Author: nlqip
New Open SSH Vulnerability It’s a serious one: The vulnerability, which is a signal handler race condition in OpenSSH’s server (sshd), allows unauthenticated remote code execution (RCE) as root on glibc-based Linux systems; that presents a significant security risk. This race condition affects sshd in its default configuration. […] This vulnerability, if exploited, could lead…
Read MoreFrom the editors of our sister publication Computerworld, this vendor comparison chart helps IT and security staff understand what the major unified endpoint management (UEM) platforms can do for their organizations to help choose the right solution. Source link lol
Read MoreEuropol coordinated a joint law enforcement action known as Operation Morpheus, which led to the takedown of almost 600 Cobalt Strike servers used by cybercriminals to infiltrate victims’ networks. During a single week in late June, law enforcement identified known IP addresses associated with criminal activity and domain names that were part of attack infrastructure…
Read MoreJul 03, 2024The Hacker NewsOSINT / Artificial Intelligence Recently the Office of the Director of National Intelligence (ODNI) unveiled a new strategy for open-source intelligence (OSINT) and referred to OSINT as the “INT of first resort”. Public and private sector organizations are realizing the value that the discipline can provide but are also finding that…
Read More“We used the standard GitHub phishlet that can be found in various user repositories on GitHub itself,” Stewart said. “When the targeted user visits the lure URL, other than the hostname in the URL bar, what they will see looks just like the normal GitHub login page, because it is the actual GitHub login page,…
Read MoreProton has launched ‘Docs in Proton Drive,’ a free and open-source end-to-end encrypted web-based document editing and collaboration tool. Proton is a Swiss company renowned for its privacy-focused services, including Proton VPN, Proton Mail, Proton Pass, Proton Drive, and now also Proton Docs. Recently, the company announced its transition to becoming a non-profit organization to…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/deep-dive-into-blockchain-security-vulnerabilities-and-protective-measures” on this server. Reference #18.c5d7ce17.1720001197.5047ce9 https://errors.edgesuite.net/18.c5d7ce17.1720001197.5047ce9 Source link lol
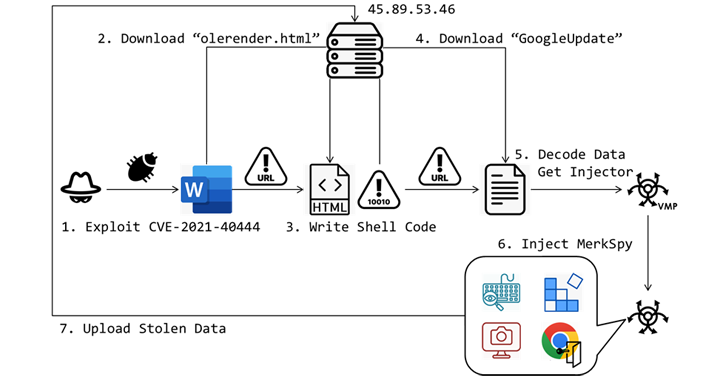
Read MoreJul 03, 2024NewsroomSpyware / Vulnerability Unknown threat actors have been observed exploiting a now-patched security flaw in Microsoft MSHTML to deliver a surveillance tool called MerkSpy as part of a campaign primarily targeting users in Canada, India, Poland, and the U.S. “MerkSpy is designed to clandestinely monitor user activities, capture sensitive information, and establish persistence…
Read MoreJul 03, 2024NewsroomMalware / SEO Poisoning The loader-as-a-service (LaaS) known as FakeBat has become one of the most widespread loader malware families distributed using the drive-by download technique this year, findings from Sekoia reveal. “FakeBat primarily aims to download and execute the next-stage payload, such as IcedID, Lumma, RedLine, SmokeLoader, SectopRAT, and Ursnif,” the company…
Read MoreArtificial Intelligence (AI) is a hot topic at the moment. It’s everywhere. You probably already use it every day. That chatbot you’re talking to about your lost parcel? Powered by conversational AI. The ‘recommended’ items lined up under your most frequently brought Amazon purchases? Driven by AI/ML (machine learning) algorithms. You might even use generative…
Read MoreRecent Posts
- Don’t become a statistic: Defending your personal data from dark web criminals
- Interbank confirms data breach following failed extortion, data leak
- Canary Trap’s Bi-Weekly Cyber Roundup – Canary Trap
- [R1] Sensor Proxy Version 1.0.11 Fixes Multiple Vulnerabilities
- Microsoft Entra “security defaults” to make MFA setup mandatory