Author: nlqip
Virtual private networking (VPN) companies market their services as a way to prevent anyone from snooping on your Internet usage. But new research suggests this is a dangerous assumption when connecting to a VPN via an untrusted network, because attackers on the same network could force a target’s traffic off of the protection provided by…
Read MoreThe UK’s National Cyber Security Centre (NCSC) has called for a ban on commonly used and easily guessable passwords, citing the alarming rise in cybercrime. The agency highlights the vulnerability of users who rely on weak passwords, making them prime targets for cybercriminals. The NCSC emphasizes that passwords like “123456,” “password,” and “qwerty” are frequently…
Read MoreToday is a monumental day for the cybersecurity industry. Live from RSA Conference 2024, I’m excited to introduce LevelBlue – a joint venture with AT&T and WillJam Ventures, to form a new, standalone managed security services business. You can read more about the news here. In 2022, I founded my private equity firm, WillJam Ventures,…
Read MoreMay 06, 2024NewsroomNetwork Security / Malware The recently uncovered cyber espionage campaign targeting perimeter network devices from several vendors, including Cisco, may have been the work of China-linked actors, according to new findings from attack surface management firm Censys. Dubbed ArcaneDoor, the activity is said to have commenced around July 2023, with the first confirmed…
Read MoreCisco Systems is announcing a number of security product updates, including a major advancement related to its acquisition of Splunk. Cisco Systems on Monday announced a number of major security product updates at the RSA Conference 2024, including an XDR advancement stemming from its acquisition of Splunk and an expansion of capabilities for its recently…
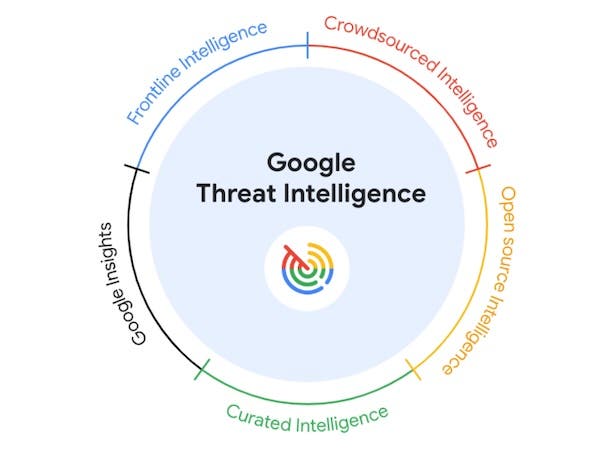
Read MoreLaunched at RSAC 2024, the new Google Threat Intelligence offering provides faster protection against threats by combining insights from Mandiant, VirusTotal and Google with GenAI-powered capabilities, the company says. Google Cloud announced a new cybersecurity offering Monday that represents a major advancement by making threat intelligence more automated and “more actionable,” an executive told CRN.…
Read More‘EQT shares our vision for the future as we transform how the world’s biggest brands connect with customers,’ says Perficient CEO Tom Hogan. Global channel consultant Perficient is being acquired by private equity firm EQT AB for approximately $3 billion in a move its CEO says is a win for shareholders as Perficient’s stock jumped…
Read More‘We were a little weak, if I may, on the Azure side. CCT has a lot of customers and a lot of know-how on Azure implementation and expansion of services around IaaS. That’s something we are looking into expanding with CCT,’ says ISSQUARED CEO and Founder Bala Ramaiah. IT and cybersecurity MSP ISSQUARED Monday said…
Read MoreHere’s the exact global cloud market share figures for AWS, Alibaba, Google Cloud, Microsoft and Salesforce for first quarter 2024 as the market increased to $76 billion. The three largest cloud companies on the planet—Amazon Web Services, Microsoft and Google Cloud—continued to battle for global cloud market share leadership during the first quarter of 2024,…
Read MoreMajor vendors including Cisco, Splunk, Google Cloud and IBM unveiled new security products Monday to kick off RSA Conference 2024. RSAC Hot Products RSA Conference 2024 is just getting underway in San Francisco and, already, an array of new cybersecurity products have been unveiled by major vendors. We’re featuring 10 of the new security tools…
Read MoreRecent Posts
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist
- Here Are The Stellar Startup Edge Computing/IoT Vendors To Know In 2024