Author: nlqip
CISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog…
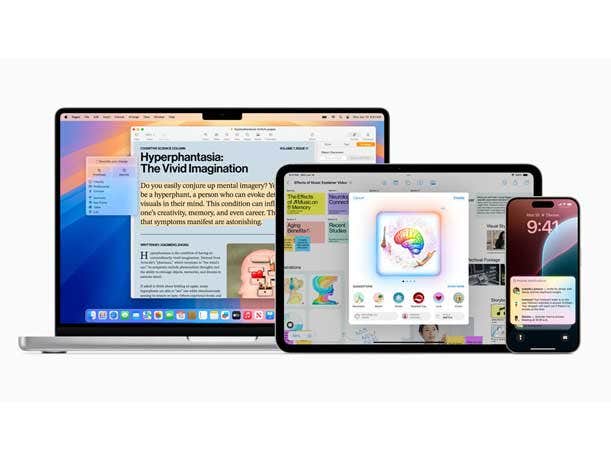
Read MoreApple’s much-anticipated upcoming suite of AI features for select iPhones, Macs and iPads is called Apple Intelligence, and it will include an enhanced Siri experience, systemwide Writing Tools, message and notification prioritization, call transcription and summarization, and ChatGPT integration. Apple Monday revealed Apple Intelligence, its much-anticipated suite of AI features that will enhance Siri’s natural…
Read MoreImpersonation scams are on the rise and often use the names and titles of government employees. The Cybersecurity and Infrastructure Security Agency (CISA) is aware of recent impersonation scammers claiming to represent the agency. As a reminder, CISA staff will never contact you with a request to wire money, cash, cryptocurrency, or use gift cards…
Read MoreThe multi-cloud networking upstart is partnering with the “de facto” security leader Palo Alto Networks. The new relationship will give enterprises new approach to securing applications and workloads across multi-cloud environments, Prosimo execs told CRN. Multi-cloud networking upstart Prosimo is joining forces with security specialist Palo Alto Networks to further secure application access at a…
Read MoreAs Oracle Inks Partnerships With OpenAI, Google Cloud, CTO Ellison Says ‘We Should Be Interconnected To Everybody’
by nlqip
‘That’s what we’re attempting to do within our multi-cloud strategy. I think that’s what customers want. So I’m optimistic that’s the way the world will settle out. We’ll get rid of these fees for moving data from cloud to cloud,’ says Oracle Chairman and CTO Larry Ellison on the company’s earnings call. Just prior to…
Read MoreMicrosoft has announced that the DirectAccess remote access solution is now deprecated and will be removed in a future release of Windows, recommending companies migrate to the ‘Always On VPN’ for enhanced security and continued support. DirectAccess is a bidirectional remote access technology introduced by Microsoft in Windows 7 and Windows Server 2008 R2, providing domain-joined…
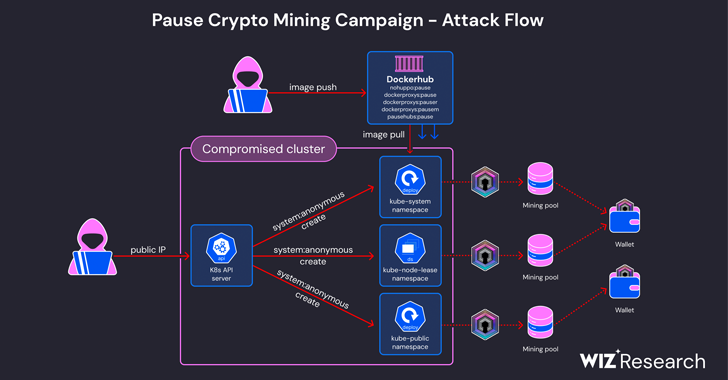
Read MoreJun 12, 2024NewsroomKubernetes / Endpoint Security Cybersecurity researchers have warned of an ongoing cryptojacking campaign targeting misconfigured Kubernetes clusters to mine Dero cryptocurrency. Cloud security firm Wiz, which shed light on the activity, said it’s an updated variant of a financially motivated operation that was first documented by CrowdStrike in March 2023. “In this incident,…
Read MoreAt Splunk .conf24, Cisco CEO Chuck Robbins and Go-to-Market President Gary Steele spoke to Splunk customers about the benefits of integrating the companies’ security and observability products and highlighted the opportunities those combinations will create for partners. Cisco Systems and Splunk executives are putting on a full-court press at Splunk .conf24 this week to tout…
Read MoreUpgrades to Databricks’ Mosaic AI, a deeper collaboration with Nvidia and the open-sourcing of Unity Catalog are among the biggest updates from Summit 2024. Upgrades to Databricks’ Mosaic AI unified tooling product for artificial intelligence and machine learning. A deeper collaboration with Nvidia. And the open-sourcing of Unity Catalog. These are some of the biggest…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-072 DATE(S) ISSUED: 06/12/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated…
Read MoreRecent Posts
- Channel Women In Security: Ethically Hacking To Build Tomorrow’s Leaders
- Tonaquint Names Involta, Flexential Vet As New CEO
- Custom “Pygmy Goat” malware used in Sophos Firewall hack on govt network
- Vulnerability Summary for the Week of October 28, 2024 | CISA
- Foreign Threat Actor Conducting Large-Scale Spear-Phishing Campaign with RDP Attachments | CISA