Author: nlqip
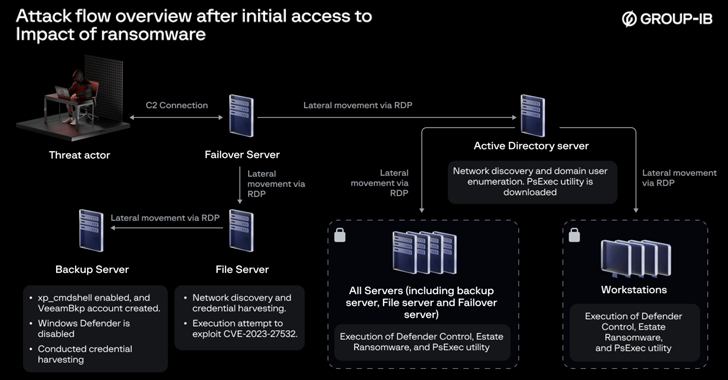
Jul 10, 2024NewsroomData Breach / Malware A now-patched security flaw in Veeam Backup & Replication software is being exploited by a nascent ransomware operation known as EstateRansomware. Singapore-headquartered Group-IB, which discovered the threat actor in early April 2024, said the modus operandi involved the exploitation of CVE-2023-27532 (CVSS score: 7.5) to carry out the malicious…
Read MoreData Protection vs Data Security: The key Differences to Know Data is any firm’s most valuable asset. This could be financial information, intellectual property, trade secrets, research and development data, or customer and employee personal details. But regardless of what type of data firms have, its importance cannot be understated. However, this also makes it…
Read MoreJul 10, 2024The Hacker NewsEndpoint Security / Identity Security It’s the age of identity security. The explosion of driven ransomware attacks has made CISOs and security teams realize that identity protection lags 20 years behind their endpoints and networks. This realization is mainly due to the transformation of lateral movement from fine art, found in…
Read MoreJul 10, 2024NewsroomEndpoint Security / Vulnerability Microsoft has released patches to address a total of 143 security flaws as part of its monthly security updates, two of which have come under active exploitation in the wild. Five out of the 143 flaws are rated Critical, 136 are rated Important, and four are rated Moderate in…
Read MoreThe Problem The “2024 Attack Intelligence Report” from the staff at Rapid7 [1] is a well-researched, well-written report that is worthy of careful study. Some key takeaways are: 53% of the over 30 new vulnerabilities that were widely exploited in 2023 and at the start of 2024 were zero-days. More mass compromise events arose from…
Read MoreJul 10, 2024NewsroomCybersecurity / Phishing Attack Google on Wednesday announced that it’s making available passkeys for high-risk users to enroll in its Advanced Protection Program (APP). “Users traditionally needed a physical security key for APP — now they can choose a passkey to secure their account,” Shuvo Chatterjee, product lead of APP, said. Passkeys are…
Read MoreA covert Russian government-operated social media bot farm that used generative AI to spread disinformation to global users has been disrupted by a joint FBI-international cybersecurity forces operation. Affiliates of a Russian state-sponsored media organization Russia Today (RT), used Meliorator — an AI-enabled bot farm generation and management software–to set up over 1000 X (formerly…
Read MoreGoogle announced today that passkeys are now available for high-risk users when enrolling in the Advanced Protection Program, which provides the strongest level of account security. The Advanced Protection Program is a free service that protects the accounts of users such as activists, journalists, business leaders, and political teams, who are at a higher risk of…
Read MoreA large-scale fraud campaign with over 700 domain names is likely targeting Russian-speaking users looking to purchase tickets for the Summer Olympics in Paris. The operation offers fake tickets to the Olympic Games and appears to take advantage of other major sports and music events. Researchers analyzing the campaign are calling it Ticket Heist and…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/digital-forensics-in-the-age-of-cryptocurrency-investigating-blockchain-and-crypto-crimes” on this server. Reference #18.e6d7ce17.1720605955.746b0c73 https://errors.edgesuite.net/18.e6d7ce17.1720605955.746b0c73 Source link lol
Read MoreRecent Posts
- SOC Audit Requirements: What You Need to Prepare
- Embarking on a Compliance Journey? Here’s How Intruder Can Help
- Researchers Uncover Python Package Targeting Crypto Wallets with Malicious Code
- Trump and Vance Phones Among Alleged Targets of Chinese Hackers
- Multiple Vulnerabilities in Apple Products Could Allow for Arbitrary Code Execution