Author: nlqip
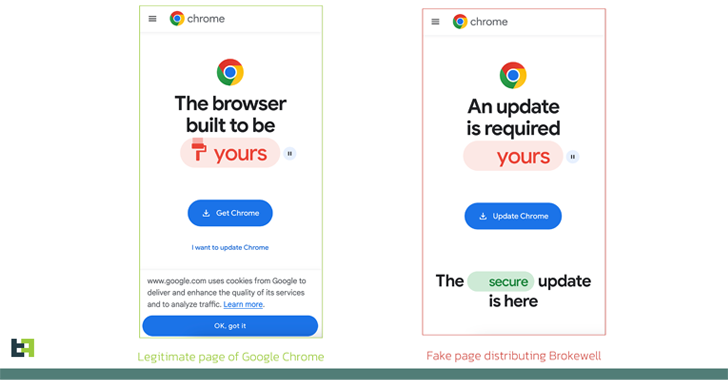
Apr 26, 2024NewsroomMobile Security / Cybercrime Fake browser updates are being used to push a previously undocumented Android malware called Brokewell. “Brokewell is a typical modern banking malware equipped with both data-stealing and remote-control capabilities built into the malware,” Dutch security firm ThreatFabric said in an analysis published Thursday. The malware is said to be…
Read MoreIn today’s digital world, where connectivity is rules all, endpoints serve as the gateway to a business’s digital kingdom. And because of this, endpoints are one of hackers’ favorite targets. According to the IDC, 70% of successful breaches start at the endpoint. Unprotected endpoints provide vulnerable entry points to launch devastating cyberattacks. With IT teams…
Read MoreThe Los Angeles County Department of Health Services disclosed a data breach after thousands of patients’ personal and health information was exposed in a data breach resulting from a recent phishing attack impacting over two dozen employees. This integrated health system operates the public hospitals and clinics in L.A. County (the most populous county in…
Read MoreHealthcare service provider Kaiser Permanente disclosed a data security incident that may impact 13.4 million people in the United States. Kaiser Permanente is an integrated managed care consortium and one of the largest nonprofit health plans in the U.S. It operates 40 hospitals and 618 medical facilities in California, Colorado, the District of Columbia, Georgia, Hawaii, Maryland,…
Read MoreA recent cyberattack on a wastewater treatment plant in Tipton, Indiana, has been claimed by the Cyber Army of Russia Reborn (CARR), a Russian-speaking hacker group. The incident spotlights the ongoing vulnerability of critical infrastructure in smaller communities, even as the plant itself reportedly experienced minimal disruption. CARR has previously been linked to similar cyberattacks…
Read MoreState of Kansas names John Godfrey as CISO John Godfrey has become the new chief information security officer for the State of Kansas, following the appointment of former CISO Jeff Maxon to Chief Information Technology Officer for Kansas. Godfrey will lead the Kansas Information Security Office in developing and implementing information security strategies, including cybersecurity…
Read MoreDutch semiconductor manufacturer Nexperia has suffered a significant data breach, exposing sensitive information, including intellectual property. The company’s servers were compromised, prompting Nexperia to take them offline and launch a full-scale investigation. The extent of the damage remains unclear, and Nexperia hasn’t confirmed whether the attackers demanded ransom. However, the hacking group Dunghill has claimed…
Read MoreApr 26, 2024NewsroomThreat Intelligence / Cyber Attack Threat actors are attempting to actively exploit a critical security flaw in the WP‑Automatic plugin for WordPress that could allow site takeovers. The shortcoming, tracked as CVE-2024-27956, carries a CVSS score of 9.9 out of a maximum of 10. It impacts all versions of the plugin prior to…
Read MoreIn 2022, we published an article discussing the rise in targeted cyberattacks on managed service providers (MSPs), which included warnings from the Five Eyes intelligence alliance. Nearly two years later, it has become evident that these warnings were well-founded, as attacks on MSPs now occur on a regular basis. In this article, we will explore…
Read MoreFrequently asked questions about CVE-2024-20353 and CVE-2024-20359, two vulnerabilities associated with “ArcaneDoor,” the espionage-related campaign targeting Cisco Adaptive Security Appliances. Background The Tenable Security Response Team has compiled this blog to answer Frequently Asked Questions (FAQ) regarding an espionage campaign called ArcaneDoor. FAQ What is ArcaneDoor? ArcaneDoor is the name given to an espionage-focused campaign…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm