Author: nlqip
Cybersecurity researchers are alerting of phishing campaigns that abuse Cloudflare Workers to serve phishing sites that are used to harvest users’ credentials associated with Microsoft, Gmail, Yahoo!, and cPanel Webmail. The attack method, called transparent phishing or adversary-in-the-middle (AitM) phishing, “uses Cloudflare Workers to act as a reverse proxy server for a legitimate login page,…
Read MoreThe Pakistan-nexus Transparent Tribe actor has been linked to a new set of attacks targeting Indian government, defense, and aerospace sectors using cross-platform malware written in Python, Golang, and Rust. “This cluster of activity spanned from late 2023 to April 2024 and is anticipated to persist,” the BlackBerry Research and Intelligence Team said in a…
Read MoreImproved incident response: This refers to the capability of network security monitoring to more quickly and effectively react to security incidents by providing real-time alerts, detailed reports, and automated responses. This allows security teams to quickly mitigate threats, minimize damage, and analyze incidents to prevent future incidents. Identification of attack surfaces: “These tools give companies…
Read MoreInstead, they should strive to be viewed as the Department of Yes and, where they are fully leaning in to support business objectives, along with the responsibility of explaining and mitigating risks. Saying no and being the Department of No are two very different things and shifting this perception through conversation enables CISOs to educate…
Read MoreHackers are utilizing code from a Python clone of Microsoft’s venerable Minesweeper game to hide malicious scripts in attacks on European and US financial organizations. Ukraine’s CSIRT-NBU and CERT-UA attribute the attacks to a threat actor tracked as ‘UAC-0188,’ who is using the legitimate code to hide Python scripts that download and install the SuperOps RMM. Superops RMM is a legitimate remote…
Read MoreWhat is known about the vulnerability The newly patched vulnerability is tracked as CVE-2024-5274 and is described as a type confusion issue in the Chrome V8 JavaScript engine. Type confusion is a type of error that can occur in programming languages that use dynamic typing such as JavaScript and can be exploited by modifying the…
Read MorePost updated on 5/25 to add three more pharmaceutical firms also impacted by the Cencora security breach. Some of the largest drug companies in the world have disclosed data breaches due to a February 2024 cyberattack at Cencora, whom they partner with for pharmaceutical and business services. Cencora, formerly AmerisourceBergen, is a pharmaceutical services provider…
Read MoreAn Indian national pleaded guilty to wire fraud conspiracy for stealing over $37 million through a fake Coinbase website used to steal credentials. Chirag Tomar, 30, was arrested at the Atlanta airport on December 20, 2023, following investigations by the U.S. Secret Service with assistance from the FBI in Nashville. Stealing Coinbase credentials Tomar and…
Read MoreA new Google Ads malvertising campaign, coinciding with the launch of the Arc web browser for Windows, was tricking people into downloading trojanized installers that infect them with malware payloads. The Arc browser is a new web browser featuring an innovative user interface design that sets it apart from traditional browsers. Launched in July 2023 for…
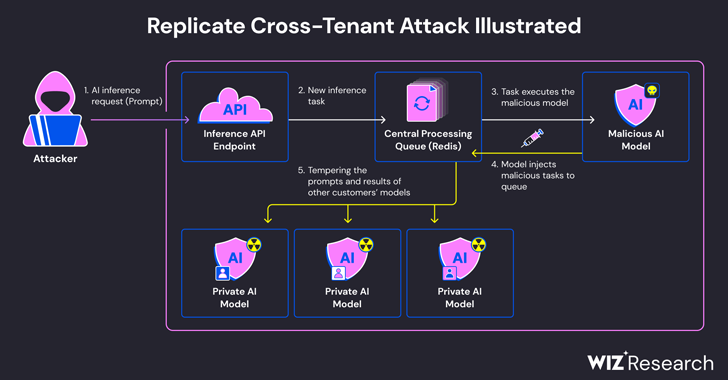
Read MoreMay 25, 2024NewsroomMachine Learning / Data Breach Cybersecurity researchers have discovered a critical security flaw in an artificial intelligence (AI)-as-a-service provider Replicate that could have allowed threat actors to gain access to proprietary AI models and sensitive information. “Exploitation of this vulnerability would have allowed unauthorized access to the AI prompts and results of all…
Read MoreRecent Posts
- Canada orders TikTok to shut down over national risk concerns
- CISA Adds Four Known Exploited Vulnerabilities to Catalog | CISA
- Ingram Micro CEO: ‘The Future Of Business Is About Transforming Relationships, Not Just Transactions’
- HPE warns of critical RCE flaws in Aruba Networking access points
- Ingram Micro Helps Partners Up Their Cybersecurity Game With Slew Of Tools, Expert Guidance