
Read MoreRecent Posts
- U.S. Citizens’ Data Allegedly on Sale
- New Cisco ASA and FTD features block VPN brute-force password attacks
- New Windows Driver Signature bypass allows kernel rootkit installs
- Over 70 zero-day flaws get hackers $1 million at Pwn2Own Ireland
- Four REvil Ransomware Members Sentenced in Rare Russian Cybercrime Convictions