Author: nlqip
FBI Seizes BreachForums Website The FBI has seized the BreachForums website, used by ransomware criminals to leak stolen corporate data. If law enforcement has gained access to the hacking forum’s backend data, as they claim, they would have email addresses, IP addresses, and private messages that could expose members and be used in law enforcement…
Read MoreThe U.S. Justice Department charged five individuals today, a U.S. Citizen woman, a Ukrainian man, and three foreign nationals, for their involvement in cyber schemes that generated revenue for North Korea’s nuclear weapons program. They were allegedly involved between October 2020 and October 2023 in a campaign coordinated by the North Korean government “to infiltrate…
Read MoreIn general, though, the best way to mitigate against DDoS attacks is to simply have the capacity to withstand large amounts of inbound traffic. Depending on your situation, that might mean beefing up your own network, or making use of a content delivery network (CDN), a service designed to accommodate huge amounts of traffic. Your…
Read MoreMay 17, 2024NewsroomLinux / Malware The Kimsuky (aka Springtail) advanced persistent threat (APT) group, which is linked to North Korea’s Reconnaissance General Bureau (RGB), has been observed deploying a Linux version of its GoBear backdoor as part of a campaign targeting South Korean organizations. The backdoor, codenamed Gomir, is “structurally almost identical to GoBear, with…
Read More“It is vital that communication over the internet remains secure,” Rosenworcel said in the statement. “Although there have been efforts to help mitigate BGP’s security risks since its original design, more work needs to be done. With this proposal, we would require broadband providers to report to the FCC on their efforts to implement industry…
Read MoreMay 17, 2024NewsroomVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added two security flaws impacting D-Link routers to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The list of vulnerabilities is as follows – CVE-2014-100005 – A cross-site request forgery (CSRF) vulnerability impacting D-Link DIR-600…
Read MoreTo meet the requirements, most public companies take proactive measures to ensure they have systems in place to assess, evaluate, and respond to incidents. “Unfortunately, in many cases, these processes are established outside of the operational resilience framework, and as a result, they are not integrated with the company’s crisis management program,” says Nolan, who…
Read MoreSecurity researchers have warned about a new cyberespionage campaign that targets artificial intelligence experts working in private industry, government and academia. The attackers, likely of Chinese origin, are using a remote access trojan (RAT) called SugarGh0st. “The timing of the recent campaign coincides with an 8 May 2024 report from Reuters, revealing that the US…
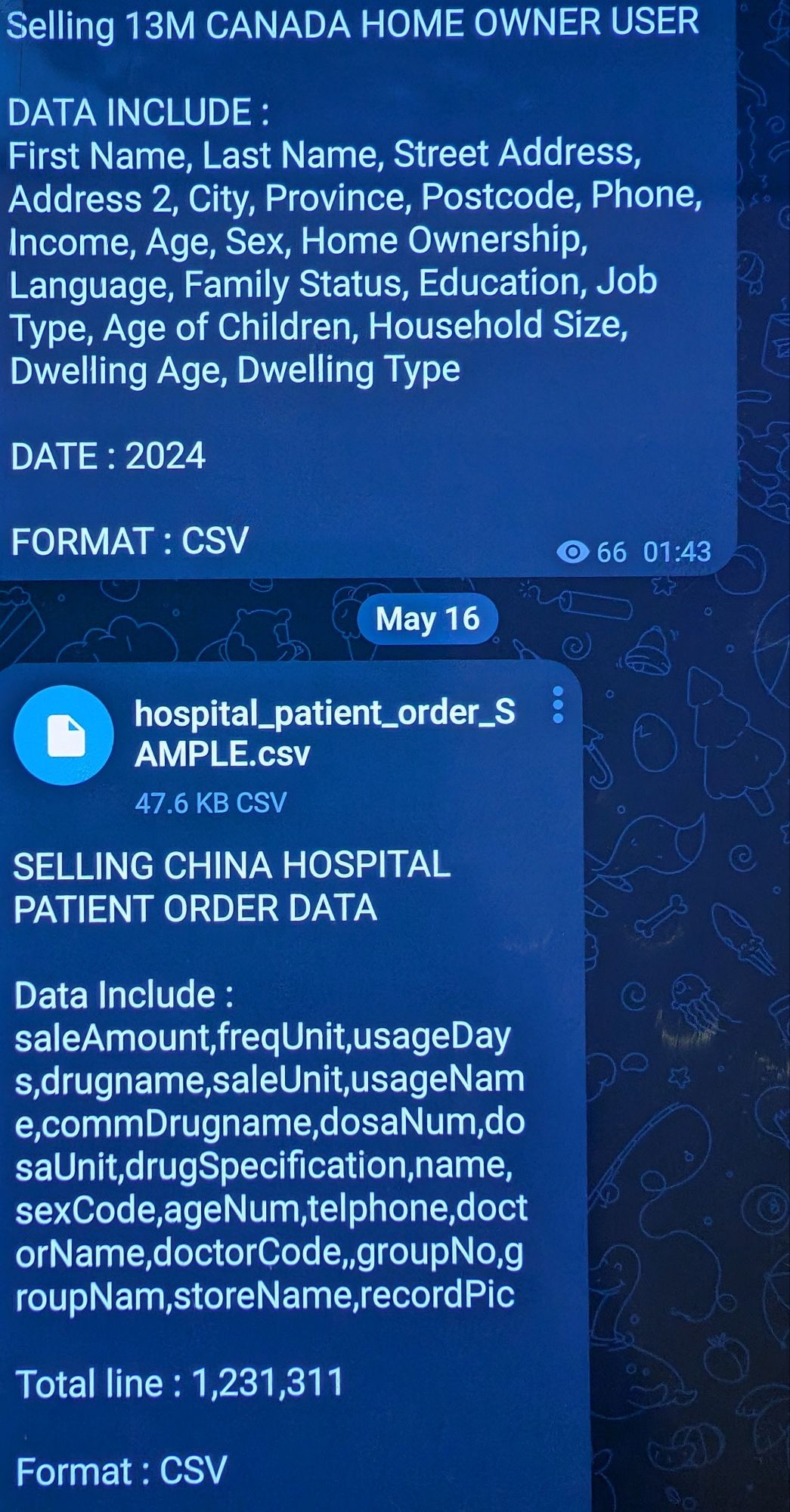
Read MoreIn a Telegram group, two important data advertised by threat actors. The first one is 13 million pieces of Canadian homeowners’ PII. It is claimed that the data includes first name, last name, street Address, address 2, city, province, postal code, phone, income, age, sex, home ownership, language, family status, education, job type, age of…
Read MoreWelcome to this week’s edition of the “Bi-Weekly Cyber Roundup” by Canary Trap. At Canary Trap, it is our mission to keep you up-to-date with the most crucial news in the world of cybersecurity and this bi-weekly publication is your gateway to the latest news. In this week’s roundup, we’ll start by recapping the activities…
Read MoreRecent Posts
- Critical Veeam RCE bug now used in Frag ransomware attacks
- ScanSource CEO Mike Baur Talks Reorganization, Acquisitions And Why He’s Bullish About Growth
- D-Link won’t fix critical flaw affecting 60,000 older NAS devices
- Five Companies That Came To Win This Week
- Palo Alto Networks warns of potential PAN-OS RCE vulnerability