Author: nlqip
Using AI for Political Polling Public polling is a critical function of modern political campaigns and movements, but it isn’t what it once was. Recent US election cycles have produced copious postmortems explaining both the successes and the flaws of public polling. There are two main reasons polling fails. First, nonresponse has skyrocketed. It’s radically…
Read MoreJun 12, 2024Newsroom State-sponsored threat actors backed by China gained access to 20,000 Fortinet FortiGate systems worldwide by exploiting a known critical security flaw between 2022 and 2023, indicating that the operation had a broader impact than previously known. “The state actor behind this campaign was already aware of this vulnerability in FortiGate systems at…
Read MoreJun 12, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have disclosed details of an ongoing phishing campaign that leverages recruiting- and job-themed lures to deliver a Windows-based backdoor named WARMCOOKIE. “WARMCOOKIE appears to be an initial backdoor tool used to scout out victim networks and deploy additional payloads,” Elastic Security Labs researcher Daniel Stepanic said in…
Read MoreLet’s talk about pedigree. With more and more applications going through automated screening, the lack of one or another facet, such as a college education, continues to reject well-qualified candidates and sends their applications to the trash. I recall my own experience from some years ago when I was engaged in the final series of…
Read MoreHealthcare increasingly under attack Such secondary scams are becoming increasingly commonplace and healthcare providers are particularly at risk, according to compliance experts. Victoria Hordern, a partner at international law firm Taylor Wessing’s technology, IP, and information team, told CSOonline: “A health data leak is a tantalizing prospect for a cybercriminal intending to carry out a…
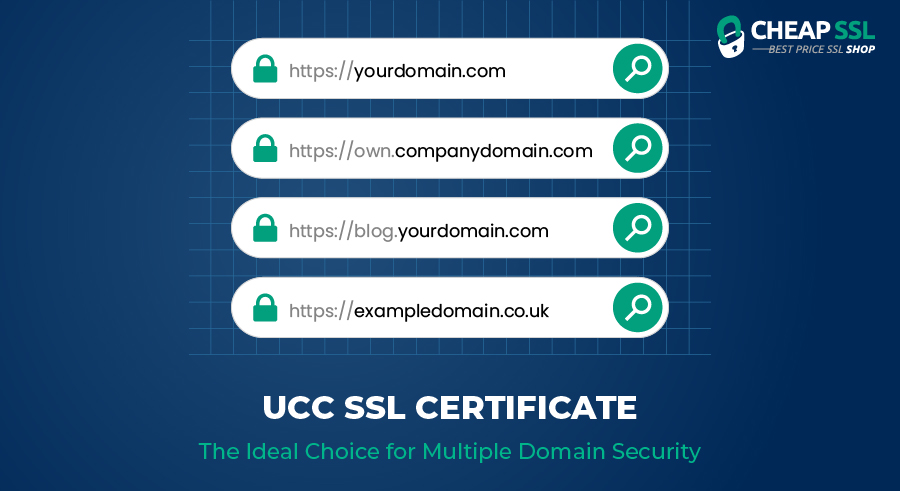
Read MoreA Unified Communication Certificate (UCC), also known as a Multi-Domain SSL or SAN certificate, offers a streamlined and cost-effective solution. Originally designed for Microsoft Exchange and Office Communication servers, UCC SSL certificates allow you to secure up to 250 domains with a single certificate. This article explores the benefits and workings of UCC SSL certificates.…
Read MoreJun 12, 2024NewsroomPatch Tuesday / Vulnerability Microsoft has released security updates to address 51 flaws as part of its Patch Tuesday updates for June 2024. Of the 51 vulnerabilities, one is rated Critical and 50 are rated Important. This is in addition to 17 vulnerabilities resolved in the Chromium-based Edge browser over the past month.…
Read MorePure Storage, a leading provider of cloud storage systems and services, confirmed on Monday that attackers breached its Snowflake workspace and gained access to what the company describes as telemetry information. While the exposed information also included customer names, usernames, and email addresses, it did not contain credentials for array access or any other data…
Read MoreThe TellYouThePass ransomware gang has been exploiting the recently patched CVE-2024-4577 remote code execution vulnerability in PHP to deliver webshells and execute the encryptor payload on target systems. Attacks started on June 8, less than 48 hours after the release of security updates by PHP’s maintainers, and relied on publicly available exploit code. TellYouThePass ransomware is…
Read MoreApply the stable channel update provided by Adobe to vulnerable systems immediately after appropriate testing. (M1051: Update Software)o Safeguard 7.1 : Establish and Maintain a Vulnerability Management Process: Establish and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this Safeguard.o…
Read More