Author: nlqip
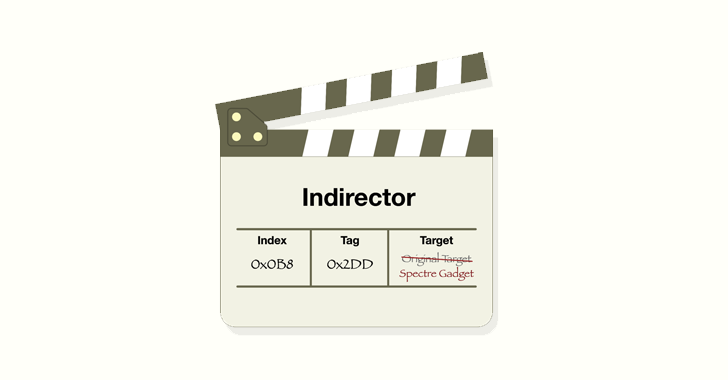
Jul 02, 2024NewsroomHardware Security / Vulnerability Modern CPUs from Intel, including Raptor Lake and Alder Lake, have been found vulnerable to a new side-channel attack that could be exploited to leak sensitive information from the processors. The attack, codenamed Indirector by security researchers Luyi Li, Hosein Yavarzadeh, and Dean Tullsen, leverages shortcomings identified in Indirect…
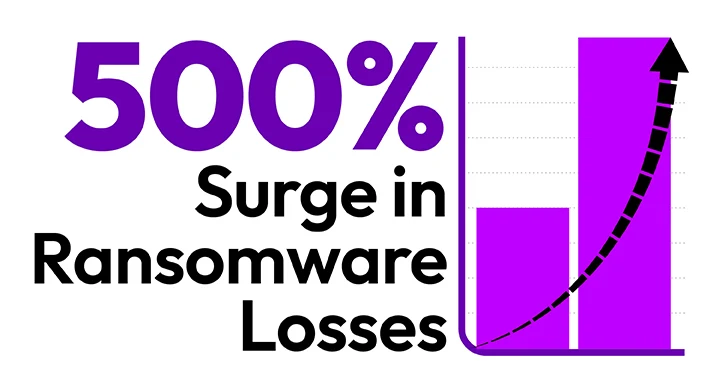
Read MoreThe cybersecurity threat landscape has witnessed a dramatic and alarming rise in the average ransomware payment, an increase exceeding 500%. Sophos, a global leader in cybersecurity, revealed in its annual “State of Ransomware 2024” report that the average ransom payment has increased 500% in the last year with organizations that paid a ransom reporting an…
Read MoreCISOs and other security execs often find themselves in a difficult position. Attackers are always getting better, and now they can use genAI to help craft ransomware emails or create deepfakes. At the same time, security practitioners are bombarded by vendors with an alphabet soup of solutions: SSE, SASE, ZTNA, DLP, CASB, SWG, SOAR, DEM,…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/navigating-the-cybersecurity-landscape-a-deep-dive-into-effective-siem-strategies-1” on this server. Reference #18.efd7ce17.1719914431.6ab2d19d https://errors.edgesuite.net/18.efd7ce17.1719914431.6ab2d19d Source link lol
Read MoreScams, Social Media Here’s how cybercriminals go after YouTube channels and use them as conduits for fraud – and what you should watch out for when watching videos on the platform 01 Jul 2024 • , 4 min. read As one of today’s most popular social media platforms, YouTube is often in the crosshairs of…
Read MoreJul 02, 2024NewsroomCyber Espionage / Vulnerability A China-nexus cyber espionage group named Velvet Ant has been observed exploiting a zero-day flaw in Cisco NX-OS Software used in its switches to deliver malware. The vulnerability, tracked as CVE-2024-20399 (CVSS score: 6.0), concerns a case of command injection that allows an authenticated, local attacker to execute arbitrary…
Read MoreJul 02, 2024NewsroomDigital Regulation / Tech News Meta’s decision to offer an ad-free subscription in the European Union (E.U.) has faced a new setback after regulators accused the social media behemoth of breaching the bloc’s competition rules by forcing users to choose between seeing ads or paying to avoid them. The European Commission said the…
Read MoreJul 02, 2024NewsroomData Theft / Wi-Fi Security An Australian man has been charged with running a fake Wi-Fi access point during a domestic flight with an aim to steal user credentials and data. The unnamed 42-year-old “allegedly established fake free Wi-Fi access points, which mimicked legitimate networks, to capture personal data from unsuspecting victims who…
Read MoreThe cybersecurity vendor says the planned acquisition will assist with improving visibility across multiple types of assets and environments. Rapid7 announced Monday it has reached a deal to acquire Noetic Cyber, a startup whose technology is aimed at bolstering the vendor’s capabilities in cyber asset attack surface management (CAASM). The Boston-based cybersecurity vendor didn’t disclose…
Read More‘You’re getting improved data privacy and security through localized computing, as well as reduced cloud dependency because now you’re processing a lot of the data locally,’ says Vibha Rustagi, Cognizant’s global head of IoT and engineering. Global IT services provider Cognizant Monday unveiled Cognizant Neuro Edge, a new addition to its Neuro suite of technologies…
Read MoreRecent Posts
- Enterprise Identity Threat Report 2024: Unveiling Hidden Threats to Corporate Identities
- LiteSpeed Cache Plugin Vulnerability Poses Significant Risk to WordPress Websites
- LottieFiles hit in npm supply chain attack targeting users’ crypto
- Don’t become a statistic: Defending your personal data from dark web criminals
- Interbank confirms data breach following failed extortion, data leak