Author: nlqip
New Patent Application for Car-to-Car Surveillance Ford has a new patent application for a system where cars monitor each other’s speeds, and then report then to some central authority. Slashdot thread. Tags: cars, patents, police Posted on August 5, 2024 at 7:07 AM • 0 Comments Sidebar photo of Bruce Schneier by Joe MacInnis. Source…
Read MoreIncident response is a structured approach to managing and addressing security breaches or cyber-attacks. Security teams must overcome challenges such as timely detection, comprehensive data collection, and coordinated actions to enhance readiness. Improving these areas ensures a swift and effective response, minimizing damage and restoring normal operations quickly. Challenges in incident response Incident response presents…
Read More“I believe the fix, sorry, I mean workaround for this is to use the Secret Key from the Identity Provider and manually type this into the Authenticator app during setup,” the user wrote. “Unfortunately, this is not very helpful in an enterprise environment, especially when the average end user rarely knows anything about the inner…
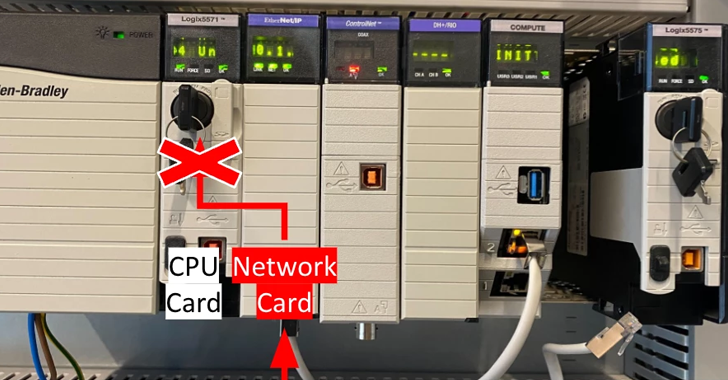
Read MoreAug 05, 2024Ravie LakshmananNetwork Security / Vulnerability A high-severity security bypass vulnerability has been disclosed in Rockwell Automation ControlLogix 1756 devices that could be exploited to execute common industrial protocol (CIP) programming and configuration commands. The flaw, which is assigned the CVE identifier CVE-2024-6242, carries a CVSS v3.1 score of 8.4. “A vulnerability exists in…
Read MoreAs organizations increasingly seek to support and secure more remote network connections, many are rethinking the traditional VPN. Many VPN alternatives exist to help secure remote access — mesh VPNs chief among them. Mesh virtual private networks (VPNs) use a peer-to-peer architecture that can theoretically be less expensive than traditional VPN approaches. VPNs, which are estimated…
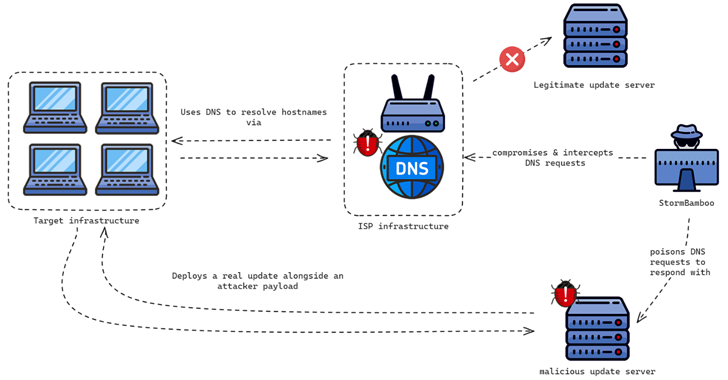
Read MoreAug 05, 2024Ravie LakshmananBrowser Security / Windows Security The China-linked threat actor known as Evasive Panda compromised an unnamed internet service provider (ISP) to push malicious software updates to target companies in mid-2023, highlighting a new level of sophistication associated with the group. Evasive Panda, also known by the names Bronze Highland, Daggerfly, and StormBamboo,…
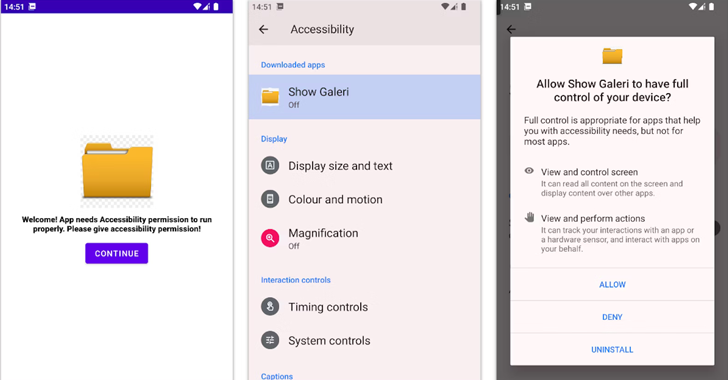
Read MoreAug 05, 2024Ravie LakshmananMobile Security / Financial Security Cybersecurity researchers have discovered a new Android banking trojan called BlankBot targeting Turkish users with an aim to steal financial information. “BlankBot features a range of malicious capabilities, which include customer injections, keylogging, screen recording and it communicates with a control server over a WebSocket connection,” Intel…
Read MoreA massive Magniber ransomware campaign is underway, encrypting home users’ devices worldwide and demanding thousand-dollar ransoms to receive a decryptor. Magniber launched in 2017 as a successor to the Cerber ransomware operation when it was spotted being distributed by the Magnitude exploit kit. Since then, the ransomware operation has seen bursts of activity over the…
Read MoreA Chinese hacking group tracked as StormBamboo has compromised an undisclosed internet service provider (ISP) to poison automatic software updates with malware. Also tracked as Evasive Panda, Daggerfly, and StormCloud, this cyber-espionage group has been active since at least 2012, targeting organizations across mainland China, Hong Kong, Macao, Nigeria, and various Southeast and East Asian countries. On…
Read MoreA novel Linux Kernel cross-cache attack named SLUBStick has a 99% success in converting a limited heap vulnerability into an arbitrary memory read-and-write capability, letting the researchers elevate privileges or escape containers. The discovery comes from a team of researchers from the Graz University of Technology who demonstrated the attack on Linux kernel versions 5.9 and 6.2 (latest) using…
Read MoreRecent Posts
- U.S. Citizens’ Data Allegedly on Sale
- New Cisco ASA and FTD features block VPN brute-force password attacks
- New Windows Driver Signature bypass allows kernel rootkit installs
- Over 70 zero-day flaws get hackers $1 million at Pwn2Own Ireland
- Four REvil Ransomware Members Sentenced in Rare Russian Cybercrime Convictions