Author: nlqip
AI, Azure and security are just some of the biggest topics expected to come up Thursday on the company’s third fiscal quarter earnings call. Updates on Microsoft’s artificial intelligence and Copilot offerings. Growth in the cloud and Azure business. And the tech giant’s position in the ever-competitive security market. These are some of the biggest…
Read MoreCISA released eight Industrial Control Systems (ICS) advisories on April 25, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-24-116-01 Multiple Vulnerabilities in Hitachi Energy RTU500 Series ICSA-24-116-02 Hitachi Energy MACH SCM ICSA-24-116-03 Siemens RUGGEDCOM APE1808 Devices Configured with Palo Alto Networks Virtual NGFW ICSA-24-116-04 Honeywell Experion PKS,…
Read MoreThe new module quantifies the risk of ransomware and data exfiltration for third-party vendors, while combining the signals with first-party and SaaS risk, Safe Security CEO Saket Modi tells CRN. Safe Security is taking a new approach to quantifying third-party cyber risk with the debut of a new tool that represents a “massive” opportunity for…
Read MorePart 7 of CRN’s Big Data 100 takes a look at the startup companies solution providers should know in the big data arena. Big Data, Big Plans The majority of the companies on the CRN 2024 Big Data 100 are either major IT vendors like Amazon Web Services, Microsoft and Oracle, or younger – albeit…
Read More‘You can search incentives by product. You can search for it by country. The partners are absolutely loving that we’re showing how we can make their businesses more transparent, more readily to understand our profitability, by letting them use AI,’ Colleen Kapase, vice president of channels and partner programs at Google Cloud, tells CRN. Google…
Read MoreHackers have started to target a critical severity vulnerability in the WP Automatic plugin for WordPress to create user accounts with administrative privileges and to plant backdoors for long-term access. Currently installed on more than 30,000 websites, WP Automatic lets administrators automate content importing (e.g. text, images, video) from various online sources and publishing on…
Read MoreSecurity researchers have discovered a new Android banking trojan they named Brokewell that can capture every event on the device, from touches and information displayed to text input and the applications the user launches. The malware is delivered through a fake Google Chrome update that is shown while using the web browser. Brokewell is under active development…
Read More‘We are in a race to put AI to work for people. And that’s a race ServiceNow intends to win for our customers,’ says ServiceNow CEO Bill McDermott. AI and generative AI continue to be key drivers of the success story that is ServiceNow. Bill McDermott, CEO of the Santa Clara, Calif.-based digital workflow technology…
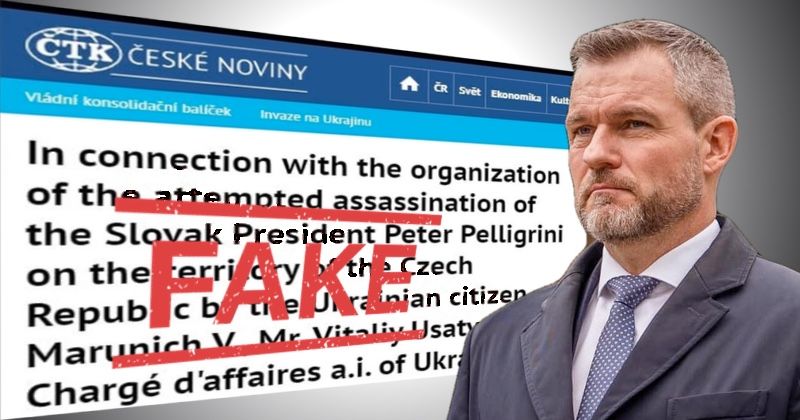
Read MoreCzech news agency ČTK announced on Tuesday that a hacker had managed to break into its systems and published fake news reports of a plot to murder the president of a neighbouring country. One of the false stories published by the hacker in Czech and English claimed that Czechia’s security information service (known as BIS)…
Read More“We believe there will be added demand because a combined portfolio is more interesting,” IBM CEO Arvind Krishna said on an earnings call. IBM executives painted the planned $6.4 billion purchase of cloud infrastructure tools vendor HashiCorp as complementary to multiple business segments – including fellow open-source tools provider Red Hat – even as IBM…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’