Author: nlqip
Even if you’ve got all the bells and whistles when it comes to securing your data center, your cloud deployments, your building’s physical security, and you’ve invested in defensive technologies, have the right security policies and processes in place and measure their effectiveness and continuously improve, still a crafty social engineer can weasel his way…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. As a high school student interested in exploring the connection between technology and nature, I was curious to find out how the natural…
Read MoreSecurity flaws in Telit Cinterion cellular modems, widely used in sectors including industrial, healthcare, and telecommunications, could allow remote attackers to execute arbitrary code via SMS. A set of eight separate issues, seven of them with identifiers CVE-2023-47610 through CVE-2023-47616 and another that has yet to be registered, were disclosed last November by security researchers…
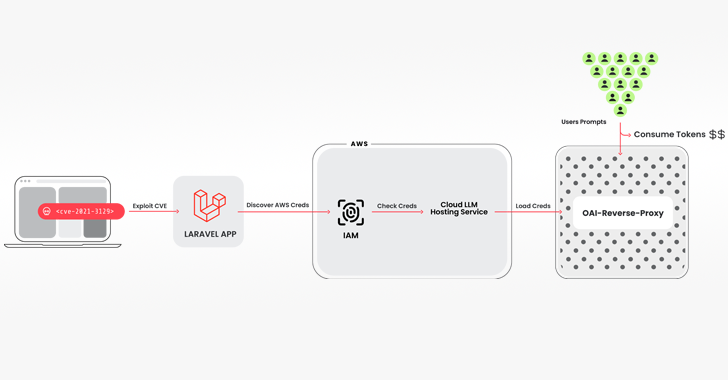
Read MoreMay 10, 2024NewsroomVulnerability / Cloud Security Cybersecurity researchers have discovered a novel attack that employs stolen cloud credentials to target cloud-hosted large language model (LLM) services with the goal of selling access to other threat actors. The attack technique has been codenamed LLMjacking by the Sysdig Threat Research Team. “Once initial access was obtained, they…
Read MoreGoogle has released a security update for the Chrome browser to fix the fifth zero-day vulnerability exploited in the wild since the start of the year. The high-severity issue tracked as CVE-2024-4671 is a “user after free” vulnerability in the Visuals component that handles the rendering and display of content on the browser. CVE-2024-4671 was…
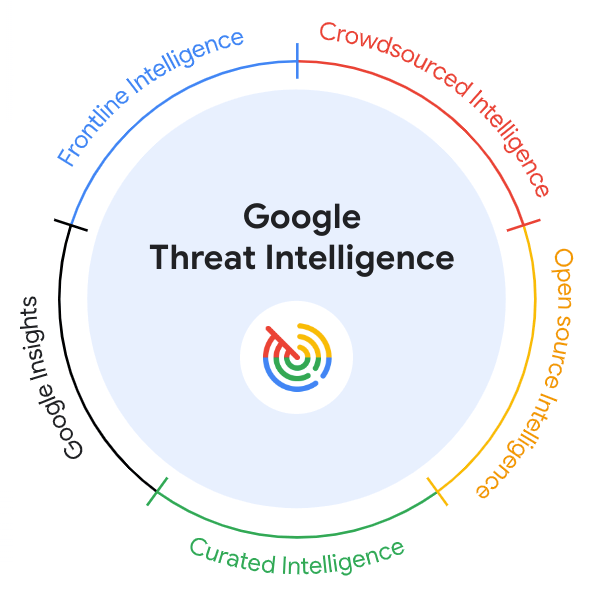
Read MoreAt the RSA Conference in San Francisco, Google announced the launch of Google Threat Intelligence, a groundbreaking new offering that leverages the company’s vast resources and expertise in cybersecurity to provide actionable threat intelligence at an unprecedented scale. Unparalleled Depth and Breadth of Intelligence This new platform combines the front-line expertise of Mandiant, the global…
Read MoreCISOs can protect themselves by making responsibilities clear With cyber incidents becoming more frequent and prominent, the role of CISOs has become a lightning rod. “Historically, the risk calculus was bad stuff happens, I’m going to get fired, I’ll go on to my next job,” said Charles Blauner, partner and CISO in residence at Team8…
Read MoreApply appropriate updates provided by Google to vulnerable systems immediately after appropriate testing. (M1051: Update Software) Safeguard 7.1: Establish and Maintain a Vulnerability Management Process: Establish and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this Safeguard. Safeguard 7.4: Perform…
Read More‘It’s probably one of the biggest announcements that we’ve ever made, or ever will make, because for the first time, Dell now has a cloud storage product to sell. This is hugely important to them because their customers sometimes say, ‘Hey, Dell guys, I don’t really want to buy any more on-prem storage from you…
Read MoreAscension Cyberattack: Electronic Health Records System Not Working, Some Elective Procedures ‘Temporarily Paused’
by nlqip
St. Louis-based Ascension, which operates 140 hospitals in the U.S., said in its latest update that it did not have a timeline for restoring its system. Ascension, a health system with 140 hospitals and operations in 19 states and Washington, D.C. that said it suffered a data breach this week, said Thursday that its electronic…
Read MoreRecent Posts
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption