Author: nlqip
The U.S. Department of Justice charged two suspects for allegedly leading a crime ring that laundered at least $73 million from cryptocurrency investment scams, also known as “pig butchering.” In pig butchering scams, criminals approach targets using various messaging apps, dating platforms, or social media platforms to build trust and introduce them to investment schemes…
Read MoreLong View Systems, T-Rex Solutions, NexusTek, Secureworks, Deepwatch and Five9 are among the companies to list open positions for channel-related roles. This month, Long View Systems, T-Rex Solutions and NexusTek are among the solution providers to list open positions while Secureworks, Deepwatch and Five9 are among the vendors to list open positions for channel-related roles.…
Read MoreFor the week ending May 17, CRN takes a look at the companies that brought their ‘A’ game to the channel including Palo Alto Networks, WekaIO, Alkira, Hewlett Packard Enterprise, Kyndryl and Ampere. The Week Ending May 17 Topping this week’s Came to Win is cybersecurity giant Palo Alto Networks, which is making a key…
Read MoreSnowflake is seeking to acquire AI startup company Reka AI for over $1 billion as the cloud data superstar strives to build the world’s No. 1 AI ecosystem. The $2.67 billion company is reportedly in talks to acquire Reka AI in a move to boost its generative AI innovation and capabilities. “We have this strategy…
Read MoreThe WebTPA Employer Services (WebTPA) data breach disclosed earlier this month is impacting close to 2.5 million individuals, the U.S. Department of Health and Human Services notes. Some of the impacted people are customers at large insurance companies such as The Hartford, Transamerica, and Gerber Life Insurance. WebTPA is a GuideWell Mutual Holding Corporation subsidiary and a…
Read MoreOne SEC Commissioner, Hester Peirce, voted for the new rule, but expressed concerns it might generate notification fatigue, which could lead to people eventually ignoring all security notifications. “My greatest concern about the rule is that its breadth could undermine the value of the customer notifications by making them so commonplace that people ignore them.…
Read MoreCybersecurity Snapshot: CISA Warns Hospitals about Black Basta, as Tenable Study Finds Cloud-Related Breaches Pervasive
by nlqip
Find out why healthcare organizations must beware of the Black Basta ransomware group. Meanwhile, a Tenable study found that 95% of surveyed organizations suffered a cloud-related breach, and offers insights for boosting cloud security. Plus, a Cloud Security Alliance report delves into how AI systems can create risky gaps in your cloud environment. And much…
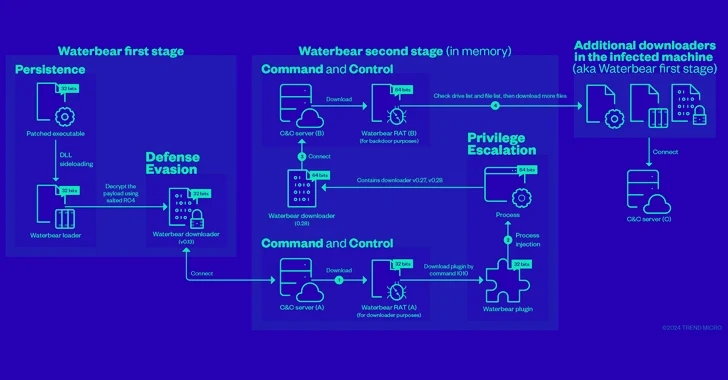
Read MoreCybersecurity researchers have shed more light on a remote access trojan (RAT) known as Deuterbear used by the China-linked BlackTech hacking group as part of a cyber espionage campaign targeting the Asia-Pacific region this year. “Deuterbear, while similar to Waterbear in many ways, shows advancements in capabilities such as including support for shellcode plugins, avoiding…
Read MoreA new report from XM Cyber has found – among other insights – a dramatic gap between where most organizations focus their security efforts, and where the most serious threats actually reside. The new report, Navigating the Paths of Risk: The State of Exposure Management in 2024, is based on hundreds of thousands of attack…
Read MoreFBI Seizes BreachForums Website The FBI has seized the BreachForums website, used by ransomware criminals to leak stolen corporate data. If law enforcement has gained access to the hacking forum’s backend data, as they claim, they would have email addresses, IP addresses, and private messages that could expose members and be used in law enforcement…
Read MoreRecent Posts
- ScanSource CEO Mike Baur Talks Reorganization, Acquisitions And Why He’s Bullish About Growth
- D-Link won’t fix critical flaw affecting 60,000 older NAS devices
- Five Companies That Came To Win This Week
- Palo Alto Networks warns of potential PAN-OS RCE vulnerability
- Unpatched Mazda Connect bugs let hackers install persistent malware