Author: nlqip
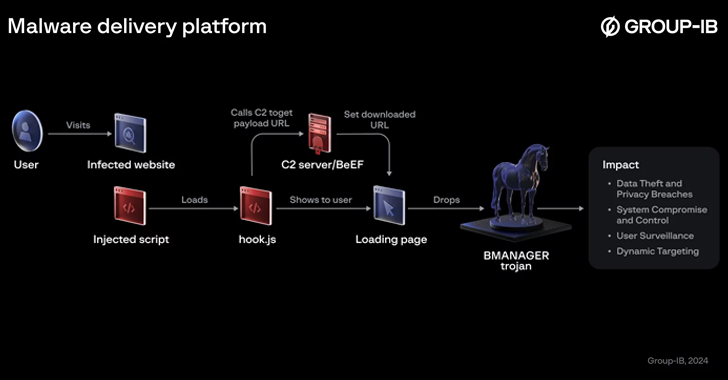
Jun 25, 2024NewsroomData Theft / Web Security A previously undocumented threat actor dubbed Boolka has been observed compromising websites with malicious scripts to deliver a modular trojan codenamed BMANAGER. “The threat actor behind this campaign has been carrying out opportunistic SQL injection attacks against websites in various countries since at least 2022,” Group-IB researchers Rustam…
Read MoreBiggest hack, if confirmed If confirmed, the Federal Reserve breach would turn into one of the biggest banking hacks in US history. Being the central banking system of the country, the Federal Reserve operates twelve banking districts, home to major cities like Boston, New York, Dallas, Chicago, and San Francisco. Although the Federal Reserve is…
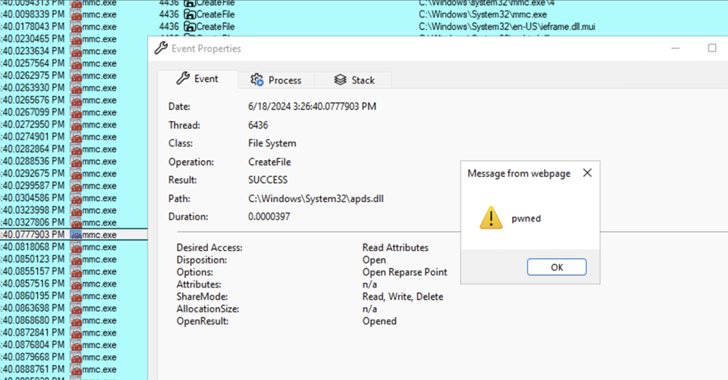
Read MoreJun 25, 2024NewsroomVulnerability / Threat Detection Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management Console (MMC) and evade security defenses. Elastic Security Labs has codenamed the approach GrimResource after identifying an artifact (“sccm-updater.msc“) that was…
Read MoreBreaking the M-209 Interesting paper about a German cryptanalysis machine that helped break the US M-209 mechanical ciphering machine. The paper contains a good description of how the M-209 works. Tags: academic papers, cryptanalysis, cryptography, history of cryptography Posted on June 25, 2024 at 7:02 AM • 0 Comments Sidebar photo of Bruce Schneier by…
Read MoreJun 25, 2024The Hacker NewsBrowser Security / Endpoint Security Browser security is becoming increasingly popular, as organizations understand the need to protect at the point of risk – the browser. Network and endpoint solutions are limited in their ability to protect from web-borne threats like phishing websites or malicious browser extensions. They also do not…
Read MoreP2PInfect, originally a dormant peer-to-peer malware botnet with unclear motives, has finally come alive to deploy a ransomware module and a cryptominer in attacks on Redis servers. According to Cado Security, which has been tracking P2PInfect for some time now, there is evidence the malware operates as a “botnet for hire,” although conflicting information prevents…
Read MoreTo maintain their growing stature and evolving role, CSOs/CISOs “must scale their mandate in the face of increasingly accelerated disruptive technological changes” from AI and cloud transformations, greater customer trust expectations, and a threat landscape that continues to intensify, SAP’s Lange says. Adapting to the velocity of change and providing a consistent defensible risk posture…
Read MoreAnalysts point out that further efforts to block them could disrupt critical services for US enterprises. “The crackdown on Chinese telecom firms may impact the efficiency of US enterprises’ data management and global connectivity by limiting competitive options and increasing transition costs,” said Prabhu Ram, head of the Industry Intelligence Group at CyberMedia Research. “Enterprises…
Read MoreA CISO presented with a key analytic shortcoming during an intrusion event may be more likely to overlook data quality or ethical issues in a new machine learning product they think would prevent similar incidents going forward. Or a positive support experience with an insurer during a crisis might perversely incentivize a too-comfortable relationship with…
Read MoreJun 25, 2024NewsroomNational Security / Wikileak WikiLeaks founder Julian Assange has been freed in the U.K. and has departed the country after serving more than five years in a maximum security prison at Belmarsh for what was described by the U.S. government as the “largest compromises of classified information in the history” of the country.…
Read MoreRecent Posts
- Cybersecurity Snapshot: Apply Zero Trust to Critical Infrastructure’s OT/ICS, CSA Advises, as Five Eyes Spotlight Tech Startups’ Security
- 5 SaaS Misconfigurations Leading to Major Fu*%@ Ups
- Massive Git Config Breach Exposes 15,000 Credentials; 10,000 Private Repos Cloned
- Microsoft Warns of Chinese Botnet Exploiting Router Flaws for Credential Theft
- Microsoft Delays Windows Copilot+ Recall Release Over Privacy Concerns