Author: nlqip
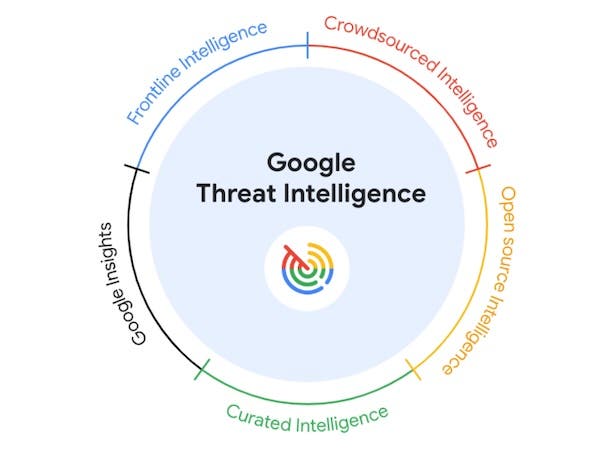
Launched at RSAC 2024, the new Google Threat Intelligence offering provides faster protection against threats by combining insights from Mandiant, VirusTotal and Google with GenAI-powered capabilities, the company says. Google Cloud announced a new cybersecurity offering Monday that represents a major advancement by making threat intelligence more automated and “more actionable,” an executive told CRN.…
Read More‘EQT shares our vision for the future as we transform how the world’s biggest brands connect with customers,’ says Perficient CEO Tom Hogan. Global channel consultant Perficient is being acquired by private equity firm EQT AB for approximately $3 billion in a move its CEO says is a win for shareholders as Perficient’s stock jumped…
Read More‘We were a little weak, if I may, on the Azure side. CCT has a lot of customers and a lot of know-how on Azure implementation and expansion of services around IaaS. That’s something we are looking into expanding with CCT,’ says ISSQUARED CEO and Founder Bala Ramaiah. IT and cybersecurity MSP ISSQUARED Monday said…
Read MoreHere’s the exact global cloud market share figures for AWS, Alibaba, Google Cloud, Microsoft and Salesforce for first quarter 2024 as the market increased to $76 billion. The three largest cloud companies on the planet—Amazon Web Services, Microsoft and Google Cloud—continued to battle for global cloud market share leadership during the first quarter of 2024,…
Read MoreMajor vendors including Cisco, Splunk, Google Cloud and IBM unveiled new security products Monday to kick off RSA Conference 2024. RSAC Hot Products RSA Conference 2024 is just getting underway in San Francisco and, already, an array of new cybersecurity products have been unveiled by major vendors. We’re featuring 10 of the new security tools…
Read MoreRussia was involved in a months-long cyber espionage campaign against Germany last year, which involved targeting politicians and the defense sector, German officials said, adding they have evidence the attacks were conducted by Russia-backed threat actor, Fancy Bear. Also tracked as APT28, Fancy Bear is a state-sponsored hacker group linked to the Russian GRU intelligence service…
Read MoreCybercriminals are vipers. They’re like snakes in the grass, hiding behind their keyboards, waiting to strike. And if you’re a small- and medium-sized business (SMB), your organization is the ideal lair for these serpents to slither into. With cybercriminals becoming more sophisticated, SMBs like you must do more to protect themselves. But at what price?…
Read MoreNew Lawsuit Attempting to Make Adversarial Interoperability Legal Lots of complicated details here: too many for me to summarize well. It involves an obscure Section 230 provision—and an even more obscure typo. Read this. Tags: copyright, courts Posted on May 6, 2024 at 7:03 AM • 0 Comments Sidebar photo of Bruce Schneier by Joe…
Read MoreMay 06, 2024NewsroomAndroid / Data Security Multiple security vulnerabilities have been disclosed in various applications and system components within Xiaomi devices running Android. “The vulnerabilities in Xiaomi led to access to arbitrary activities, receivers and services with system privileges, theft of arbitrary files with system privileges, [and] disclosure of phone, settings and Xiaomi account data,”…
Read MoreMay 06, 2024NewsroomSpyware / Malware Cybersecurity researchers have discovered a new information stealer targeting Apple macOS systems that’s designed to set up persistence on the infected hosts and act as a spyware. Dubbed Cuckoo by Kandji, the malware is a universal Mach-O binary that’s capable of running on both Intel- and Arm-based Macs. The exact…
Read MoreRecent Posts
- Solution Providers Rally For Employees, Customers Amid LA Area Wildfires
- VMware-Broadcom Partners Weigh In On New Channel Chief’s Vision And Strategy
- Qualcomm Hires Intel Xeon Chief Architect Amid Server CPU Plans
- Vulnerability Summary for the Week of January 6, 2025 | CISA
- How Hackers Steal Your Password