Author: nlqip
New Attack on VPNs This attack has been feasible for over two decades: Researchers have devised an attack against nearly all virtual private network applications that forces them to send and receive some or all traffic outside of the encrypted tunnel designed to protect it from snooping or tampering. TunnelVision, as the researchers have named…
Read MoreThis article is covering effects of the people tracking applications over the “telegram-nearby-map” project on GitHub. This open-source project allows users to track the approximate location of other Telegram users within a specified radius, raising significant concerns about privacy and potential misuse. Functionality and Concerns The tool leverages Telegram’s “People Nearby” feature, which allows users…
Read MoreThe funding was led by major names of Silicon Valley venture capital including Andreessen Horowitz and comes after Wiz executives signaled an intensified push with channel partners. Wiz on Tuesday announced $1 billion in new funding at a $12 billion valuation as the four-year-old company sees surging growth in the cloud and AI security markets.…
Read MoreKara Swisher has been covering Silicon Valley since the early days, and she’s made a ton of enemies the old fashioned way (by telling the truth about the new robber barons of our digital lives). In a new memoir called Burn Book, she pulls the curtain back on a world run by powerful babies. Is…
Read MoreUpdates on Lightspeed, OpenShift AI and Red Hat’s partnership with Nvidia are some of the major news made this week at Summit. Lightspeed expansion. Red Hat OpenShift AI enhancements. And deeper partnerships with the likes of Stability AI, Oracle and Nvidia. These are some of the biggest news items from the Raleigh, N.C.-based open source…
Read MoreThe FBI, UK National Crime Agency, and Europol have unveiled sweeping indictments and sanctions against the admin of the LockBit ransomware operation, with the identity of the Russian threat actor being revealed for the first time. According to a new indictment by the US Department of Justice and a press release by the NCA, the LockBit ransomware operator…
Read MoreMay 07, 2024NewsroomVulnerability / Network Security The MITRE Corporation has offered more details into the recently disclosed cyber attack, stating that the first evidence of the intrusion now dates back to December 31, 2023. The attack, which came to light last month, singled out MITRE’s Networked Experimentation, Research, and Virtualization Environment (NERVE) through the exploitation…
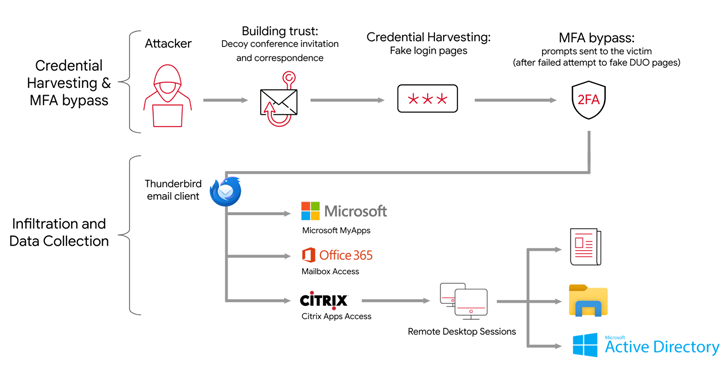
Read MoreThe Iranian state-backed hacking outfit called APT42 is making use of enhanced social engineering schemes to infiltrate target networks and cloud environments. Targets of the attack include Western and Middle Eastern NGOs, media organizations, academia, legal services and activists, Google Cloud subsidiary Mandiant said in a report published last week. “APT42 was observed posing as…
Read MoreAt RSA Conference 2024 this week, vendors are showcasing new products in categories including SASE, security operations and application security — with many touting newly released, GenAI-powered cybersecurity capabilities. Big RSAC Product Announcements Even as the cybersecurity industry continues to maintain its rapid growth pace — leading many vendors to roll out product announcements throughout…
Read MoreThe company said the acquisition of Noname Security will allow Akamai to ‘extend protection across all API traffic locations.’ Akamai Technologies on Tuesday announced a deal to acquire API security firm Noname Security for $450 million. The company said the acquisition of Noname will allow Akamai to “extend protection across all API traffic locations.” [Related:…
Read MoreRecent Posts
- Five HPE GreenLake Game Changers: A Look At Pay-Per-Use Cloud Service Improvements
- Multiple Vulnerabilities in Adobe Products Could Allow for Arbitrary Code Execution
- Critical Patches Issued for Microsoft Products, January 14, 2025
- CISA Releases Four Industrial Control Systems Advisories | CISA
- Ivanti Releases Security Updates for Multiple Products | CISA