Author: nlqip
Apple has removed 25 virtual private network (VPN) apps from the Russian App Store at the request of Roskomnadzor, Russia’s telecommunications watchdog. Roskomnadzor confirmed to Interfax that the order targets multiple apps (including NordVPN, Proton VPN, Red Shield VPN, Planet VPN, Hidemy.Name VPN, Le VPN, and PIA VPN) used to gain access to content tagged…
Read MoreJul 08, 2024NewsroomCyber Espionage / Cloud Security A previously undocumented advanced persistent threat (APT) group dubbed CloudSorcerer has been observed targeting Russian government entities by leveraging cloud services for command-and-control (C2) and data exfiltration. Cybersecurity firm Kaspersky, which discovered the activity in May 2024, the tradecraft adopted by the threat actor bears similarities with that…
Read MoreA remote code execution vulnerability in the Ghostscript document conversion toolkit, widely used on Linux systems, is currently being exploited in attacks. Ghostscript comes pre-installed on many Linux distributions and is used by various document conversion software, including ImageMagick, LibreOffice, GIMP, Inkscape, Scribus, and the CUPS printing system. Tracked as CVE-2024-29510, this format string vulnerability…
Read MoreHPE has filed with the European regulatory commissions for approval to purchase Juniper Networks. Here’s the timeline for the blockbuster $14 billion merger. Hewlett Packard Enterprise has filed with the European Commission for regulatory approval of its blockbuster $14 billion acquisition of Juniper Networks. European regulators now have until August to either approve HPE’s deal…
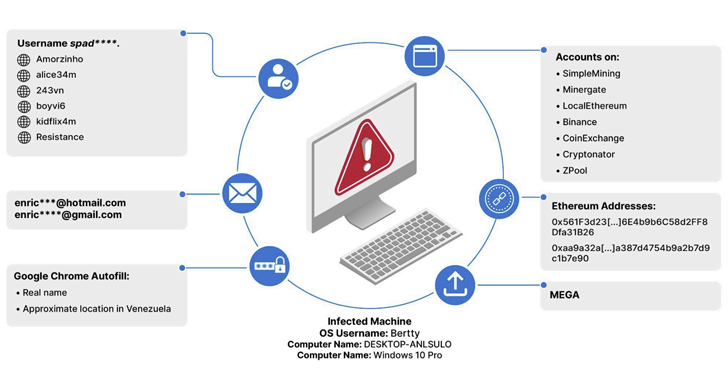
Read MoreJul 08, 2024NewsroomDark Web / Cyber Crime An analysis of information-stealing malware logs published on the dark web has led to the discovery of thousands of consumers of child sexual abuse material (CSAM), indicating how such information could be used to combat serious crimes. “Approximately 3,300 unique users were found with accounts on known CSAM…
Read MoreA new advanced persistent threat (APT) group named CloudSorcerer abuses public cloud services to steal data from Russian government organizations in cyberespionage attacks. Kaspersky security researchers discovered the cyberespionage group in May 2024. They report that CloudSorcerer uses custom malware that uses legitimate cloud services for command and control (C2) operations and data storage. Kaspersky…
Read More2code — himer The Himer WordPress theme before 2.1.1 does not sanitise and escape some of its Post settings, which could allow high privilege users such as Contributor to perform Stored Cross-Site Scripting attacks 2024-07-03 5.4 CVE-2024-2234contact@wpscan.com 2code — himer The Himer WordPress theme before 2.1.1 does not have CSRF checks in some places, which…
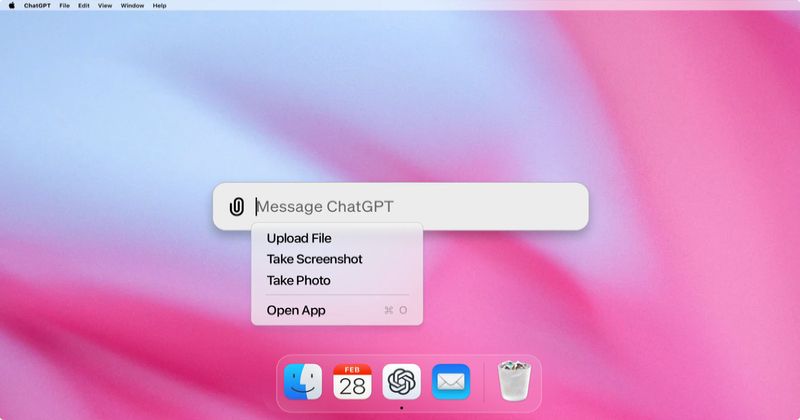
Read MoreIs it only a few weeks since OpenAI announced its new app for macOS computers? To much fanfare, the makers of ChatGPT revealed a desktop version that allowed Mac users to ask questions directly rather than via the web. “ChatGPT seamlessly integrates with how you work, write, and create,” bragged OpenAI. What could possibly go…
Read MoreJul 08, 2024NewsroomRansomware / Encryption An emerging ransomware-as-a-service (RaaS) operation called Eldorado comes with locker variants to encrypt files on Windows and Linux systems. Eldorado first appeared on March 16, 2024, when an advertisement for the affiliate program was posted on the ransomware forum RAMP, Singapore-headquartered Group-IB said. The cybersecurity firm, which infiltrated the ransomware…
Read MoreCRN recognizes over 100 individuals across the channel who are dedicated to building an inclusive culture where everyone can thrive and reach their full potential. In its second annual Inclusive Channel Leaders list, CRN shines a spotlight on those executives who lead by example and are driving diversity, equity and inclusion across their organization. These…
Read MoreRecent Posts
- Don’t become a statistic: Defending your personal data from dark web criminals
- Interbank confirms data breach following failed extortion, data leak
- Canary Trap’s Bi-Weekly Cyber Roundup – Canary Trap
- [R1] Sensor Proxy Version 1.0.11 Fixes Multiple Vulnerabilities
- Microsoft Entra “security defaults” to make MFA setup mandatory