Author: nlqip
The U.S. Justice Department and international partners dismantled the 911 S5 proxy botnet and arrested 35-year-old Chinese national YunHe Wang, its administrator. As early as 2011, Wang and his conspirators pushed malware onto victims’ devices using multiple malicious VPN applications bundling proxy backdoors. The VPN apps that added compromised devices to the 911 S5 residential…
Read MoreThe cybersecurity vendor says that a now-fixed VPN vulnerability has been exploited in attacks. Check Point has released emergency patches for a VPN vulnerability that the cybersecurity vendor said has been exploited in a small number of attacks. Initially disclosed by Check Point on Monday, the company released more details Tuesday as well as fixes…
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog…
Read MoreCVE-2024-24919: Check Point Security Gateway Information Disclosure Zero-Day Exploited in the Wild
by nlqip
Amid warnings of threat actors targeting VPN devices, Check Point has identified a zero-day information disclosure vulnerability impacting Check Point Network Security gateways which has been exploited by malicious actors. Background On May 27, Check Point released a blog post with recommendations on security best practices. According to the original post, Check Point has been…
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-4978 Justice AV Solutions (JAVS) Viewer Installer Embedded Malicious Code Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the…
Read MoreAmong the companies named to this year’s Solution Provider 500, 41 are joining the list for the first time. Here’s a look at who’s new. Joining The Club As the IT industry grows and evolves so does the channel, the VARs, solution providers and strategic service providers who strive to meet the ever-changing IT needs…
Read MoreOkta warns that a Customer Identity Cloud (CIC) feature is being targeted in credential stuffing attacks, stating that numerous customers have been targeted since April. Okta is a leading identity and access management company providing cloud-based solutions for secure access to apps, websites, and devices. It offers single sign-on (SSO), multi-factor authentication (MFA), universal directory, API…
Read MoreMay 29, 2024NewsroomEnterprise Security / Vulnerability Check Point is warning of a zero-day vulnerability in its Network Security gateway products that threat actors have exploited in the wild. Tracked as CVE-2024-24919, the issue impacts CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways, and Quantum Spark appliances. “The vulnerability potentially allows an attacker to…
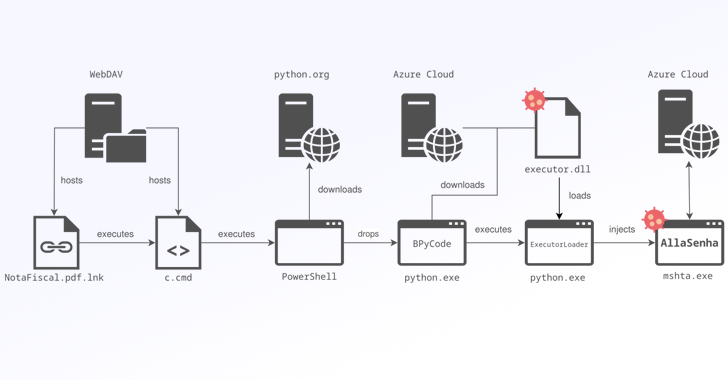
Read MoreBrazilian banking institutions are the target of a new campaign that distributes a custom variant of the Windows-based AllaKore remote access trojan (RAT) called AllaSenha. The malware is “specifically aimed at stealing credentials that are required to access Brazilian bank accounts, [and] leverages Azure cloud as command-and-control (C2) infrastructure,” French cybersecurity company HarfangLab said in…
Read More‘When we look at what’s in our pipeline, it is increasingly filled with newer technologies. That tells us that those newer offerings, whether they’re around cloud, around AI, around quantum, around digital workplace, are really getting the buyers’ attention,’ says Unisys’ Chairman and CEO Peter Altabef. While global IT solution provider Unisys can trace its…
Read MoreRecent Posts
- Canada Orders TikTok to Shut Down Canadian Operations Over Security Concerns
- Jane Goodall: Reasons for hope | Starmus highlights
- A Vulnerability in Cisco Unified Industrial Wireless Software for Ultra-Reliable Wireless Backhaul Access Point Could Allow for Remote Code Execution
- GenAI Risks To Software Security On The Rise: Experts
- CEO Gerry Smith: ODP Strengthens B2B Focus, Investments, But Faces Challenges