Author: nlqip
To meet the requirements, most public companies take proactive measures to ensure they have systems in place to assess, evaluate, and respond to incidents. “Unfortunately, in many cases, these processes are established outside of the operational resilience framework, and as a result, they are not integrated with the company’s crisis management program,” says Nolan, who…
Read MoreSecurity researchers have warned about a new cyberespionage campaign that targets artificial intelligence experts working in private industry, government and academia. The attackers, likely of Chinese origin, are using a remote access trojan (RAT) called SugarGh0st. “The timing of the recent campaign coincides with an 8 May 2024 report from Reuters, revealing that the US…
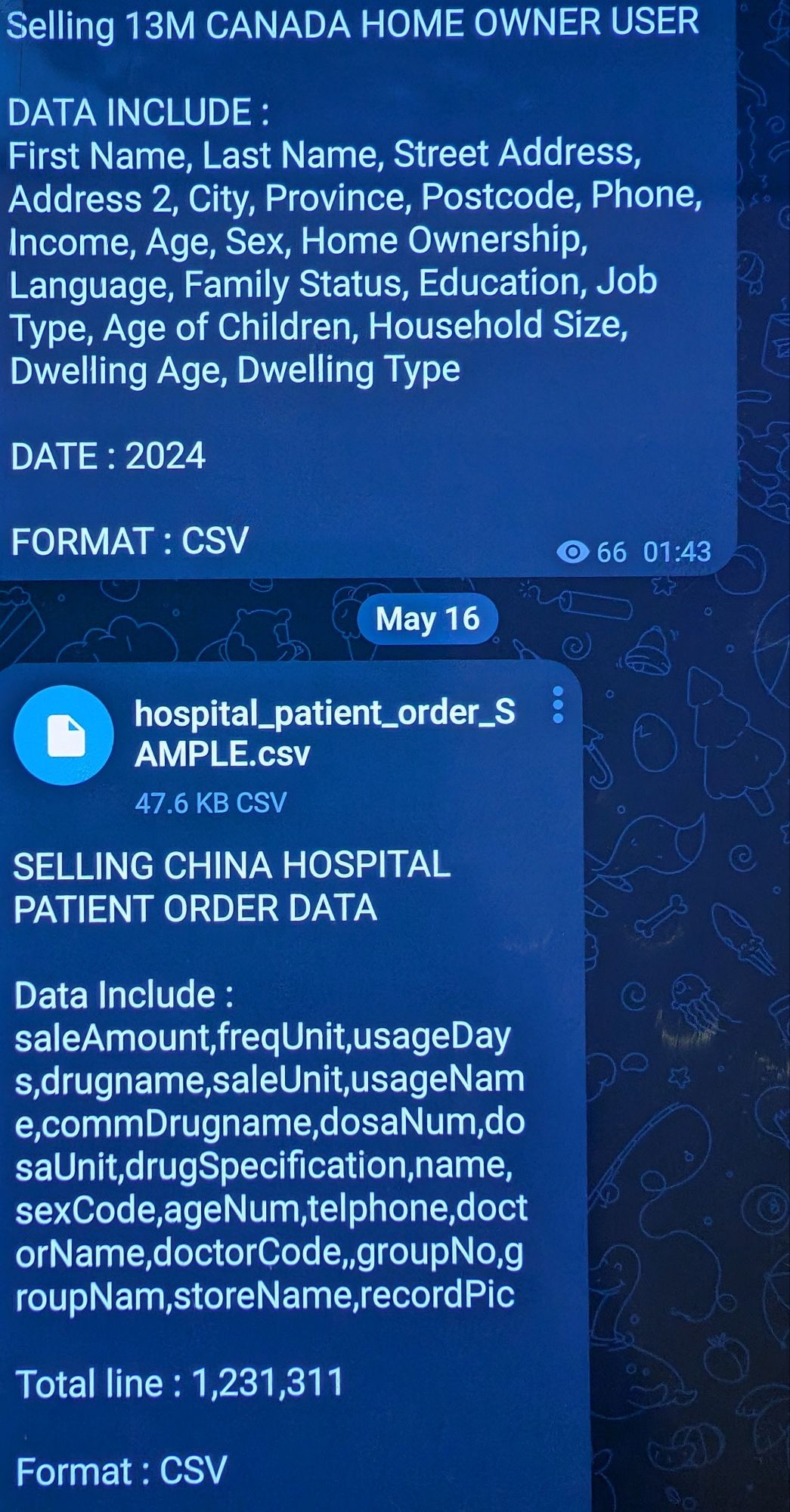
Read MoreIn a Telegram group, two important data advertised by threat actors. The first one is 13 million pieces of Canadian homeowners’ PII. It is claimed that the data includes first name, last name, street Address, address 2, city, province, postal code, phone, income, age, sex, home ownership, language, family status, education, job type, age of…
Read MoreWelcome to this week’s edition of the “Bi-Weekly Cyber Roundup” by Canary Trap. At Canary Trap, it is our mission to keep you up-to-date with the most crucial news in the world of cybersecurity and this bi-weekly publication is your gateway to the latest news. In this week’s roundup, we’ll start by recapping the activities…
Read MoreScreenshots for PuTTY BleepingComputer Review: PuTTY is a Windows client for several remote shell protocols such as SSH and Telnet. Included in the installer are auxilliary utilities to generate PuTTY-compatible keyfiles for password-less login. PuTTY is the premier Windows utility for administering remote computers via simple command line. Visitors Also Liked: Source link lol
Read MoreThe Norwegian National Cyber Security Centre (NCSC) recommends replacing SSLVPN/WebVPN solutions with alternatives due to the repeated exploitation of related vulnerabilities in edge network devices to breach corporate networks. The organization recommends that the transition be completed by 2025, while organizations subject to the ‘Safety Act’ or those in critical infrastructure should adopt safer alternatives by…
Read MoreThe U.S. Justice Department charged five individuals today, a U.S. Citizen woman, a Ukrainian man, and three foreign nationals, for their involvement in cyber schemes that generated revenue for North Korea’s nuclear weapons program. They were allegedly involved between October 2020 and October 2023 in a campaign coordinated by the North Korean government “to infiltrate…
Read MoreMicrosoft has shared a temporary fix for a known issue preventing Microsoft 365 customers from replying to encrypted emails using the Outlook Desktop client. This confirms customer reports regarding these issues when using the classic Outlook clients shared on Microsoft’s community website in recent months. According to online reports, reinstalling Outlook or creating a new…
Read More‘This is the biggest concession of a SIEM vendor to an XDR vendor so far,’ writes Forrester’s Allie Mellen. With Palo Alto Networks slated to acquire IBM’s QRadar assets, the deal is a sign of where things are headed in the rapidly consolidating market for security operations platforms as traditional SIEM loses favor, according to…
Read MoreElectronic prescription provider MediSecure in Australia has shut down its website and phone lines following a ransomware attack believed to originate from a third-party vendor. The incident has impacted personal and health information of individuals but the extent remains unclear at this time. Operating since 2009, MediSecure provides digital tools to healthcare professionals to manage…
Read MoreRecent Posts
- Red Hat Updates Present ‘Huge’ Partner Opportunities in OpenShift, Edge
- US govt officials’ communications compromised in recent telecom hack
- Microsoft patches Windows zero-day exploited in attacks on Ukraine
- Leaked info of 122 million linked to B2B data aggregator breach
- Dell NativeEdge Platform Brings AI To Edge Operations