Author: nlqip
Finland’s Transport and Communications Agency (Traficom) is warning about an ongoing Android malware campaign attempting to breach online bank accounts. The agency has highlighted multiple cases of SMS messages written in Finnish that instruct recipients to call a number. The scammer who answers the call instructs victims to install a McAfee app for protection. The…
Read MoreVideo Organizations that fall victim to a ransomware attack are often caught between a rock and a hard place, grappling with the dilemma of whether to pay up or not 03 May 2024 The Simone Veil hospital in Cannes, France – which fell victim to a disruptive ransomware attack two weeks ago – has announced…
Read MoreImage: Midjourney A Mullvad VPN user has discovered that Android devices leak DNS queries when switching VPN servers even though the “Always-on VPN” feature was enabled with the “Block connections without VPN” option. “Always-on VPN” is designed to start the VPN service when the device boots and keep it running while the device or profile is on. Enabling the…
Read MoreThe Iranian state-backed threat actor tracked as APT42 is employing social engineering attacks, including posing as journalists, to breach corporate networks and cloud environments of Western and Middle Eastern targets. APT42 was first documented by Mandiant in September 2022, who reported that the threat actors were active since 2015, having carried out at least 30 operations in…
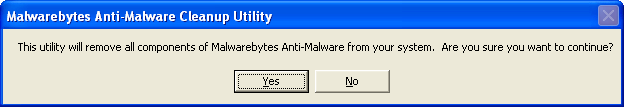
Read MoreScreenshots for Malwarebytes Anti-Malware Cleanup Tool BleepingComputer Review: The Malwarebytes Anti-Malware Cleanup Tool allows you to completely uninstall Malwarebytes Anti-Malware in the event that you are unable to uninstall it properly from the Windows control panel. When this tool runs it will search your computer for installations of Malwarebytes Anti-Malware and remove it from your…
Read MoreCzechia and Germany on Friday revealed that they were the target of a long-term cyber espionage campaign conducted by the Russia-linked nation-state actor known as APT28, drawing condemnation from the European Union (E.U.), the North Atlantic Treaty Organization (NATO), the U.K., and the U.S. The Czech Republic’s Ministry of Foreign Affairs (MFA), in a statement,…
Read MoreDropbox, a popular cloud storage and collaboration platform, recently disclosed a security breach impacting its eSignature service,Dropbox Sign. On May 2, 2024, the company revealed that hackers successfully infiltrated the platform, gaining access to sensitive customer information. The stolen data includes customer emails, usernames, phone numbers, and hashed passwords. Additionally, the attackers managed to exfiltrate…
Read MoreScams Once your crypto has been stolen, it is extremely difficult to get back – be wary of fake promises to retrieve your funds and learn how to avoid becoming a victim twice over 02 May 2024 • , 4 min. read It’s a nightmare scenario for any cryptocurrency user. You fall victim to a…
Read MoreImage: Midjourney A Mullvad VPN user has discovered that Android devices leak DNS queries when switching VPN servers even though the “Always-on VPN” feature was enabled with the “Block connections without VPN” option. “Always-on VPN” is designed to start the VPN service when the device boots and keep it running while the device or profile is on. Enabling the…
Read MoreFriday Squid Blogging: Squid Purses Squid-shaped purses for sale. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here. Tags: squid Posted on May 3, 2024 at 5:05 PM • 0 Comments Sidebar photo of Bruce Schneier…
Read MoreRecent Posts
- CISA Releases Four Industrial Control Systems Advisories | CISA
- CISA and US and International Partners Publish Guidance on Priority Considerations in Product Selection for OT Owners and Operators | CISA
- Broadcom Names New Channel Chief, Sales Leader: 5 Big Things To Know
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.