Author: nlqip
A new Rust-based version of the Qilin (Agenda) ransomware strain, dubbed ‘Qilin.B,’ has been spotted in attacks, featuring stronger encryption, better evasion from security tools, and the ability to disrupt data recovery mechanisms. Qilin.B was spotted by security researchers at Halcyon, who warned about the threat and shared indicators of compromise to help with early…
Read MoreCISA released four Industrial Control Systems (ICS) advisories on October 24, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. CISA encourages users and administrators to review newly released ICS advisories for technical details and mitigations. Source link lol
Read MoreIterate.ai’s Generate application is part of a new SMB App Pack that Intel is bundling with AI PCs for channel partners to sell, and it has partnered with TD Synnex to handle distribution for the application, which the company says is only the beginning of its channel ambitions. An Intel ISV partner said it’s going…
Read MoreA new Fortinet FortiManager flaw dubbed “FortiJump” and tracked as CVE-2024-47575 has been exploited since June 2024 in zero-day attacks on over 50 servers, according to a new report by Mandiant. For the past ten days, rumors of an actively exploited FortiManager zero-day have been circulating online after Fortinet privately notified customers in an advanced…
Read MoreCISA, US, and International Partners Release Joint Guidance to Assist Software Manufacturers with Safe Software Deployment Processes | CISA
by nlqip
Today, CISA—along with U.S. and international partners—released joint guidance, Safe Software Deployment: How Software Manufacturers Can Ensure Reliability for Customers. This guide aids software manufacturers in establishing secure software deployment processes to help ensure software is reliable and safe for customers. Additionally, it offers guidance on how to deploy in an efficient manner as part of…
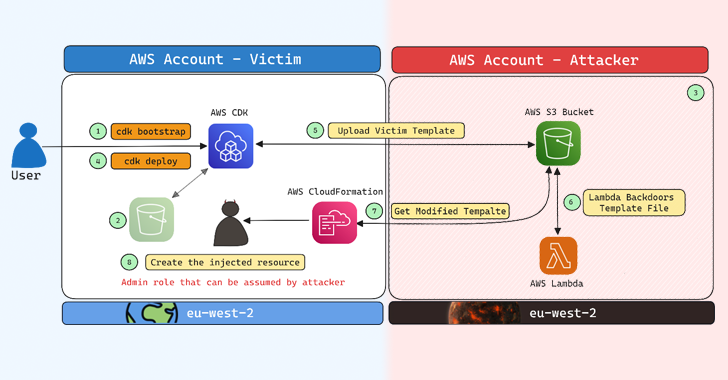
Read MoreCybersecurity researchers have disclosed a security flaw impacting Amazon Web Services (AWS) Cloud Development Kit (CDK) that could have resulted in an account takeover under specific circumstances. “The impact of this issue could, in certain scenarios, allow an attacker to gain administrative access to a target AWS account, resulting in a full account takeover,” Aqua…
Read MoreOn the second day of Pwn2Own Ireland 2024, competing white hat hackers showcased an impressive 51 zero-day vulnerabilities, earning a total of $358,625 in cash prizes. Pwn2Own is a hacking contest where security researchers compete to exploit software and mobile hardware devices to earn the coveted title of “Master of Pwn” and $1,000,000 in cash…
Read MoreThe vulnerability—which has been exploited in attacks compromising more than 50 FortiManager devices, according to Mandiant researchers—was disclosed by Fortinet Wednesday. A critical-severity FortiManager vulnerability publicly disclosed by Fortinet this week has been exploited in attacks dating back to late June, according to Mandiant researchers. The attacks exploiting the flaw (tracked at CVE-2024-47575) has compromised…
Read MoreOct 24, 2024Ravie LakshmananVulnerability / Network Security Cisco on Wednesday said it has released updates to address an actively exploited security flaw in its Adaptive Security Appliance (ASA) that could lead to a denial-of-service (DoS) condition. The vulnerability, tracked as CVE-2024-20481 (CVSS score: 5.8), affects the Remote Access VPN (RAVPN) service of Cisco ASA and…
Read MoreLatrodectus is a Windows malware downloader first detected in October 2023 that functions as a backdoor. The malware downloads executable and DLL payloads. Latrodectus can also execute commands. Threat actors are increasingly using Latrodectus malware to target businesses in the financial, automotive, and healthcare sectors. Latrodectus primarily spreads through phishing emails containing malicious attachments disguised…
Read MoreRecent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day