Author: nlqip
People’s Republic of China (PRC) Ministry of State Security APT40 Tradecraft in Action | CISA
by nlqip
This advisory, authored by the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC), the United States Cybersecurity and Infrastructure Security Agency (CISA), the United States National Security Agency (NSA), the United States Federal Bureau of Investigation (FBI), the United Kingdom National Cyber Security Centre (NCSC-UK), the Canadian Centre for Cyber Security (CCCS), the New…
Read MoreCybersecurity Performance Management Awareness Month – How CPM helps you satisfy NIST CSF “Protect” controls – CnSight.io – Cybersecurity Performance Improvement
by nlqip
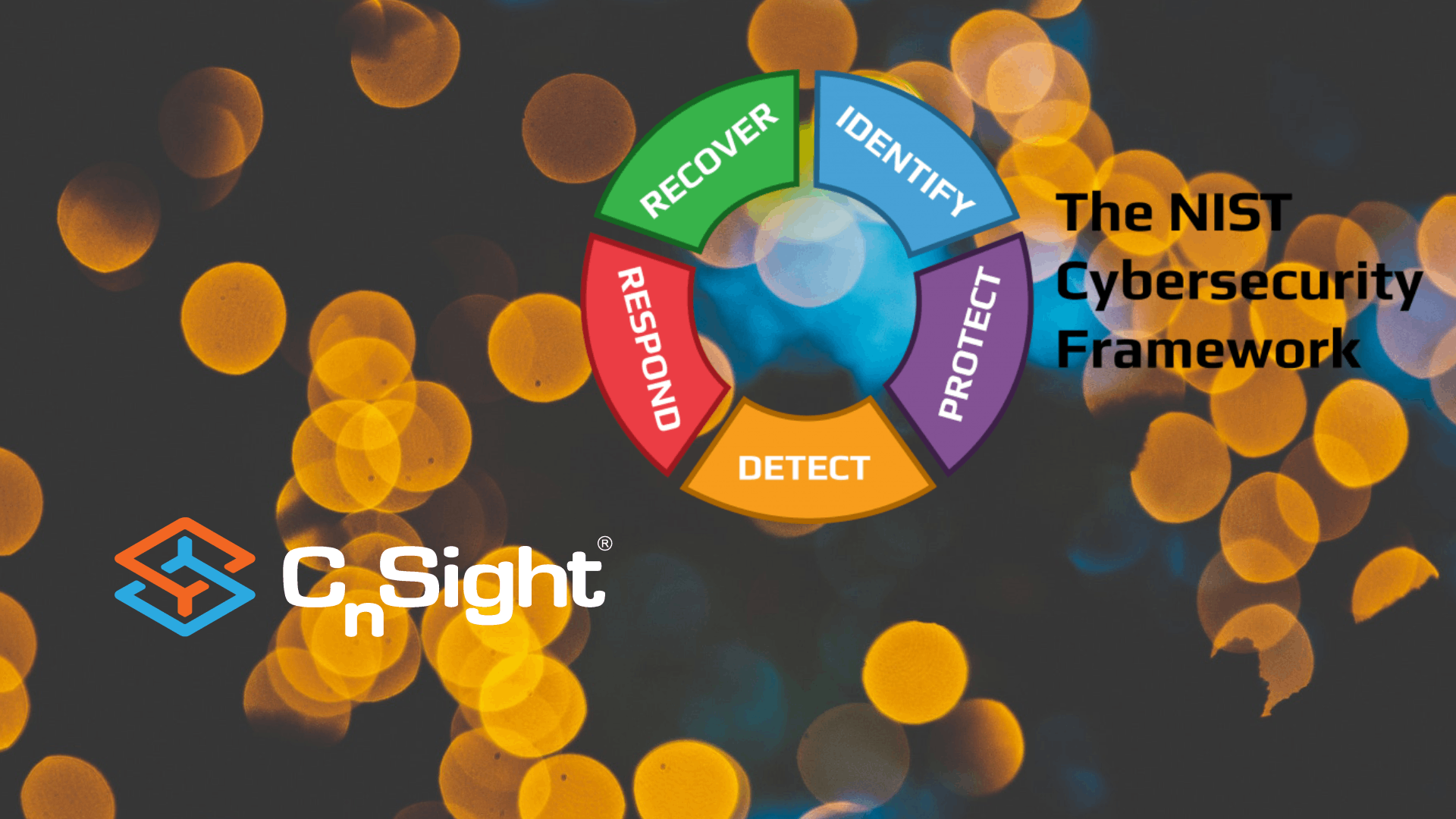
To celebrate Cyber Awareness Month, we’re releasing a series of posts outlining ways Cybersecurity Performance Management (CPM)TM can help you improve your cyber performance, reduce risk, and increase cyber ROI—all through the lens of the NIST Cybersecurity Framework (CSF). We’ll take you from the basics of CPM through to advanced practices with a weekly series…
Read MoreCybersecurity Performance Management Awareness Month – How CPM helps you satisfy NIST CSF “Identify” controls – CnSight.io – Cybersecurity Performance Improvement
by nlqip
To celebrate Cyber Awareness Month, we’re releasing a series of posts outlining ways Cybersecurity Performance Management (CPM)TM can help you improve your cyber performance, reduce risk, and increase cyber ROI—all through the lens of the NIST Cybersecurity Framework (CSF). Last week, we talked about the “Protect” Security Function, which you can find here. We’ll take…
Read MoreCybersecurity Performance Management Awareness Month – How CPM helps you satisfy NIST CSF “Detect” controls – CnSight.io – Cybersecurity Performance Improvement
by nlqip
To our regular readers, welcome back and thank you! To those new readers, in celebration of Cyber Awareness Month, we’re releasing a series of posts outlining ways Cybersecurity Performance Management (CPM)TM can help you improve your cyber performance, reduce risk, and increase cyber ROI—all through the lens of the NIST Cybersecurity Framework (CSF). Last week,…
Read MoreCybersecurity Performance Management Awareness Month – How CPM helps you satisfy NIST CSF “Respond” controls – CnSight.io – Cybersecurity Performance Improvement
by nlqip
To celebrate Cyber Awareness Month, we’re releasing a series of posts outlining ways Cybersecurity Performance Management (CPM)TM can help you improve your cyber performance, reduce risk, and increase cyber ROI—all through the lens of the NIST Cybersecurity Framework (CSF). Last week, we talked about the “Detect” Security Function, which you can find here. We’ll take you…
Read MoreCybersecurity Performance Management Awareness Month – How CPM helps you satisfy NIST CSF “Recover” controls – CnSight.io – Cybersecurity Performance Improvement
by nlqip
To celebrate Cyber Awareness Month, we’re releasing a series of posts outlining ways Cybersecurity Performance Management (CPM)TM can help you improve your cyber performance, reduce risk, and increase cyber ROI—all through the lens of the NIST Cybersecurity Framework (CSF). Last week, we talked about the “Recover” Security Function, which you can find here. We’ll take…
Read MoreCybersecurity Performance Management Awareness Month – How CPM aligns with the new “Govern” Security Function – CnSight.io – Cybersecurity Performance Improvement
by nlqip
To celebrate Cyber Awareness Month, we’ve been releasing a series of posts outlining ways Cybersecurity Performance Management (CPM)TM can help you improve your cyber performance, reduce risk, and increase cyber ROI—all through the lens of the NIST Cybersecurity Framework (CSF). Last week, we talked about the “Recover” Security Function, which you can find here. Today…
Read MoreSafeguarding Your Business: Strategies to Combat Rapid Vulnerability Exploitation – CnSight.io – Cybersecurity Performance Improvement
by nlqip
In recent years, businesses have struggle in the face of an ever-growing threat from cybercriminals. The increased sophistication and automation of malware distribution has resulted in an arms race between malware developers and system owners, who need to be on top of their game in remediating flaws as they become known. Rapid vulnerability exploitation has…
Read MoreComputer hardware maker Zotac has exposed return merchandise authorization (RMA) requests and related documents online for an unknown period, exposing sensitive customer information. Zotac, known for its range of compact and mini PCs, high-performance graphics cards, motherboards, and computer accessories, has misconfigured the web folders that hold RMA data, resulting in them being indexed by…
Read MoreEnhancing Cybersecurity with CISA’s Cross-Sector Cybersecurity Performance Goals – CnSight.io – Cybersecurity Performance Improvement
by nlqip
In today’s cybersecurity landscape, ensuring the implementation of best practices is essential for a resilient critical infrastructure where negative public impact is minimized when an event occurs. The Cybersecurity and Infrastructure Security Agency (CISA) has developed Cross-Sector Cybersecurity Performance Goals (CPGs) to help organizations prioritize their cybersecurity efforts. In this post we’ll take a closer…
Read MoreRecent Posts
- Interbank confirms data breach following failed extortion, data leak
- Canary Trap’s Bi-Weekly Cyber Roundup – Canary Trap
- [R1] Sensor Proxy Version 1.0.11 Fixes Multiple Vulnerabilities
- Microsoft Entra “security defaults” to make MFA setup mandatory
- Cisco Partner Summit 2024: 5 Top Execs On Partners, Company Transformation And Success