Author: nlqip
‘The more willingness to have conversations and to do research, [that will] help sellers down the line as they think about the right fit for them,’ says Sydney Hockett, vice president of Evergreen Services Group. When it comes to selling an MSP business, owners have a lot of options. Merging or selling to a holding…
Read MoreThe Iranian-backed MuddyWatter hacking group has partially switched to using a new custom-tailored malware implant to steal files and run commands on compromised systems. Dubbed BugSleep, this new backdoor is still actively being developed and was discovered by analysts at Check Point Research while being distributed via well-crafted phishing lures. The campaign pushes the malware…
Read MoreHacking Scientific Citations Some scholars are inflating their reference counts by sneaking them into metadata: Citations of scientific work abide by a standardized referencing system: Each reference explicitly mentions at least the title, authors’ names, publication year, journal or conference name, and page numbers of the cited publication. These details are stored as metadata, not…
Read MoreAdobe–Bridge Bridge versions 14.0.4, 13.0.7, 14.1 and earlier are affected by an Integer Overflow or Wraparound vulnerability that could result in arbitrary code execution in the context of the current user. Exploitation of this issue requires user interaction in that a victim must open a malicious file. 2024-07-09 7.8 CVE-2024-34139psirt@adobe.com Adobe–InDesign Desktop InDesign Desktop versions…
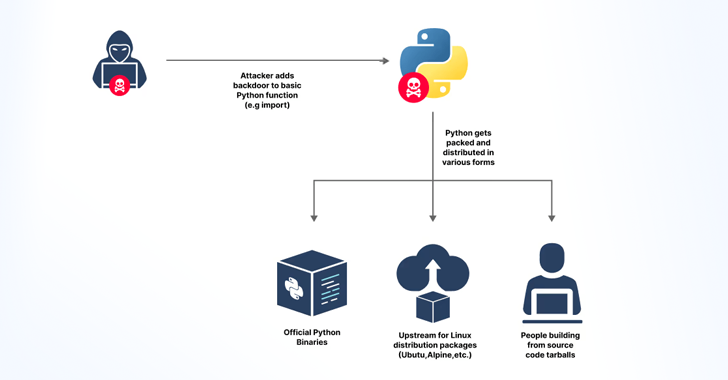
Read MoreJul 15, 2024NewsroomSupply Chain Attack / Cyber Threat Cybersecurity researchers said they discovered an accidentally leaked GitHub token that could have granted elevated access to the GitHub repositories of the Python language, Python Package Index (PyPI), and the Python Software Foundation (PSF) repositories. JFrog, which found the GitHub Personal Access Token, said the secret was…
Read More‘For Google, this would be a shot across the bow at Microsoft and Amazon, making a major bet on the cybersecurity space to complement its flagship GCP offering in the cloud,’ says Wedbush Securities analyst Dan Ives. Here are five key things to know about Google’s potential $23 billion bid for red-hot security startup Wiz.…
Read MoreMicrosoft has provided a temporary workaround for a known issue preventing the Microsoft Photos app from launching on some Windows 11 systems. The company says this bug impacts devices running Windows 11 22H2 and 23H2, on which the “Prevent non-admin users from installing packaged Windows apps” or the BlockNonAdminUserInstall Configuration Service provider (CSP) policies are…
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog…
Read MoreThe SEXi ransomware operation, known for targeting VMware ESXi servers, has rebranded under the name APT INC and has targeted numerous organizations in recent attacks. The threat actors started attacking organizations in February 2024 using the leaked Babuk encryptor to target VMware ESXi servers and the leaked LockBit 3 encryptor to target Windows. The cybercriminals…
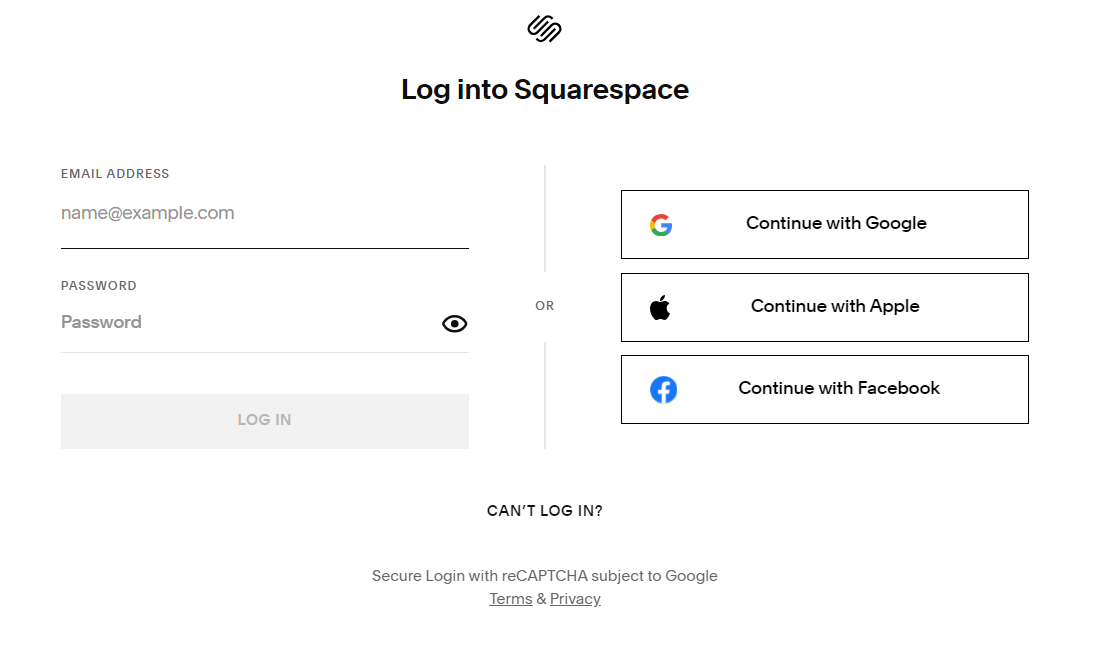
Read MoreAt least a dozen organizations with domain names at domain registrar Squarespace saw their websites hijacked last week. Squarespace bought all assets of Google Domains a year ago, but many customers still haven’t set up their new accounts. Experts say malicious hackers learned they could commandeer any migrated Squarespace accounts that hadn’t yet been registered,…
Read MoreRecent Posts
- Multiple Vulnerabilities in Apple Products Could Allow for Arbitrary Code Execution
- Multiple Vulnerabilities in Siemens InterMesh Subscriber Devices Could Allow for Remote Code Execution
- AMD Boosts Instinct GPU Sales Forecast Again Due To High AI Demand
- New Windows Themes zero-day gets free, unofficial patches
- Kaseya Acquires SaaS Alerts, Unveils Kaseya 365 User