Author: nlqip
Welcome to this week’s edition of the “Bi-Weekly Cyber Roundup” by Canary Trap. At Canary Trap, it is our mission to keep you up-to-date with the most crucial news in the world of cybersecurity and this bi-weekly publication is your gateway to the latest news. This week’s cybersecurity round-up covers critical developments across the industry.…
Read MoreNov 04, 2024The Hacker NewsWeekly Recap / Cybersecurity This week was a total digital dumpster fire! Hackers were like, “Let’s cause some chaos!” and went after everything from our browsers to those fancy cameras that zoom and spin. (You know, the ones they use in spy movies? 🕵️♀️) We’re talking password-stealing bots, sneaky extensions that…
Read MoreNov 04, 2024Mohit KumarDDoS Attack / Cybercrime German law enforcement authorities have announced the disruption of a criminal service called dstat[.]cc that made it possible for other threat actors to easily mount distributed denial-of-service (DDoS) attacks. “The platform made such DDoS attacks accessible to a wide range of users, even those without any in-depth technical…
Read MoreMicrosoft has confirmed several bugs causing install and Blue Screen of Death (BSOD) issues impacting Windows Server 2025 systems with more than 256 logical processors. Users may experience symptoms such as Windows Server 2025 installation or upgrading processes failing or hanging and server starting and restarting taking as much as three hours or more in…
Read MoreNov 04, 2024Ravie LakshmananArtificial Intelligence / Vulnerability Google said it discovered a zero-day vulnerability in the SQLite open-source database engine using its large language model (LLM) assisted framework called Big Sleep (formerly Project Naptime). The tech giant described the development as the “first real-world vulnerability” uncovered using the artificial intelligence (AI) agent. “We believe this…
Read MoreCyber Threats That Could Impact the Retail Industry This Holiday Season (and What to Do About It)
by nlqip
As the holiday season approaches, retail businesses are gearing up for their annual surge in online (and in-store) traffic. Unfortunately, this increase in activity also attracts cybercriminals looking to exploit vulnerabilities for their gain. Imperva, a Thales company, recently published its annual holiday shopping cybersecurity guide. Data from the Imperva Threat Research team’s six-month analysis…
Read MoreCisco says that non-public files recently downloaded by a threat actor from a misconfigured public-facing DevHub portal don’t contain information that could be exploited in future breaches of the company’s systems. While analyzing the exposed documents, the company found that their contents include data that Cisco publishes for customers and other DevHub users. However, files…
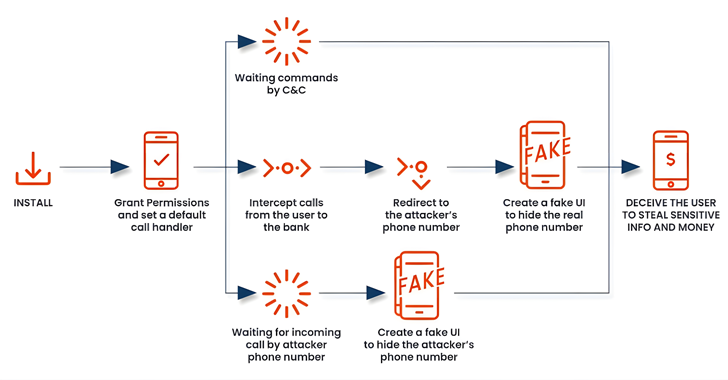
Read MoreNov 04, 2024Ravie LakshmananMobile Security / Financial Fraud Cybersecurity researchers have discovered a new version of a well-known Android malware family dubbed FakeCall that employs voice phishing (aka vishing) techniques to trick users into parting with their personal information. “FakeCall is an extremely sophisticated Vishing attack that leverages malware to take almost complete control of…
Read MoreImage: Midjourney A relatively new ransomware operation named Interlock attacks organizations worldwide, taking the unusual approach of creating an encryptor to target FreeBSD servers. Launched at the end of September 2024, Interlock has since claimed attacks on six organizations, publishing stolen data on their data leak site after a ransom was not paid. One of…
Read MoreResearchers have shown that it’s possible to abuse OpenAI’s real-time voice API for ChatGPT-4o, an advanced LLM chatbot, to conduct financial scams with low to moderate success rates. ChatGPT-4o is OpenAI’s latest AI model that brings new enhancements, such as integrating text, voice, and vision inputs and outputs. Due to these new features, OpenAI integrated…
Read MoreRecent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day


![German Police Disrupt DDoS-for-Hire Platform dstat[.]cc; Suspects Arrested](https://kartwheelnewz.info/wp-content/uploads/2024/11/German-Police-Disrupt-DDoS-for-Hire-Platform-dstatcc-Suspects-Arrested.png)