Author: nlqip
[*] 10Web Form Builder Team–Form Maker by 10Web Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) vulnerability in 10Web Form Builder Team Form Maker by 10Web allows Stored XSS.This issue affects Form Maker by 10Web: from n/a through 1.15.24. 2024-05-14 5.9 CVE-2024-34437audit@patchstack.com 1Panel-dev–1Panel 1Panel is an open source Linux server operation and maintenance…
Read MoreZoom has announced the global availability of post-quantum end-to-end encryption (E2EE) for Zoom Meetings, with Zoom Phone and Zoom Rooms to follow soon. Meetings is a popular video conferencing service that allows users to host and join virtual meetings with high-definition video and audio, featuring screen sharing, chat, and participant management, making it a popular choice…
Read MoreBy ARC Labs contributors, John Dwyer and Harold Tabellion In April 2024, security researcher Meowmycks released a LetMeowIn which was designed to harvest credentials from the LSASS process on Microsoft Windows systems. In this blog, ARC Labs will provide an overview of how LetMeowIn works and provide some detection guidance for defenders. Dumping credentials from…
Read MoreNews around Microsoft Copilot in Azure, Team Copilot and Defender for Cloud are some of the most exciting updates to come out of Build 2024. An upcoming preview for Microsoft Copilot in Azure. Team Copilot’s ability to bring generative artificial intelligence to entire organizations and departments. And upgrades to Defender for Cloud to better protect…
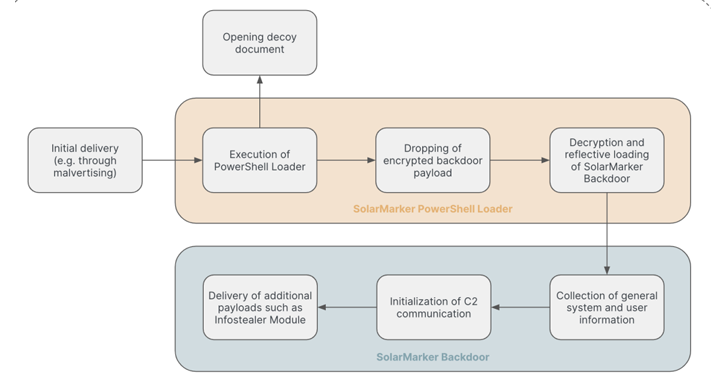
Read MoreMay 21, 2024NewsroomData Breach / Malware The persistent threat actors behind the SolarMarker information-stealing malware have established a multi-tiered infrastructure to complicate law enforcement takedown efforts, new findings from Recorded Future show. “The core of SolarMarker’s operations is its layered infrastructure, which consists of at least two clusters: a primary one for active operations and…
Read MoreTo many, Kubernetes is a black box that’s difficult to understand, manage and secure. If you’re using stateful persistent volumes – cloud resources that live and manage data outside the scope of your pods – it can be even darker. Many organizations use stateful persistent volumes to provide stable storage for certain applications, such as…
Read MoreTenable®, the Exposure Management company, today announced Noam Dahan, a cloud security research manager for Tenable, will present at Identiverse 2024, taking place on May 28-31, 2024 in Las Vegas. Dahan will give an in-depth presentation on cloud identity and access management policies and guardrails that protect organizations from unknown threats and reduce risks…
Read MoreThe agreement to acquire IBM’s QRadar SaaS assets also opens the door for Palo Alto Networks to pursue the ‘much larger prize’ of migrating on-premises QRadar customers to XSIAM, CEO Nikesh Arora said Monday. Palo Alto Networks’ agreement to acquire IBM’s QRadar SaaS assets is poised to rapidly elevate the cybersecurity vendor’s position in the…
Read More‘Over the last 25 years, how many times have the analysts come and said print is dead. Print is declining. It’s shifting. It’s not going away. I don’t believe in our lifetime we’re going to see it disappear completely. And as a dealer, you just have to be ready to adapt to whatever changes. And…
Read MoreFile Integrity Monitoring (FIM) is an IT security control that monitors and detects file changes in computer systems. It helps organizations audit important files and system configurations by routinely scanning and verifying their integrity. Most information security standards mandate the use of FIM for businesses to ensure the integrity of their data. IT security compliance…
Read MoreRecent Posts
- Fortinet Execs: Firewall Growth Is On The Rebound
- Analysis: HP Reorganization Elevates Ex-Poly CEO’s Role In Growth Strategy
- A Vulnerability in Android OS Could Allow for Remote Code Execution
- North Korean hackers use new macOS malware against crypto firms
- CISA: ‘Critical’ Palo Alto Networks Flaw Has Seen Exploitation