Author: nlqip
The Hacking of Culture and the Creation of Socio-Technical Debt Culture is increasingly mediated through algorithms. These algorithms have splintered the organization of culture, a result of states and tech companies vying for influence over mass audiences. One byproduct of this splintering is a shift from imperfect but broad cultural narratives to a proliferation of…
Read MoreJun 19, 2024NewsroomCybercrime / Cryptocurrency A threat actor who goes by alias markopolo has been identified as behind a large-scale cross-platform scam that targets digital currency users on social media with information stealer malware and carries out cryptocurrency theft. The attack chains involve the use of a purported virtual meeting software named Vortax (and 23…
Read MoreJun 19, 2024NewsroomMalware / Cyber Attack Chinese-speaking users are the target of a never-before-seen threat activity cluster codenamed Void Arachne that employs malicious Windows Installer (MSI) files for virtual private networks (VPNs) to deliver a command-and-control (C&C) framework called Winos 4.0. “The campaign also promotes compromised MSI files embedded with nudifiers and deepfake pornography-generating software,…
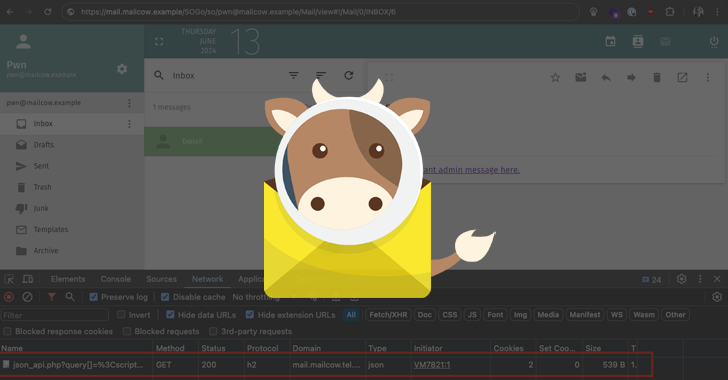
Read MoreJun 19, 2024NewsroomEmail Security / Vulnerability Two security vulnerabilities have been disclosed in the Mailcow open-source mail server suite that could be exploited by malicious actors to achieve arbitrary code execution on susceptible instances. Both shortcomings impact all versions of the software prior to version 2024-04, which was released on April 4, 2024. The issues…
Read MoreCould separation of certain functions improve risk management? In other circumstances, it makes sense to have a head of cybersecurity to lead the technical, operations and architecture teams, and a CISO to lead governance, risk, and compliance functions, according to Chirag Joshi, CISO and founder of 7 Rules Cyber consultancy. “The governance and risk role…
Read MoreMicrosoft has confirmed that Windows 10 apps will mistakenly display an “How do you want to open this file?” dialog box when attempting to right-click on the program’s icon and perform a registered task. Windows apps can be registered to offer different tasks to run when you right click on the program’s icon in the…
Read MoreMicrosoft has confirmed that Windows 10 apps will mistakenly display an “How do you want to open this file?” dialog box when attempting to right-click on the program’s icon and perform a registered task. Windows apps can be registered to offer different tasks to run when you right click on the program’s icon in the…
Read MoreApply appropriate updates provided by Broadcom to vulnerable systems immediately after appropriate testing. (M1051: Update Software) Safeguard 7.1: Establish and Maintain a Vulnerability Management Process: Establish and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this Safeguard. Safeguard 7.4: Perform…
Read MoreAMD is investigating whether it suffered a cyberattack after a threat actor put allegedly stolen data up for sale on a hacking forum, claiming it contains AMD employee information, financial documents, and confidential information. “We are aware of a cybercriminal organization claiming to be in possession of stolen AMD data,” AMD told BleepingComputer in a…
Read MoreNvidia CEO Jensen Huang: HPE-Nvidia Is A ‘Massive Partnership,’ Exits Sphere Stage With A ‘Go HPE!’
by nlqip
Nvidia and HPE introduced new co-developed, co-branded AI offerings that, ‘with a giant go to market’ can ‘bring AI to the world’s enterprises for the very first time,’ said Nvidia CEO Jensen Huang onstage at HPE Discover. Nvidia CEO Jensen Huang Tuesday told 15,000 Hewlett Packard Enterprise customers and partners packed into the Sphere arena…
Read More